Today’s Cybersecurity Dilemma: Analyzing over 100,000 security incidents daily from more than 150 distinct threat actors
The Challenges:
- Security teams struggle to keep up with threats
- Uncertainty about relevant and significant threats
- Blind spots from ineffective, scattered cybersecurity tools

The Solution: Defend Against the Threats That Matter Most
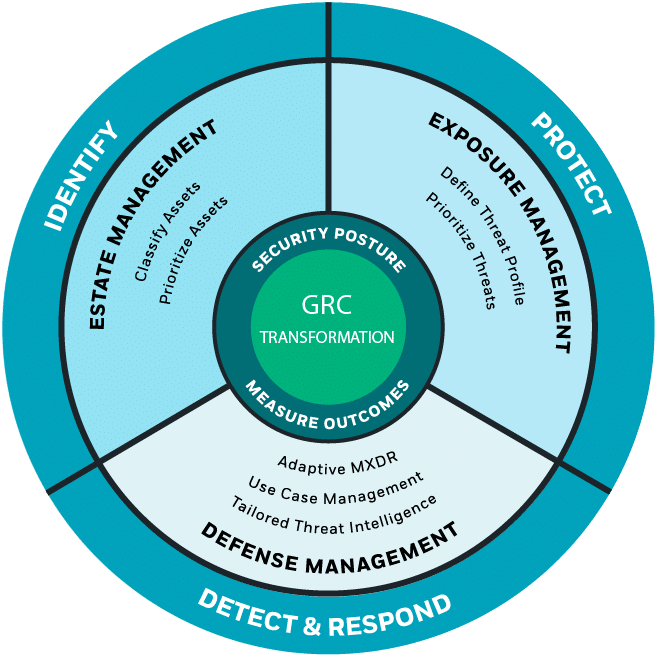
CyberProof provides an integrated threat-led platform that combines:
- Estate (Asset) Management: Tag, classify, and prioritize known and unknown assets to understand your exposure – continuously
- Exposure Management: Focus on relevant threats using CTEM and ASCA frameworks – continuously
- Defense Management: Optimize detection and response playbooks – continuously
- Resulting in GRC Transformation: Mitigate Global Risk, Define Business Outcomes & ROI, Mature Security Posture
SecOps & Risk Mitigation
CyberProof uses OSINT and threat intelligence feeds for visibility into threats.
CyberProof’s adaptable playbooks address continuously evolving threats with updated strategies.
Professionals manage sophisticated networks, leveraging experience to counter advanced threats.
Professionals manage sophisticated networks, leveraging experience to counter advanced threats.
24/7 global SOC support ensures incident response with guaranteed SLA.
24/7 global SOC support ensures incident response with guaranteed SLA.
CyberProof develops recovery plans, restoring capabilities after a cyber incident.
Classify and manage enterprise assets, understanding risks and data sensitivity.
Non-destructive tests uncover potential exploits in assets and applications.
Mitigate security issues early with CyberProof’s training and awareness programs.
Rigorous security assessment for on-premise and cloud applications to ensure protection.
IAM manages user access, monitors for anomalies, ensuring security.
Cloud First approach ensures compliance and security within cloud environments.
Managed service for SIEM, EDR, MXDR, and threat intelligence solutions.
Identify, assess, and mitigate security vulnerabilities through regular scanning.
Partners
“Today I have complete visibility into the entire environment, in real time”
Jamil Farshchi | Equifax CISO
CyberProof CTEM
CyberProof’s CTEM platform, powered by Interpres, is able to continuously identify, assess, and prioritize risk, while enhancing defense services like MDR, Vulnerability Management and Use Case Management to address evolving threats. Take proactive steps to fortify your security today!
Threat Alerts
Exchange Server Vulnerabilities Enable Persistent Credential Theft
Threat actors have recently been observed exploiting legacy vulnerabilities in internet-facing Microsoft Exchange servers to inject keyloggers directly into Outlook Web Access (OWA) authentication pages. These keyloggers are embedded into legitimate login interfaces, allowing attackers to harvest credentials in plaintext while avoiding detection. Because the login pages continue to function normally, users remain unaware that their credentials are being intercepted. The malicious scripts exfiltrate captured data to attacker-controlled infrastructure, creating a covert and persistent threat.
This campaign reflects a broader shift in tactics: rather than relying on traditional malware payloads, attackers are compromising authentication mechanisms themselves to gain access. The continued presence of unpatched Exchange servers gives threat actors stable footholds for credential theft operations
Ongoing Exploitation of MOVEit Transfer Vulnerabilities
A renewed wave of cyberattacks is once again targeting MOVEit Transfer, the secure file transfer solution from Progress Software. Recent reports confirm that both cybercriminals and APT groups are exploiting known and even zero-day vulnerabilities in MOVEit Transfer, putting sensitive enterprise data at risk. The uptick in malicious activity has reignited concerns following the large-scale 2023 Clop ransomware campaign, which compromised hundreds of organizations through similar flaws.
MOVEit Transfer continues to be an attractive target due to its critical role in handling privileged data transfers across industries. Despite past security updates, threat actors are actively scanning for unpatched instances to gain initial access, exfiltrate confidential data, and extort victims. Organizations relying on MOVEit should prioritize patching all instances, verify configurations, and monitor for suspicious file transfer activity to reduce their exposure to these persistent threats