Authors: Niranjan Jayanand, Venkatesh Bolla, Golan Agi
Executive Summary
On January 13, 2025, Horizon AI disclosed three critical vulnerabilities that could compromise both SimpleHelp server and client machines. SimpleHelp quickly patched these vulnerabilities in January and urged organizations to quickly update to the latest versions.
CyberProof Threat Hunters assess with medium confidence that different cybercriminal groups and some ransomware groups are likely abusing these vulnerabilities in the wild. Attacks so far reported and researched, are likely through connecting to endpoints running vulnerable versions of SimpleHelp Remote Monitoring & Management (RMM) Client.
The CyberProof Threat Research Team details on how they tracked the vulnerability to study any potential abuse and shares a hunting query that can be used for the initial stage of hunting to help organizations check for post-exploitation events of SimpleHelp’s RMM software.
Technical Details
Since the COVID outbreak, attackers have progressively focused on RMM tools, exploiting the prevalence of the hybrid work model. In almost every attack, remote access software (RMM) may be installed and used post-compromise as an alternate communications channel for redundant access or as a way to establish an interactive remote desktop session with the target system.
Attackers have increasingly targeted RMM tools, taking advantage of the widespread hybrid work model. Below are some of the top targeted RMM vulnerabilities in 2024.
- CVE-2024-1708 and CVE-2024-1709: Affecting ConnectWise ScreenConnect.
- CVE-2024-12356 and CVE-2024-12686: Affecting BeyondTrust products.
- CVE-2024-12754: A privilege escalation vulnerability stemming from an arbitrary file read/copy operation performed by the AnyDesk service as NT AUTHORITY\SYSTEM. This flaw allows an attacker to manipulate the file-copying process to overwrite system-critical files while retaining original ownership and permissions.
Early January, Horizon3 disclosed reporting SimpleHelp RMM vulnerabilities targeted CVE-2024-57726, CVE-2024-57727, and CVE-2024-57728 that pose risks from attackers ranging from escalating privileges to downloading or uploading arbitrary files.
The stats below, from Shadow Server, shows the prevalence of vulnerable versions of SimpleRMM globally.
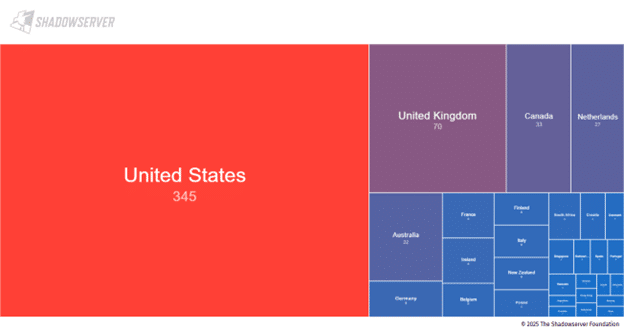
Source: ShadowServer
What to Look For
Different cyber-criminal groups including human-operated ransomware groups are well known to abuse inbuilt applications and trusted tools throughout different stages of the attack kill chain. Your Threat Hunting Team should look for context around the following events to distinguish the unknown from the known:
- Check for lateral movements through WMI, PSExec, etc
- Check for reconnaissance through execution of ipconfig, net.exe, netstat.exe etc.
- Watch out for new user account creation.
- Check for post compromise tools dropped and executed – like Impacket, Sliver, Mimikatz, CobaltStrike, BloodHound, ngrok etc.
- Check for defense evasion techniques like disabling security services (example: Microsoft Defender), process injection in the context of benign processes, scanning across the environment for vulnerable drivers etc.
- Check for deployment and execution of malicious files to several endpoints through WMI, PDQDeployRunner etc.
- Check for data exfiltration through tools like RClone, RustDesk, etc.
Hunting Query
CyberProof Researchers have made available a hunting query that can be used for the initial assessment stage to help organizations check for post-exploitation events of SimpleHelp’s Remote Monitoring & Management (RMM) software. The query below is only shared to help initiate a review of possible suspicious child processes launched from the RMM process.

Our teams have tested SimpleHelp RMM vulnerability against the query for the post compromise TTP (Hands-on keyboard commands execution). Please see the results below:
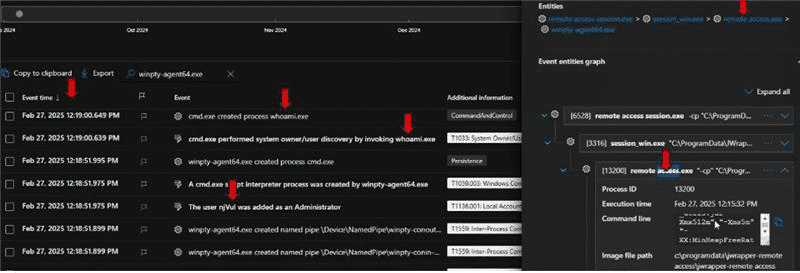
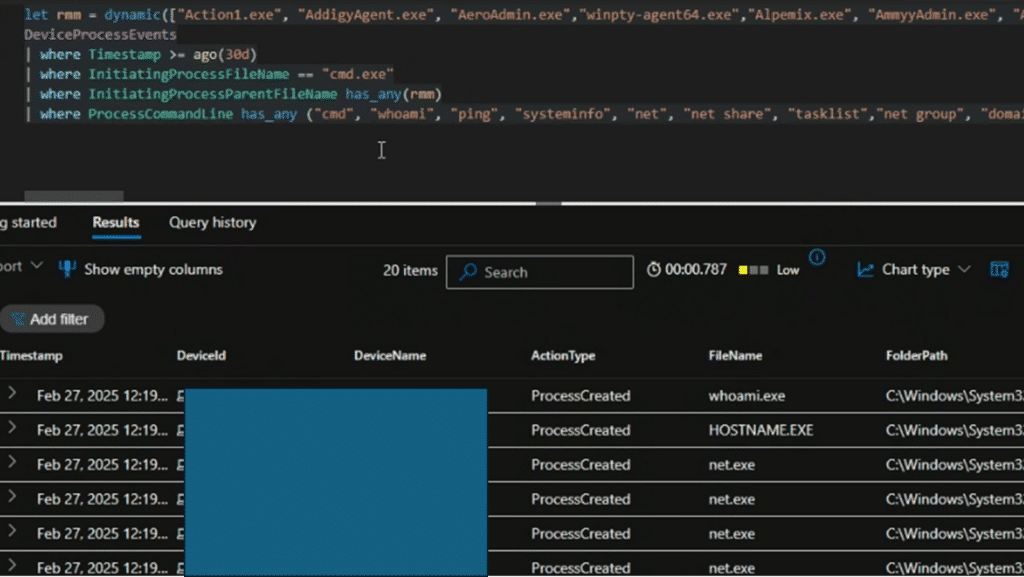
Recommendation
- SimpleHelp strongly advises users to update to the latest version as recommended in their advisory for Security Vulnerabilities in SimpleHelp 5.5.7 and earlier:
- SimpleHelp v5.5 Users – SimpleHelp v5.5.8 and later versions resolve these vulnerabilities. The latest release is available on the SimpleHelp Download Page.
- SimpleHelp v5.4 Users – A patch for SimpleHelp v5.4.10 is now available.
- SimpleHelp v5.3 Users – A patch for SimpleHelp v5.3.9 is now available.
- Uninstall unused and unauthorized SimpleHelp RMM instances from the network.
- Restrict the use of SimpleHelp or any RMM with the network to admins and authorized users only.
- Work closely with threat intelligence and detection engineering teams to enrich hunting queries to stay ahead of early-stage targeted and opportunistic attacks.
How CyberProof Can Help
As cyber threats continue to evolve, so too must the strategies and technologies used to combat them. Threat detection is a critical component of any organization’s cybersecurity strategy. Learn how CyberProof can help your organization effectively detect and respond to cyber threats.













