Contributors: Vishak Unnikrishnan Kavita, Niranjan Jayanand
Introduction
In early June 2025, Artic Wolf researchers reported on malvertising campaign serving malicious Oyster backdoor disguised as PuTTY, KeyPass and WinSCP through SEO poisoning leading to Oyster backdoor infection aka Broomstick or CleanupLoader. The Oyster backdoor campaigns have been known since at least 2023 and have been known to lure users into downloading malicious installers for software like Google Chrome and Microsoft Teams in the past. Oyster backdoor like any other malicious loader is known to assist in ransomware infections like Rhysida, for example.
CyberProof Threat Researchers spotted one such instance of an Oyster infection in the second half of July 2025, where the user was tricked into installing a malicious installer impersonating Putty file. The backdoor was detected and blocked hence there were no signs of hands-on keyboard activities spotted. This blog covers some of the technical details of the files observed during this attack.
Technical Details of Oyster Backdoor
The image below shows the kill chain spotted by the SOC analyst:
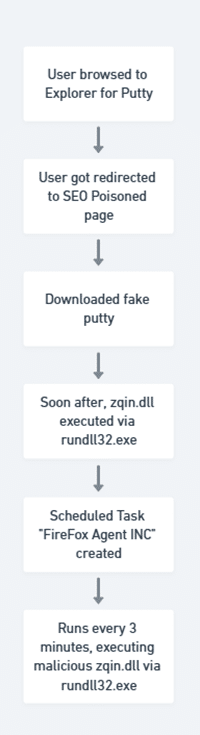
Fig.1: Attack kill chain of Oyster backdoor
Once installed (usually via fake installers found through SEO poisoning or malicious ads), Oyster backdoor can give attackers remote access to compromised systems.
It is programmed to collect system information, steal credentials, run commands, download more malware, and keep itself active by creating scheduled tasks.
During review of the incident by CyberProof SOC analysts, it was confirmed that the user likely was tricked into downloading a malicious installer from remote url [https[:]//danielaurel.tv/wp-json/api/download/553d53f6d17341fb5a4acdd48f2a0152] as shown below, in a sandbox environment:
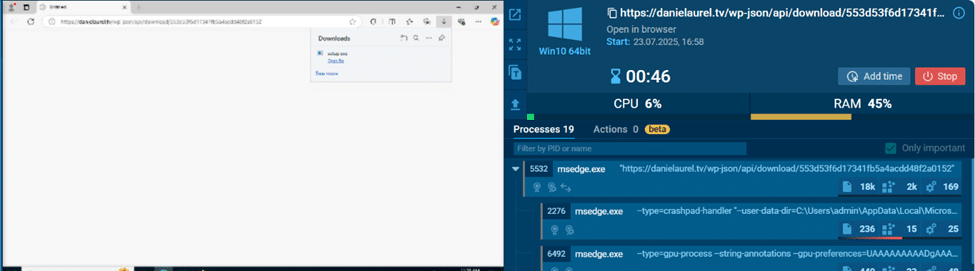
Fig. 2: Download of malicious installer
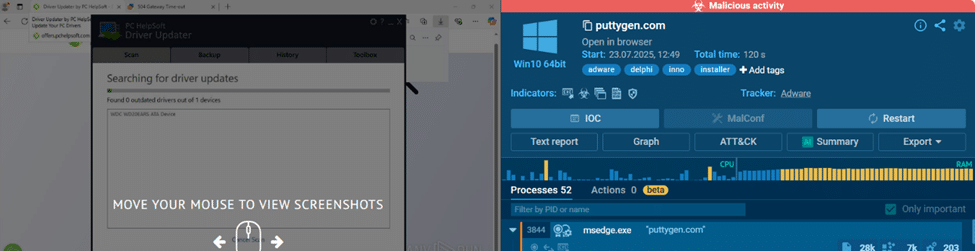
Fig. 3: File executed in sandbox (Anyrun)
The file identified during the SOC incident includes:
- File name:
PuTTY-setup.exeSHA256: a8e9f0da26a3d6729e744a6ea566c4fd4e372ceb4b2e7fc01d08844bfc5c3abb] - Downloaded url:
https: //danielaurel.tv/wp-json/api/download/553d53f6d17341fb5a4acdd48f2a0152
The installer used a certificate that was revoked.
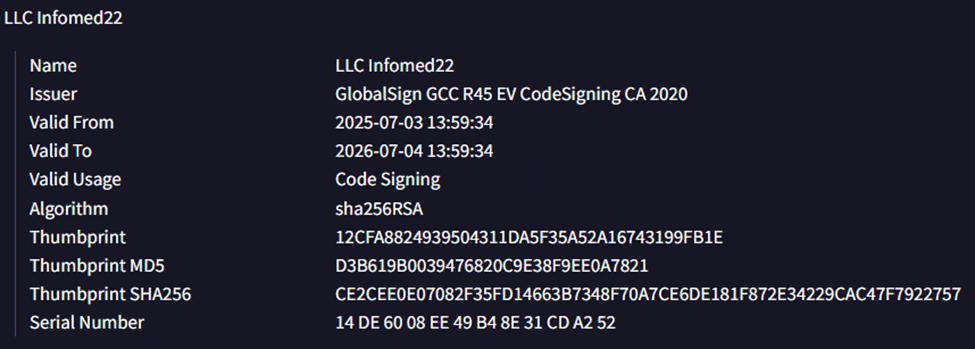
Fig. 4: Signer information
Other files seen using this revoked certificate at the time of writing this blog are shown below:
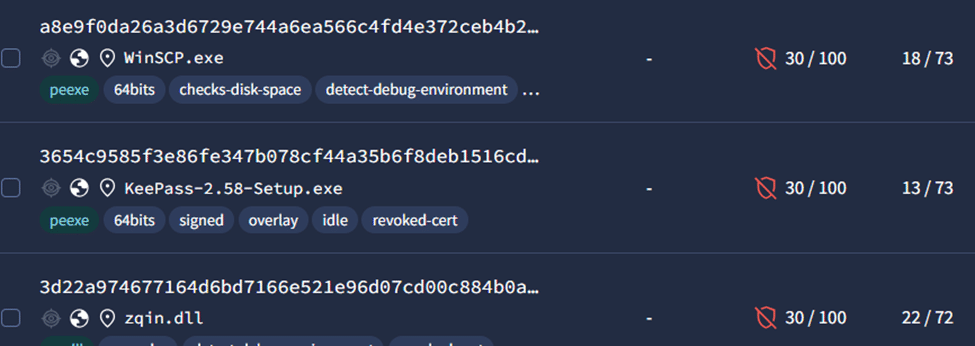
Fig. 5: Files in VT with same signer
We have recently shared observations on the spike in digitally signed malicious droppers used in similar malware campaigns over the last few months. In the reporting we shared how certificates used in the campaigns were later revoked. Learn more about our research on ConnectWise ScreenConnect malicious droppers in the blogs ConnectWise ScreenConnect Attacks (Part 1): Continued Surge in RMM Tool Abuse and ConnectWise ScreenConnect Attacks (Part 2): IRS Themed Attacks.
Reviewing the web proxy logs confirmed that the user search could have led to other malicious links for malware download through SEO poisoning.
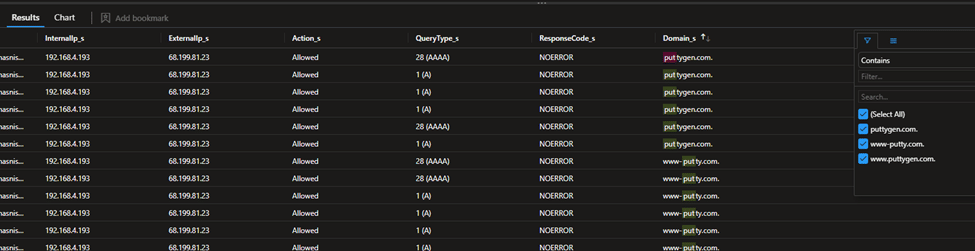
Fig. 6: Filtering proxy log to check putty impersonating website visited by the user
Reviewing the events and confirming the download of a malicious executable as shown below.
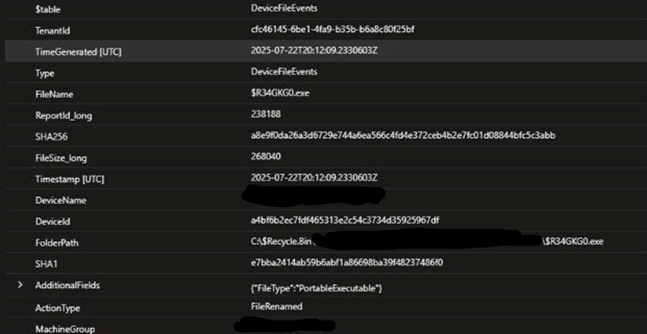
Fig 7: Event on the endpoint confirms the file’s presence
The user accidentally executes the malicious executable, which leads to dropping and execution of a malicious DLL file, which is the Oyster backdoor through rundll32.exe.
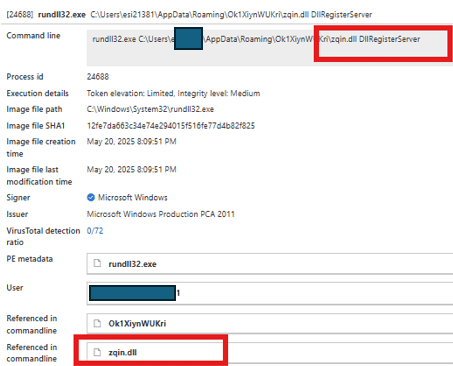
Fug. 8: Execution of Oyster DLL payload using rundll32.exe
Oyster backdoor achieves persistence through a scheduled task named “FireFox Agent INC”, which is set to run every 3 minutes. By executing the malicious zqin.dll via rundll32.exe the task is created as shown below:

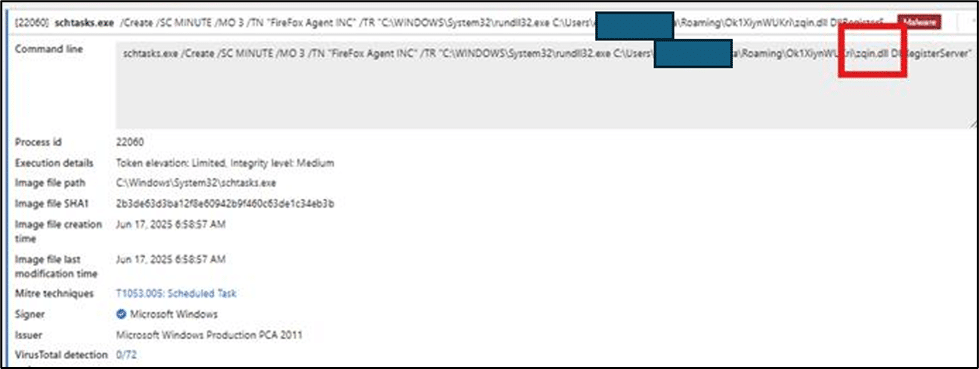
Fig. 9: Scheduled task creation for persistence
Hunting Queries

Indicator of Compromise
- updaterputty[.]com
- zephyrhype[.]com
- putty[.]run
- putty[.]bet
- 3d22a974677164d6bd7166e521e96d07cd00c884b0aeacb5555505c6a62a1c26
- Zqin.dll
- a8e9f0da26a3d6729e744a6ea566c4fd4e372ceb4b2e7fc01d08844bfc5c3abb
- 3654c9585f3e86fe347b078cf44a35b6f8deb1516cdcd84e19bf3965ca86a95b
- puttyy[.]org
- 194.213.18.89
- 85.239.52.99













