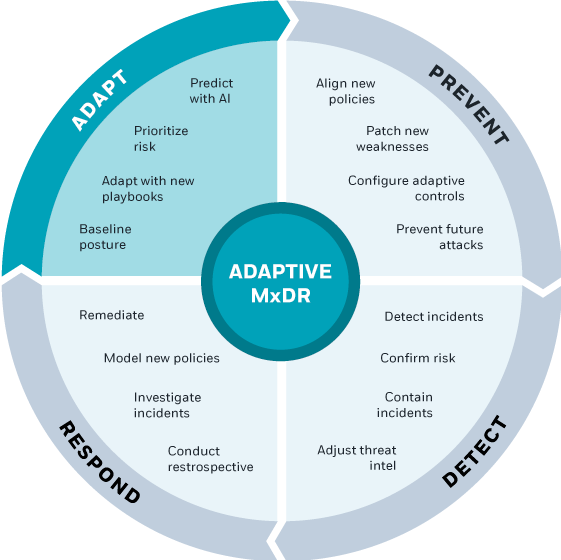
Adaptive Managed xDR (MxDR) – Powered by Google
CyberProof’s Adaptive MxDR service – powered by Google Chronicle Security, provides powerful detection and response capabilities to prevent increasingly sophisticated attacks. Leveraging AI and automation through a cloud-first security delivery model, CyberProof’s Adaptive MxDR service helps prevent increasingly sophisticated attacks while minimizing Mean-Time-To-Detect (MTTD) and Mean-Time-To-Response (MTTR) benchmarks.
RECOGNIZED AS INDUSTRY LEADERS
AI & Automation
Leveraging AI and automation through SOAR to orchestrate threat respons
Reduced Incident Response Time
with orchestration and automation capabilities that provide faster time to response and increased threat landscape visibility

Adaptive Security
AI assisted and adaptive response playbooks tailored for evolving Realtime threats
Case Study
How HealthProof went from 3 SOCs and 3 SIEMs to a single global SOC with CyberProof
From ViVE 2025, watch Hans Guilbeaux, CIO of UST HealthProof, share how his team partnered with CyberProof and Google Cloud Security to leverage cloud-enabled security operations, elevating their cybersecurity posture and streamlining incident response.
REDUCING THE IMPACT OF ATTACKS
Uncover Threats Faster with Cloud-Native SecOps
CyberProof’s use of Chronicle’s modern, cloud native SecOps platform provides a combination of Google’s hyper-scale infrastructure along with unparalleled visibility and understanding of cyber adversaries to provide our CyberProof SOC teams with curated outcomes that proactively uncover the latest threats in near real-time, and enable them to detect, investigate and respond with speed and precision.

Google scale and speed
Eliminate security blind spots by ingesting, normalizing, analyzing and searching all security telemetry at Google scale and speed.

Applied threat intelligence
Proactively uncover and defend against novel attacks in near real-time without extensive custom engineering. Curated outcomes apply Google’s vast threat and exposure visibility to your unique environment.
AI-infused productivity
Elevating the CyberProof SOC team’s talent and productivity with a unified platform infused with generative AI and expert help when needed, during and after an incident.
Adaptive Use Case Management
Adapt to new threats with CyberProof’s agile use case framework, to evolve response playbooks as new incidents are detected.

Cloud First Security
Build a security stack that is native to Google cloud, leverage scale, agility and other cloud security capabilities e.g. SOAR, SIEM.

Threat Hunting
Utilize insights from CyberProof’s threat intelligence to define threat hunting hypotheses, based on incidents of attacks (IOA)







Speak with an expert
Discover how we can help you with Managed XDR in an open and honest conversation with one of our cybersecurity experts
RESOURCES
Learn more about managed XDR
Frequently asked questions
What is MXDR? (Managed Extended Detection and Response)
MXDR, a managed unified security incident platform, utilizes AI and automation to detect, respond to, and investigate advanced cyberattacks. Unlike targeted systems like Endpoint Detection and Response (EDR) or Managed Detection and Response (MDR), MXDR broadens its coverage across multiple enterprise security categories, offering a comprehensive defense against sophisticated cyber threats. MXDR integrates detection, investigation, and response capabilities across various domains, including endpoints (such as laptops, servers, and workstations), hybrid identities (like user accounts and access management), cloud applications and workloads, email, data stores, and telemetry from other sources. Additionally, MXDR offers native integration with third-party solutions. Key capabilities include incident-based investigation, where XDR correlates low-level alerts into comprehensive incidents, automatic disruption of advanced attacks by detecting ongoing attacks and initiating response actions like isolating compromised devices, and cyberattack chain visibility, providing a complete view of complex attack chains by ingesting alerts from diverse sources.
What’s the difference between XDR and MXDR?
MXDR is a hosted and managed XDR service by a provider, leveraging their own SecOps teams, operating 24/7 support across multiple Security Operations Centers (SOC), worldwide.
What’s the difference between EDR and MXDR?
EDR (Endpoint Detection and Response) is a technology that protects endpoints such as servers, workstations, mobiles and IoT devices from cyber threats. EDR comprises prevention, detection, and response controls that can be used by security analysts to get deep visibility of malicious behavior at the endpoint and contain it quickly before it spreads throughout the network. On the other hand, MXDR is widely considered an evolution of EDR, providing managed and extended visibility of high-fidelity alerts beyond the endpoint to applications, identities, cloud, and network domains.