Contributors: Jacob James, Niranjan Jayanand, Madhuri Syamakala
This blog is part of a (2) part series around our research finding on the ConnectWise ScreenConnect Attacks.
You can catch up on our latest findings here – ConnectWise ScreenConnect Attacks (Part 2): IRS Themed Attacks
Executive Summary
On February 13, 2024, an independent researcher ethically and responsibly reported a potential critical ConnectWise ScreenConnect™ vulnerability [versions 23.9.7 and prior] using the ConnectWise vulnerability disclosure program through the ConnectWise Trust Center.
On May 2025, CyberProof Analysts and Threat Hunters spotted multiple ConnectWise ScreenConnect signed malicious droppers (likely CHAINVERB backdoor tied to UNC5952 UNC5952 threat group) abuses in the wild targeting global financial organizations through emails using invoice theme. CHAINVERB is a downloader that abuses digital signatures in Windows executables. Our investigations saw a surge in usage of .top or dns.net TLD [Top level domains] in multiple eCrime campaigns in recent months.
On 28 May 2025, ConnectWise shared a security event advisory stating possible breach by a nation stage threat group which is currently being investigated by Mandiant.
We are continuing to learn if our observations are tied to this attack and shall post more information if we find more interesting observations in coming weeks. The surge in attackers abusing RMM tools in almost every other attack are not declining and we continue to advocate the importance of organizations to adopt best practices for Threat Hunting to spot unknown abuse in environments.
Technical Details
During recent MDR incidents, we saw a surge in malicious Screenconnect droppers served through emails using invoice themes leading to CHAINVERB downloader. CHAINVERB utilizes an embedded command-and-control (C2 or C&C) URL, hidden within the digital certificate, to download and execute its next-stage payload. CHAINVERB has been observed deploying the ConnectWise Control (formerly ScreenConnect) remote access tool on infected systems.
We access this campaign with medium confidence to UNC5952, a financially motivated threat group that conducts socially engineered financial transaction operations. The group heavily relies on social engineering tricks to lure users to visit their command-and-control infrastructure. The recent downloaders were digitally signed and were seen using file names associated to signed documents, adobe reader, invoice [NotaFiscal refers to Brazilian invoice or tax receipt], Zoominstaller etc. Once the user is tricked, it leads to the installation of ScreenConnect (aka Connectwise) and initiates remote desktop sessions to attacker command and control. This can further lead the attacker to conduct internal host reconnaissance and capturing screenshots during access.
Delivering the Malicious Installer
First case using anondns.net as TLD:
CyberProof MDR analyst spotted a phishing email from sender “russ@oshlaw.com” with malicious PDF attachment with a malicious URL [https[:]//visionary-clafoutis-308e89[.]netlify[.]app/] in the email body that served “Download.exe”.
- MD5: a01a80d8c1f665eda5a81391a1ed0024
- SHA-1: b1568b6001450646e2526f6836ca77cb8b3fc7e0
- SHA-256: d6d75807c23ebfb34eceaa10037f2a911dd50128135cb968811c50b0f1d69eea
This file was signed by “ConnectWise” as shown below.
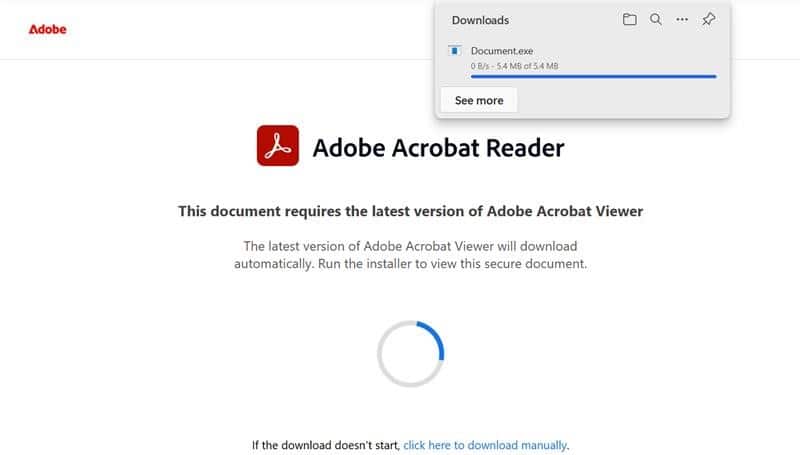
Fig: Malicious url in the email leading to download of Document.exe
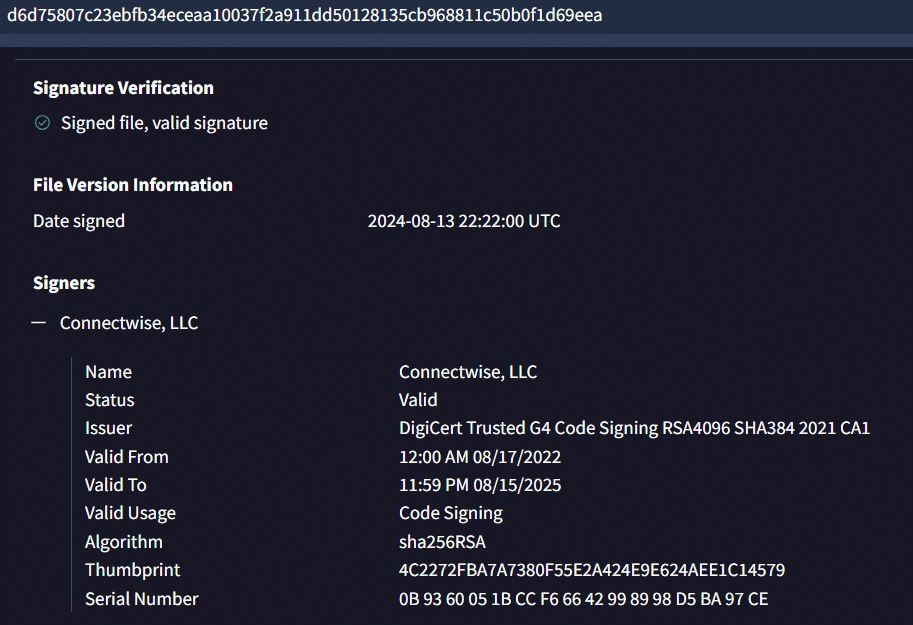
Fig: File is digitally signed by Connectwise, LLC
Below image shows the C2 [kasin22.anondns.net] of this CHAINVERB binary:
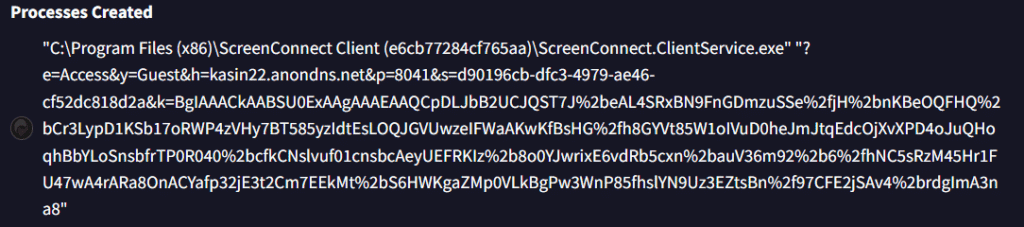
Second case using .top TLD:
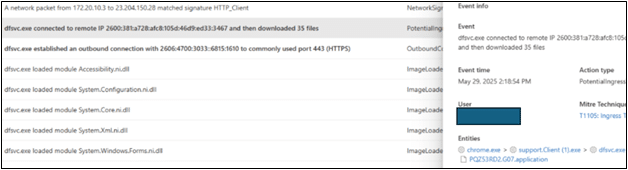
Below is an event seen from our telemetry where another malcious dropper was seen using ‘yertoje.uzhelp.top’ as command and control:

Further investigations led to collection of possible related IOCs, one is a malicious webpage [www.helpw8.top] impersonating customer support leading to download and execution of malicious dropper using file name Support.Client (1).exe.
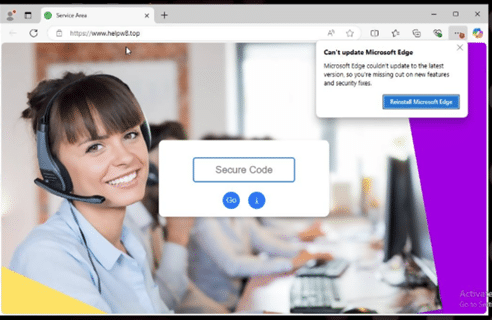
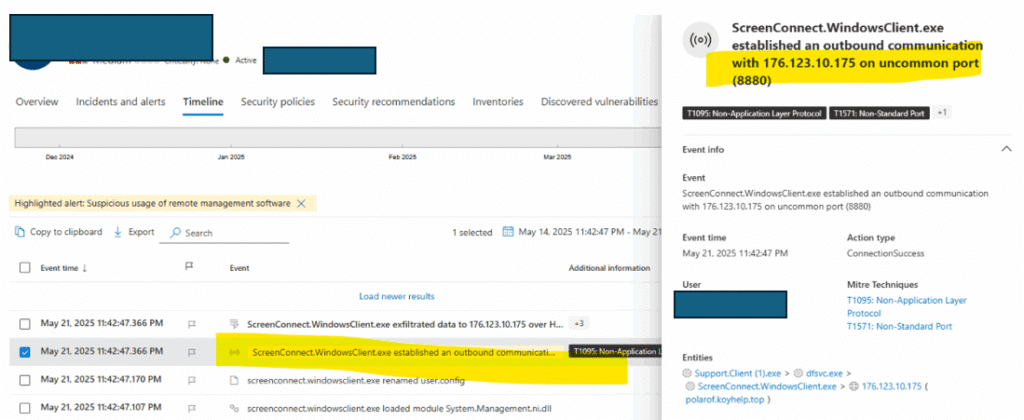
On execution, the sample was seen connecting to remote IP 176.123.10.175.

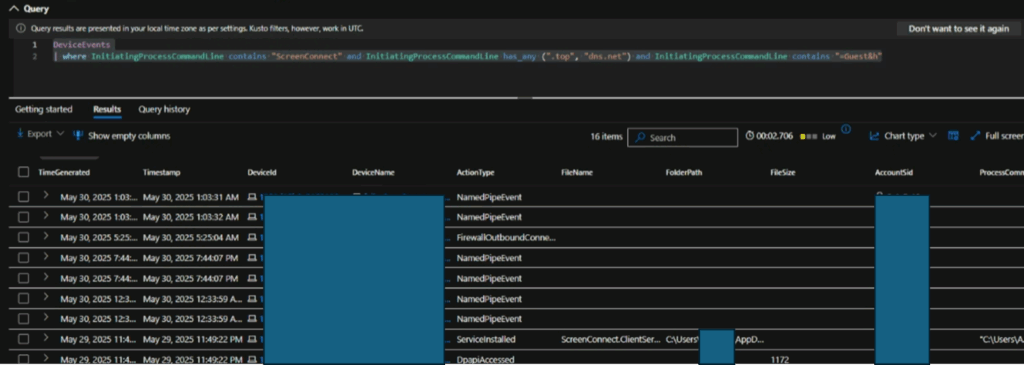
Hunting Query for Detecting CHAINVERB backdoor
This section shares a quick hunting query to detect CHAINVERB

Upgrade ScreenConnect to a patched version immediately:
1. To upgrade to version 23.9.8 or later, please note there is a specific upgrade path that must be followed: 2.1 → 2.5 → 3.1 → 4.4 → 5.4 → 19.2 → 22.8 → 23.3 → 23.9.8+
2. If you are not on maintenance and upgrading to 22.4.20001 (or your latest eligible version), please follow this specified upgrade path: 2.1 → 2.5 → 3.1 → 4.4 → 5.4 → 19.2 → 22.4.20001
For instructions on how to upgrade your on-premise installation, click here.
Mitigations per CISA Advisory Against Malicious Use of RMM Software
The authoring organizations encourage network defenders to:
- Implement best practices to block phishing emails. See CISA’s Phishing Infographic for more information.
- Audit remote access tools on your network to identify currently used and/or authorized RMM software.
- Review logs for execution of RMM software to detect abnormal use of programs running as a portable executable.
- Use security software to detect instances of RMM software only being loaded in memory.
- Implement application controls to manage and control execution of software, including allowlisting RMM programs.
- See NSA Cybersecurity Information sheet Enforce Signed Software Execution Policies.
- Application controls should prevent both installation and execution of portable versions of unauthorized RMM software.
- Require authorized RMM solutions only be used from within your network over approved remote access solutions, such as virtual private networks (VPNs) or virtual desktop interfaces (VDIs).
- Block both inbound and outbound connections on common RMM ports and protocols at the network perimeter.
- Implement a user training program and phishing exercises to raise awareness among users about the risks of visiting suspicious websites, clicking on suspicious links, and opening suspicious attachments. Reinforce the appropriate user response to phishing and spearphishing emails.
Indicators of Compromise
- polarof[.]koyhelp[.]top
- www[.]v4shelp[.]top
- helpw8[.]top
- yertoje[.]uzhelp[.]top
- web[.]bcqhelp[.]top
- web[.]mryhelp[.]top
- B552a9a824d10d0b8385005cba442544
- a01a80d8c1f665eda5a81391a1ed0024
- 180f9294e3e2418a460dee6d9e40291a
- f2ba4c8023add555f68732460dc9d4c7
- cc9b850b23700158b2b3d14cc45135eb
- ca80f7198ca049c40a8b32d0c317595f
- 5cb2a3602f1056a8fba8072fbf80561a
- 296d63f69293f56fb1ffafeae04a756f
- russ@oshlaw.com
- Kasin22.anondns.net
- b05f9798620028f6f88a04c672bfdba2
- 848db3f9ccbcd65aa0ff91da10d6ac22
- 77e093ff9a44fe0266d5e1b736683efe
- 3ba3a33626207a86999baeb188747d5a
- 2ce5e29abd1c94dc99632c63e415ba12
- a493cf8de03552a775f738d77ad6e457
- 2947efb92b290724c7b3b61b7d2a0195
- 3e7f5c2ab812e00d0a2a443f7aa5eb90
- d8ff63a61f6d8c3379b4c64eb624d6b7
- b64d3d38de70cade9b423e87c571a65c
- 11099bafe8fb1dac645f72e9a993cb0a
- 99ee3de2e32f7a05df15738023304bc5
- 87648c0d0f9a255a22274249948a11a0
- 85e12111e6913b3cd30f1f21caba1462
- 50afa07549676ea22c0e27f6aa583af0
- 0f249172ac7501af462248588daaab50
- 6048ce6db60de443e7b98c41f16c6952
- b273d861bfb4f8daabe143c7a74de547
- 6b32ce8781e54e27c1fe42f0d2bdbe0e
- aa251635e7e97d9276a93ceabbacdbb1
- 054c9912afa050b56082ca8584ced948
- 71af888e3467c69e45b98f95aeafe68e
- bf382d8b554244e70a7e13ac363365a1
- b049c27324c3a01311f20d5db294817f
- 64d4977383bc99c6832e5e015a46889f
- 5cd0afa3d3bb5226e84b274175d8178b
- 47208e7f253f38e574fa150794fa5890
- 3bf8b746e02db924c6af2220b531d1b2
- 4b127db25684359a302c55f49db5c708
- 3ce16e7fc2da4be70a72e7e48609f67a
- d4bf0c9b291e039178495b432943cdbf
- e3b3aa27254565637b0b1a1fe2faed3b
- db4879df2426ca0cc100f7a72fc3418e
- 2bc2cd08e21bef440ec6c83eb0068442
- 25e1336f22b27b3cb5d7bc91abdd1a9a
- dc531753ba238d56549445ea7d1a5ca1
- 7ffdbd968f6e1db7eae9e058ac79e9bd
- de4c6b36cf1b707eed2b3b3c5dd2e718
- dfd4f7657cf7cea7ba272c1b791cd5a0
- 7203f98c19dd4859488b688fc775a8ef
- fbe9e18d77342dcac9eeae4977ffb3c6
- 893bb4521b75b301cfb7b3106c055c12
- 8623e275f3a769bc2528fdc39728e244
- 49c5a54f2864bf3e0cdb9343d897acda
- da8e03697343af47fc7e29ed56d4663c
- fd8c225bcdf57c6f0fb5c6f111b47ef5
- ea7164cf3ef1b9037d7bcfae09f23aa3
- de2de1eb68b066c0e69921f51234d40a
- 715a252cea21f0d4f4ae7f0723baf625
- f03a90f320c3677ba1b3e16ea64b3f49
- d0f76accd3c94906fb2b66cab84d96f8
- 4c096113de849cda645135fa7b3bb5ca
- 07c8988b88d404b1dee9adf977255a44
- 2675cc6b4f9698befbcb508cd32178a1
- 288c8506e0c8784e8285cedc877d1170
- a66f45a7d2d065ba375adfd790ebcbc4
- 1d02925bc24b0edc1b0603c45e93a696
- c5a85316c07b6e7088c2c409f1febf22
- 14e54cff871c6236579abfbcc353ecb3
- b07b433cddb3f795331c3f27dd8aa189
- 6ebed61e44202aedc4d1ba58c16d4c5d
- 4cbe999b7105a8111bef31df5e103fc1
- 421e764a03c725bf64008e60ddb15a84
- 1448b06d2157f1dbe4e8f449f737214a
- 4556288adc268b13695ffddb58ad329d
- 7086c4d6d0e0196f08afb9cf8c80e0a8
- 1c60490885081a0782380118f5e36e58
- 69f3c1b39b1717297b8af0b324fa37fb
- 1796319d7ff9d14843f56d1dc15c79a3
- 1967d49246e5d1dbfa3fb4271ca353b1
- 5b2f84d6b552ca9bd0351df357158ea5
- 0173c335860852cb6145f14500abb149
- 1984543d91123d8c869bdd42b929f015
- 3ca077d1b43e2fd567d3e49490f86d5b
- f92cd489de2b5d82b4c3998b40cb3df8
- 726c1741ef33c9b0dfdfb1d8e53ce0fa
- d8d0cac5170380585f806b897cd14b9d
- d33b15e2850f533af9e46c7846d4bcc5
- bf07d7a18fc32261c0a536919fed5e69
- 46310732752848582065e901f5a6a233
- 89cd5cbe803b8d4b0f27c9750a7f9a04
- 08cf33bd7d34ef0c49b17bd53e5ee83c
- fca6d5ce3fe97f21615cbe08d688b2ac
- 60224f437f45761c083fe11c2d88b0d7
- 357e4a0b14e8c481008e79df870ff729
- 3796ab8db2ca9dc884a591a69b3715d4
- 333dddd525c3910a319b363f77d0bc39
- 7565cb88cae52972604d22a729e7a693
- 91444bd4b6bc087ea1fff367fe029749
- 7d6a0116622f6f519f607ba0a9e7add4
- ebc8e0604ae3b66aac419d6b309574db
- f86462bae226b4f9c65f83f224621af6
- c4cb22e51ecdce8b1b9398b96c89171c
- e2e1b95b55dd0d7fc5f983b4d518db0b
- 18335fefbc5885cfc42df41ebc4ef31b
- a01a80d8c1f665eda5a81391a1ed0024
- 9d5a9f7b2eafc725c2c2f8f3b55ca17e
- 684a68dc8e1f5929906ea5f5fee005b4
- 2254eca6a943144866f648514e3ed8c1
- 2ee07292c98fa68c37775a3e8f1aa9ae
- 4619beab0955d17c69b6a03d725cab26
- 4a5f9323e22265ba5572b40a0bcf9e60
- b8e1fc27a3a78c6ec296f1060702bd35
- f32535d6fd244010c2c03f3015efb386
- 5d5cc5d15a2186ca442a0d865d2c6c6d
- fc52076dceba92f778e3ddfc779b82e4
- a87b746ce6e4eb54300fdccd2ecd653f
- 4c878ac8a33ce5201e2a25abd081a8d0
- 936873144e6e0fb2b703c766a19bb7e8
- 485ce9a3df08af7369b5ad055f3d1a99
- 93ee0c45cf836ff300145bd069ba9107
- bccb4b2ab4b27ff1c632533e0584cf79
- dd602d27f47c1c3f5c597960db8c1a51
- 186216fc1e1327ab007aedd8188231e7
- f1c1ac1c5cbc3bc1ac1b8e03440086e2
- d60a9a14c3fc5bc24b1e0f8638bcfb51
- f62e18c391a571d5b293c4cf7d220543
- 79699e683b1f5db921656ffb0f0d8c1e
- 89f68ff5e4965218126f8e616a7a7798
- 99f9f82711ec2c53ef7ff114b80ebb76
- b8e48661ea97a690308d8987625cbf48
- 7b3f4d34b8d3518c092d81506df05103
- 7c0b9116ad3584b3104a54281bcff793
- 51976d5a76b203b25bbc514d6129de9c
- 9fb707a0ab4259078495c94bb6b6a2e9
- 42c0a87246ee89b37c0e7846e07627e5
- 690fbe64c5cf40f4e43ec4d2193e66b0
- 73f9ecfae60b17cb6331b0800bd0c16f
- 06705be1357579f491aa5abb67aca22c
- d714cea27c300d0b2789098763a884ab
- 32c7b6a978b2c5c19a983d50fd52c0f7
- 7af30ba52976fec95c0fd86691a7329f
- cebeb96d7e2d36264fb6f50570051ee8
- 3d70e84758aef8a192f95e4e092cb769
- 8efcb17298c5af05639f85e042f5f69c
- f2896464e2c3389ad4c98eccb19f9acd
- e9ea1026cf176f4d497a27d0c856bedf
- 8542228028211206428187271d831981
- b7386ff0ad31f28448c4704d30b5cfeb
- be2ad88838969e92010fab7d958ee0f2
- d32ad97efa23f8ad4269a5e59589703b
- a050291d555cf05c1b5fd6049ff85c8c
- 68320761a01f9df5f1bdc71c94326311
- d983cebe16603091c83e39b5f4eb266d
- a1afebafe5a7598cef0ef8f348d49996
- 18fbd1aec9f66d3b92a2d89f81bcc929
- b28bf1217eaab7dc2281beacf8c00f6a
- d1f2de5b461f3344f4274806c4ff1ac1
- bbcb31367235ceb97549bf432587d6f2
- 3f7cc1cb3da89b1ad57bc35bc73d54a9
- ef3c98feca4c88c14c78e890ecdd705e
- 00f7c19a8494bfa0d734648d18c464df
- a9bfee1aa5068c03ce1b4580698f000a
- 781add1dd969276ba231c975ccc7a15f
- 54d42f80e8e09f1568f335be20393cb5
- 1ee9703849ab4d406c9c57e35a0c211f