A remote workforce needs ongoing training in order to successfully identify and report phishing and other types of cyber attacks. With so many employees based at home due to COVID-19, it’s more important than ever to create a strong culture of security and ensure both the informational awareness and genuine engagement of all members of your team.
Spear phishing attacks, in particular, have been a popular technique used by threat actors during the COVID-19 pandemic to trick and infect victims. Here are some tips for keeping employees aware of the threat – and on top of the game
How to Detect Spear Phishing Emails
CyberProof has gathered important precautionary tips on how employees can detect Spear Phishing emails when working remotely:
- Look for incorrect spelling and bad grammar. Professional companies or organizations usually have an editorial staff to ensure customers get high-quality professional content. If an official email message is fraught with errors, it is likely to be a scam. Moreover, free offers may hide malicious attacks. Particularly during the coronavirus pandemic, free offers are being advertised. But sometimes a “Unique Opportunity” is covering up a cyber attack, so if an offer has spelling errors, be cautious.
-
Do not click on links or download files from an unknown sender. Spear Phishing emails usually contain strange links, i.e., the actual address is most likely different from the common links that employees are used to seeing. We recommend being extra-cautious and consistently checking the legitimacy of links. One method for doing that is to hover the mouse over the link without clicking it and see if the address matches what was typed in the message.
-
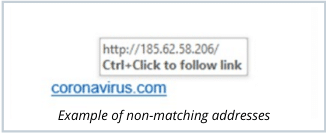
Pay attention to slightly altered web addresses. This is another type of spoofing method: a threat actor makes slight alterations to a web address so that it closely resembles the name of a legitimate company.
-
When it comes to attachments – take special care. Attackers may use multiple techniques to try and trick recipients into trusting that an attached file is legitimate. When in doubt, contact the sender and ask them to confirm the legitimacy of the email and attachment. Apart from not clicking on, or downloading attachments from unknown senders:
-
Do not trust logos used in attachments: A threat actor can attach a malicious link to a company’s legitimate logo or icon, and trick the target into clicking on it; by hovering over the logo, you can see the URL before clicking on it.
-
Be wary of multiple file extensions: pdf.exe, rar.exe, txt.hta, etc.
-
- Stay away from panic inducing messages. As part of Spear Phishing email campaigns, hackers often attempt to create a sense of panic in order to get their victims to respond quickly. In these cases, the threat actor is most likely trying to extort you. Generally, this kind of email will include instructions about how to make a payment. If you received an email with a tone of extortion, do not follow the sender’s instructions; they are basically just trying their luck.
As part of Spear Phishing email campaigns, hackers often attempt to create a sense of panic in order to get their victims to respond quickly.
-
If a vendor contacts you “out of the blue” – be wary of an account takeover. The fact that you have an ongoing work relationship with the individual who sent you an email does not necessarily mean the email is safe. Sometimes, a threat actor will take over the email account of a known vendor. Be especially suspicious if you receive an email that is the continuation of an old, dated thread. If the timing is strange – and it seems unusual that the vendor is contacting you now – this might be indicative of an account takeover.
What Security Teams Can Do to Reduce Risk
-
Provide weekly updates about new trends. Send a weekly company update about new phishing attempts and trends that are gaining traction. This information should be shared with all employees. You can find information about the latest attacks on CyberProof’s Threat Alerts.
-
Conduct monthly training. In addition to general awareness CISOs should share recent threats detected in the company’s security filters so that employees know what’s been going on at the security level. While some information may need to be kept confidential, CISOs can use relevant findings as an educational opportunity – by letting people know the source of the vulnerability, and explaining what employees should do in order to thwart future attacks.
-
Implement known Indicators of Compromise (IoCs). While threat actors are attempting to capitalize on the COVID-19 crisis, they are using some of the same tactics they always do. Be especially vigilant now to take steps to protect your organization from today’s, and future threats. We highly recommend implementing known IoCs in your security systems.
-
Make it easier for employees to report concerns. Streamline work from home processes for employees to let your security operation team know about suspicious emails. The goal is to train employees to act as an extension of the security team. Make the reporting process easy and intuitive.
Streamline work from home processes for employees to let your security operation team know about suspicious emails
- Make security less about work, and more about family. With employees working from home, caution and safety online promotes the protection of home and family, not just the office. Send out security updates that are “marketed” more as a matter of personal importance, and provide easy-to-use resources such as training modules that allow employees to quickly get up to speed.
If you would like to speak to a CyberProof expert about protecting your organization from spear phishing attacks and other cyber threats, contact us today.