Contributors: Niranjan Jayanand, Prajeesh Sureshkumar, Deepak Nayak, Archana Manoharan, Kalyani Kalva, Vishak Unnikrishnan Kavitha
Executive Summary
CyberProof researchers have been tracking multiple infostealer campaigns were certificates are revoked post our reporting, Authenticode stuffing used in ConnectWise ScreenConnect, and how attackers rotate their tools over time to evade detections.
Over the last eight months, CyberProof Threat Hunters and MDR Analysts continue to see different waves of malicious installers impersonating legitimate productivity tools with backdoor capability, likely using EvilAI. Researchers reported that EvilAI disguises itself as productivity or AI-enhanced tools, with professional-looking interfaces and valid digital signatures that make it difficult for users and security tools to distinguish it from legitimate software. Some tie this campaign under the name TemperedChef.
Infection vector is confirmed to be through Search Engine Optimizations (SEO) manuplation or through newly registered domains. Our telemetry confirmed that Manufacturing sector users were heavily impacted, followed by financial institutions. From our analysis, we can confirm that this campaign is currently with no specific regional or industry targeting unknown motivation at this moment. Close to about 5-7% of our incidents were related to these campaigns between June – Sep 2025.
CyberProof Researchers also confirmed the backdoor is also capable of extracting DPAPI secrets and provides full command-and-control functionality, including arbitrary command execution, file upload and download, and data exfiltration. In most observed cases, the malware proceeds with the deployment of second-stage binaries and establishes additional persistence mechanisms, such as ASEP registry run keys and .lnk startup files.
Several EDR products have shown late detections of this long-running campaign. CyberProof team has worked around the clock to help notify customers of these EDR gaps, isolate affected machines teaming with our Advanced Threat Hunting team.
Technical Details
In the next sections, we will highlight key points on what to look out for these different flavors of backdoor campaigns that shows some overlap in their process kill chains.
Campaign 1: AppSuite PDF Editor
Between mid-May and end of August, CyberProof MDR analysts saw few organizations hit by this campaign also reported by other researchers as TemperedChef. Below image shows a user accidently clicking on a malicious url hosting attacker crafted installer with Backdoor capability.
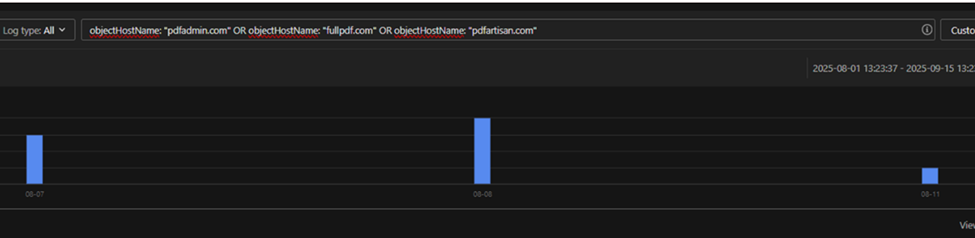
Fig. 1: Searching for three malicious domains related to this cluster in TrendMicro XDR
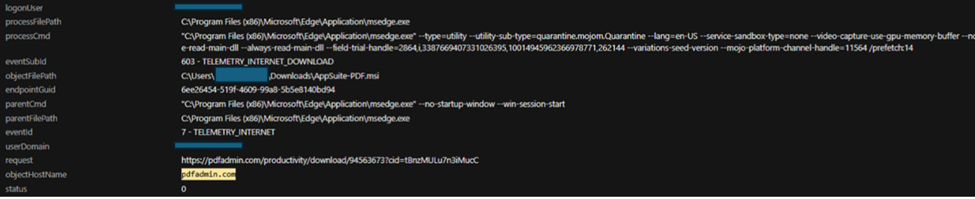
Fig. 2: Image from an infected user, seen downloading the installer from pdfadmin.com
Further analysis helped us identify another url that serves malicious AppSuites PDF installer.
Fig. 3: Sample holds – https://vault.appsuites.ai/AppSuites-PDF-1.0.28.exe ; see below from the strings found in sample (hash : f28a0cf84e09873b77f9e2e5a800fd67)
https://vault.appsuites.ai/AppSuites-PDF-1.0.28.exe ; see below from the strings found in sample (hash : f28a0cf84e09873b77f9e2e5a800fd67)
Campaign 2: OneStart PDF Editor Campaign
Researcher spotted OneStart PDF Editor used as decoy to infect users with backdoor starting mid February 2025.
Around August 2025, a researcher confirmed OneStart Browser is the root cause of the additional pups being installed on the endpoints. OneStart creates Registry AutoRun Keys and Scheduled task for persistence.
The Scheduled task are triggered upon boot/login. Node.js/Node.exe then runs the <GUID>.js file from the AppData/Local/Temp folder to make a network connection to the C2 mka3e8[.]com.
Sometime around the 16th of august, this C2 connection triggered a MSHTA process to connect to portal[.]manualfinder[.]com to download the manualfinderapp.msi file. In another instance, we saw https://pdf.onestart.ai/en/pdfeditor 5e1689ca04778ff0c5764abc50b023bd71b9ab7841a40f425c5fee4b798f8e11
Campaign 3: ManualFinder Campaign
Researchers reported a file named “ManualFinder.msi” getting dropped onto a system from a JavaScript persistence. It resembles a lot to OneStart PDF Editor campaign.
According to the researcher, here is an example log from one instance he saw, where the parent process establishes persistence, and then the process is the installation of ManualFinder:
- Parent Process:
c:\users\redacted_user\appdata\local\programs\node\node.exe
- Parent Command Line:
"node.exe" "C:\Users\redacted_user\AppData\Local\TEMP\[guid looking-number]of.js"
- Process:
C:\Windows\System32\cmd.exe
- Process Command Line:
cmd.exe /d /s /c "msiexec /qn /i "C:\Users\redacted_user\AppData\Local\TEMP\ManualFinder-v2.0.196.msi""
ManualFinder has a code-signing signature for the signer “GLINT SOFTWARE SDN. BHD.” which has now been revoked.
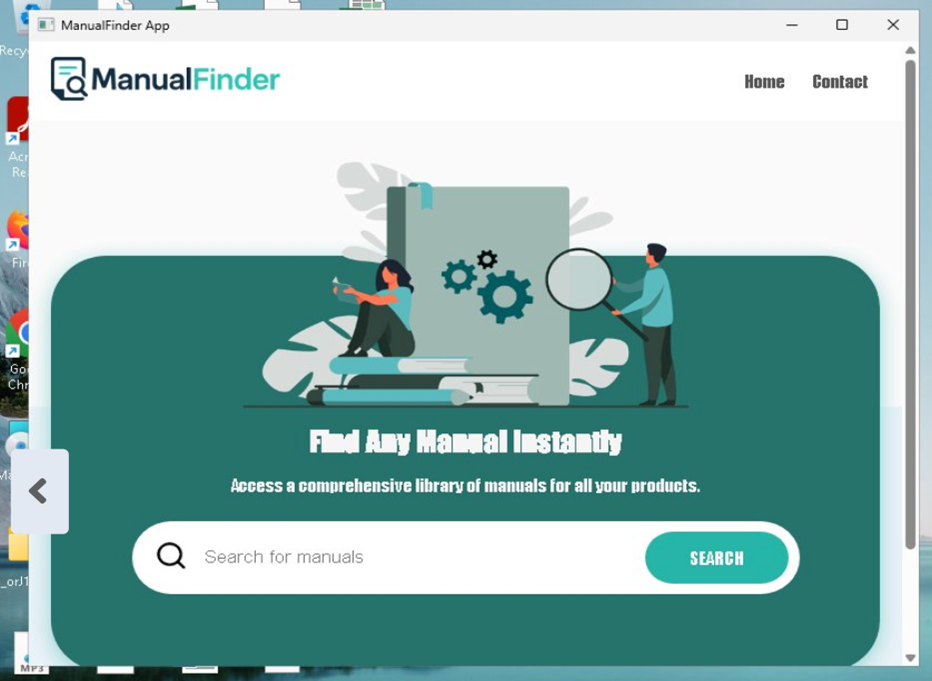
Fig. 4: Image of webpage serving the installer – url : http[ : ] //lib.manualfinder.app/ManualFinder-v2.0.196.msi
This is the high level process kill chain seen in this campaign:
node.exe → cmd.exe → msiexec.exe → ManualFinder-v2.0.196.msi → ManualFinderApp.exe
Below is an example of <GUID>.js naming pattern, spawned by node.exe:
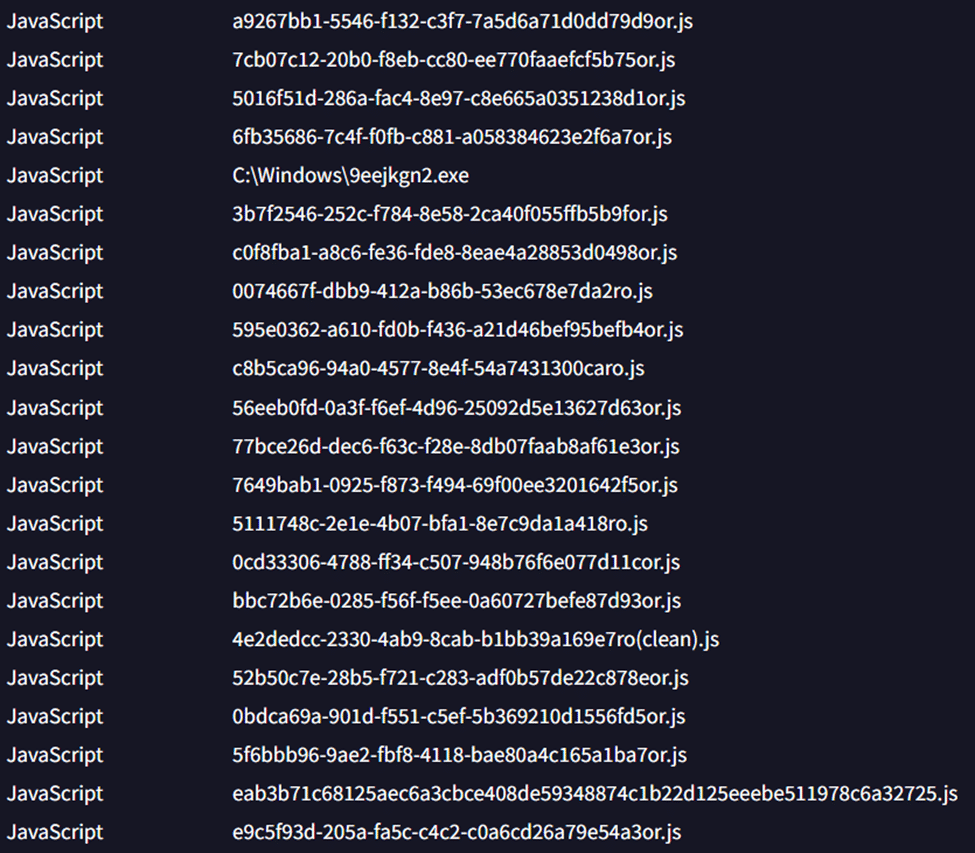
Fig. 5: <GUID>.js naming pattern seen from in this cluster when checked in VirusTotal
Below image shows late alert by SentinelOne EDR (source – link):
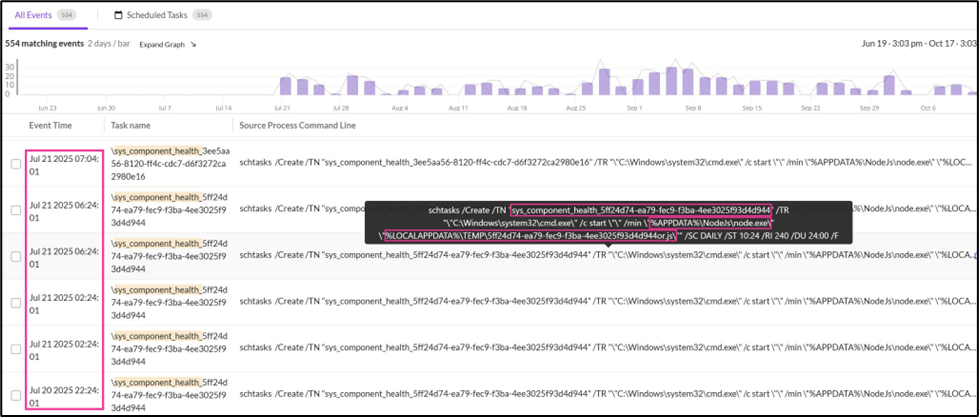
Fig. 6: Late detection seen in SentinelOne
Campaign 4: ManualReaderPro Campaign
Another similar campaign was seen running with ManualReaderPro themed installers as shown below:
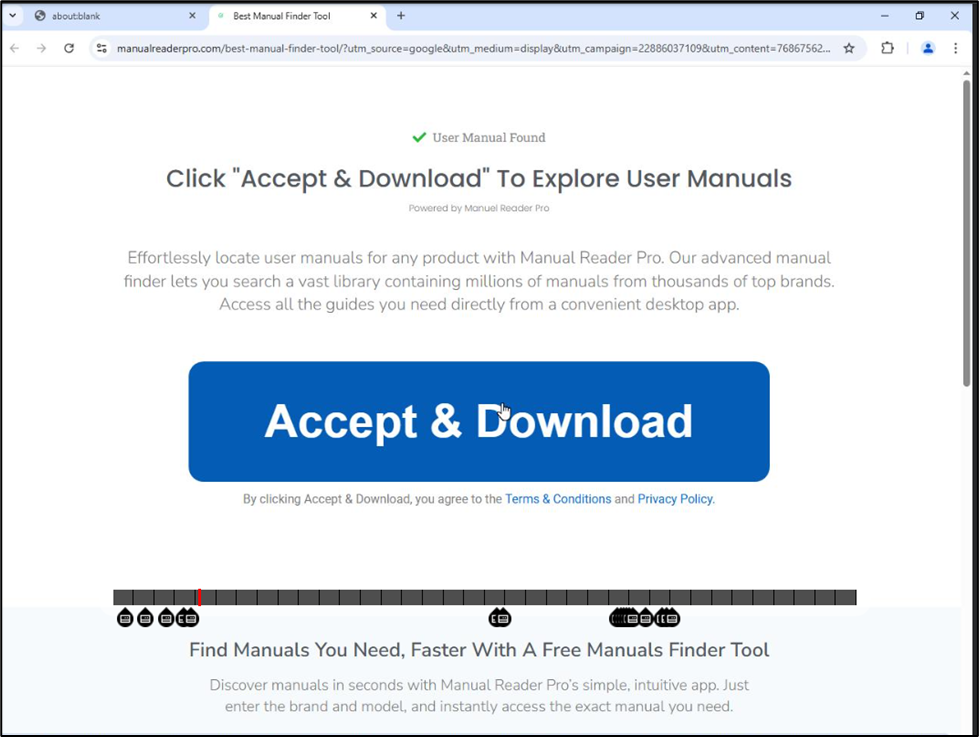
Fig. 7: ManualReaderPro website serving installer
The sample on execution launched a java script file and remote connection as shown below:
"cmd.exe" /C start "" /min
"C:\Users\redact\AppData\Local\Programs\ManualReaderPro\node\node.exe "
"C:\Users\redact\AppData\Local\Programs\ManualReaderPro\7ec7fc48 811d-4a03-8707-537c55f5864f.js" ◼ "node.exe"
"C:\Users\redact\AppData\Local\Programs\ManualReaderPro\7ec7fc48 811d-4a03-8707-537c55f5864f.js" ◼ Node established connection towards the site
"api[.]cjby76nlcynrc4jvrb[.]com"
Late Defender detection at persistence stage of scheduled task was alerted by name:
'Trojan:JS/Obfus!MSR' as shown in below image : HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows
NT\CurrentVersion\Schedule\TaskCache\Tasks\{36E2D293-A247-4F36-9CBA B3037E84F152}\'
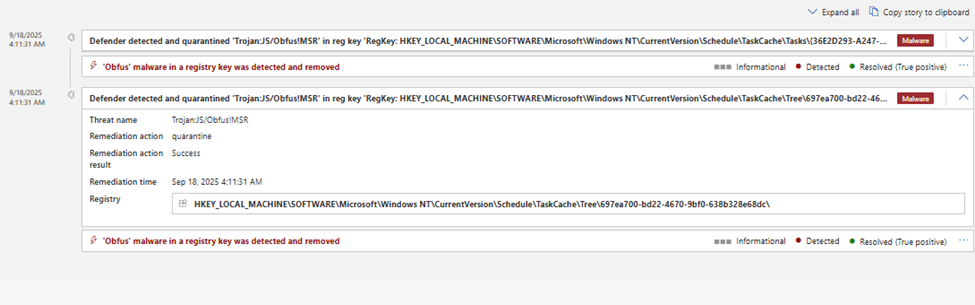
Fig. 8: Late Defender alert of JS dropped for scheduled task for persistence.
Campaign 5: Crystal PDF Campaign
In early Septmber 2025, CyberProof Researchers notified their customers of another wave of digitally signed PDF masqeurading installers.
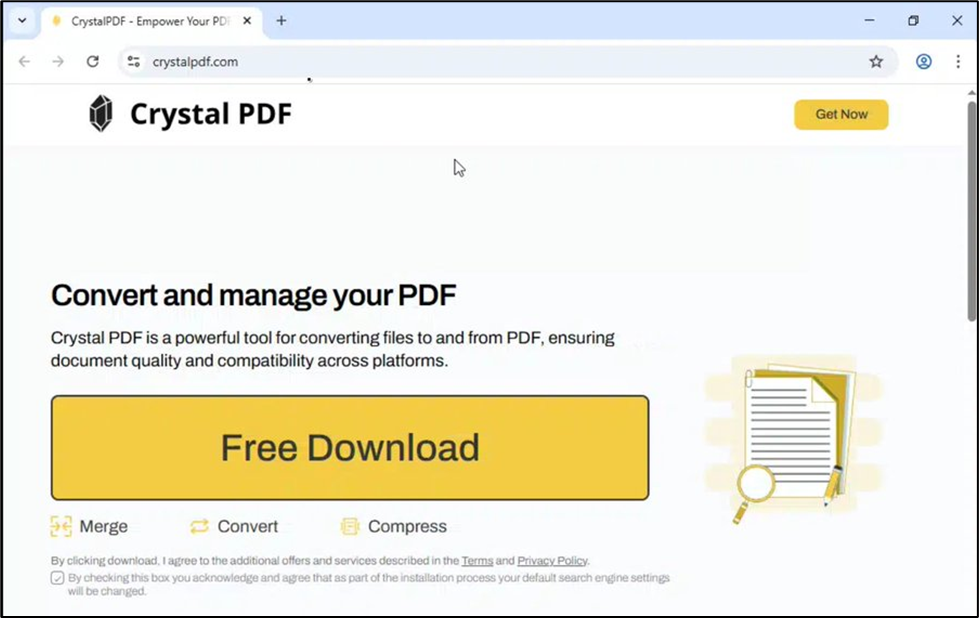
Fig. 9: Newly created website related to Crystal PDF
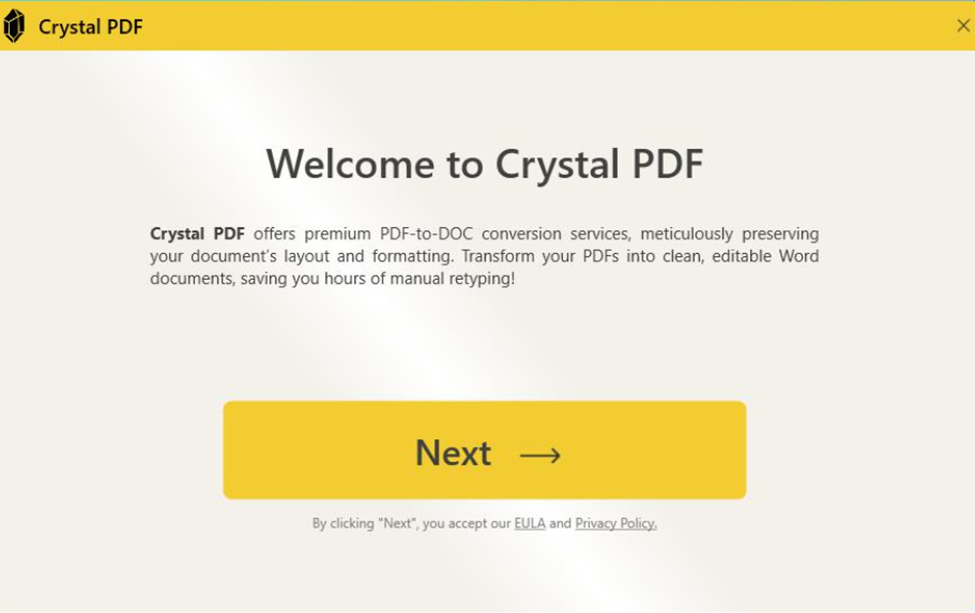
Fig. 10: User tricked by Crystal PDF tool features
The samples identified under this cluster or campaign were signed with below mentioned signed, the certificate is revoked at the time of writing this report.
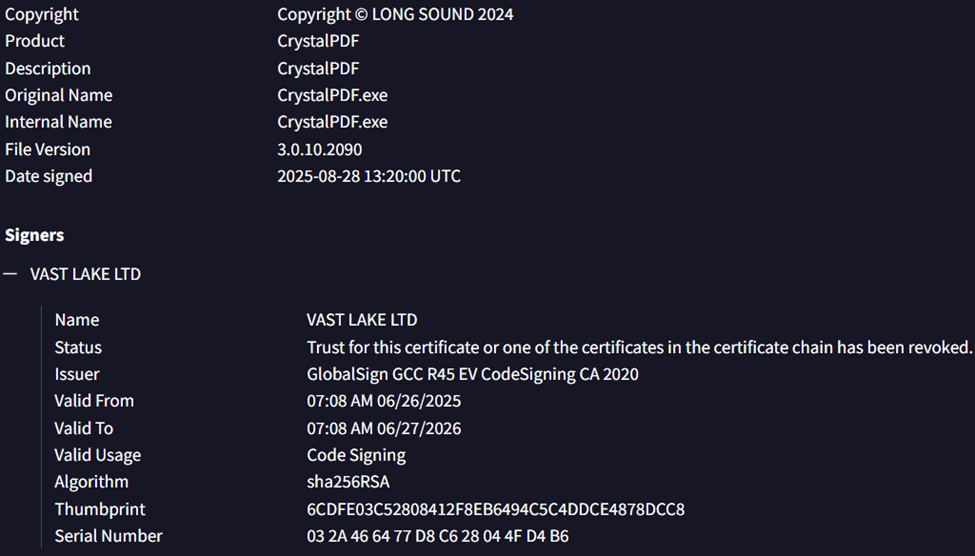
Fig. 11: Digital certificate information from a CrystalPDF sample
Webpage View of Malicious Domains
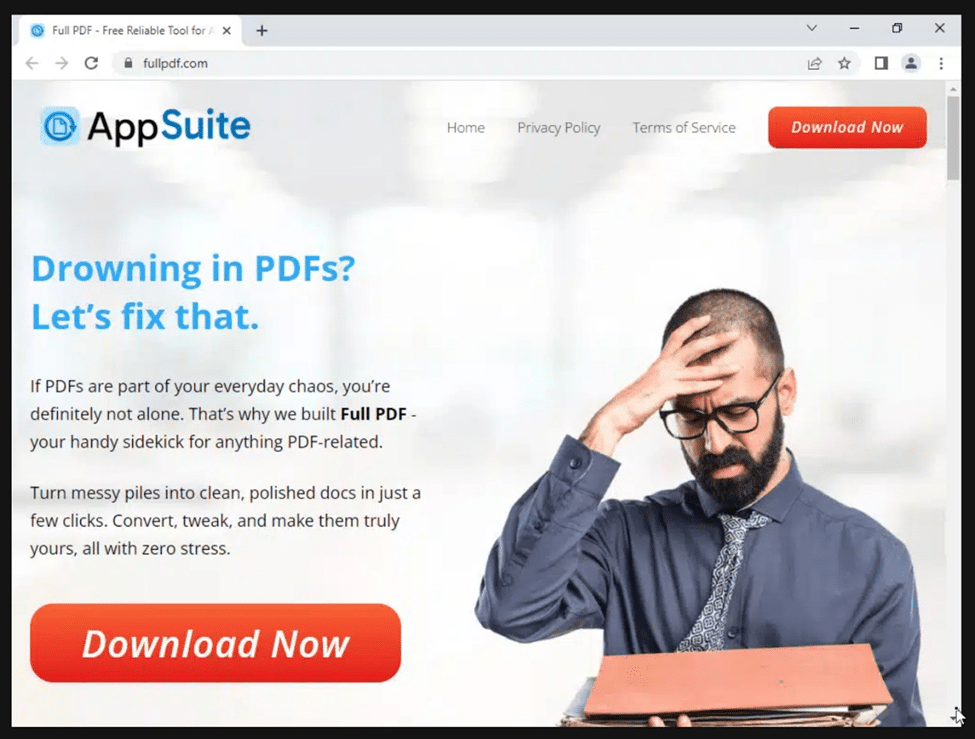
Fig. 12: Webpage related to AppSuite cluster
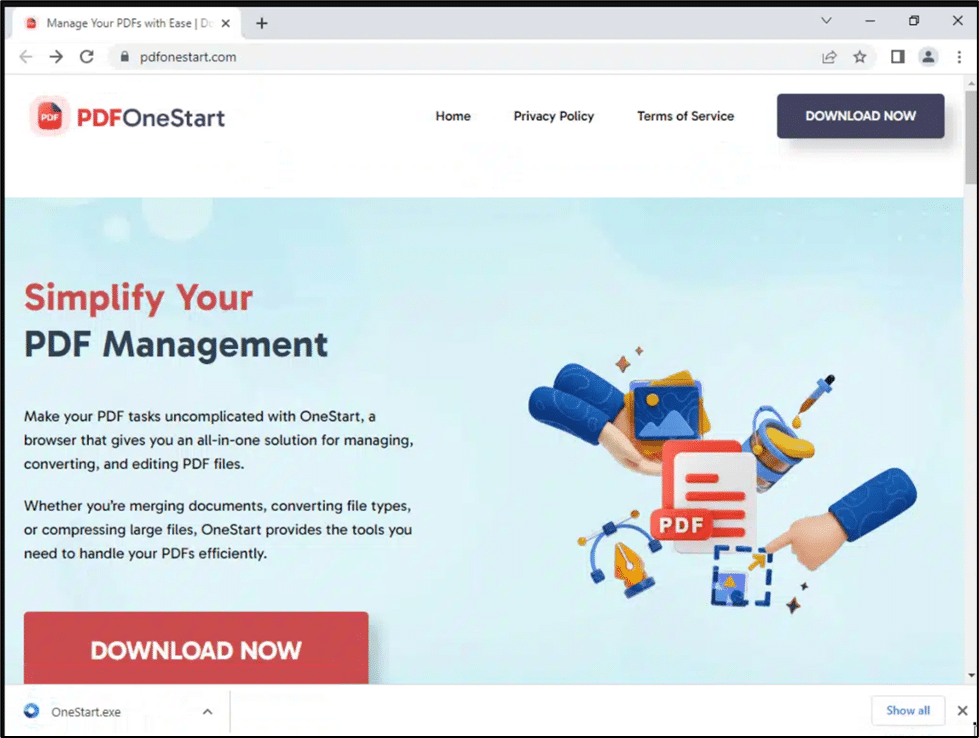
Fig. 13: Webpage related to PDFOneStart
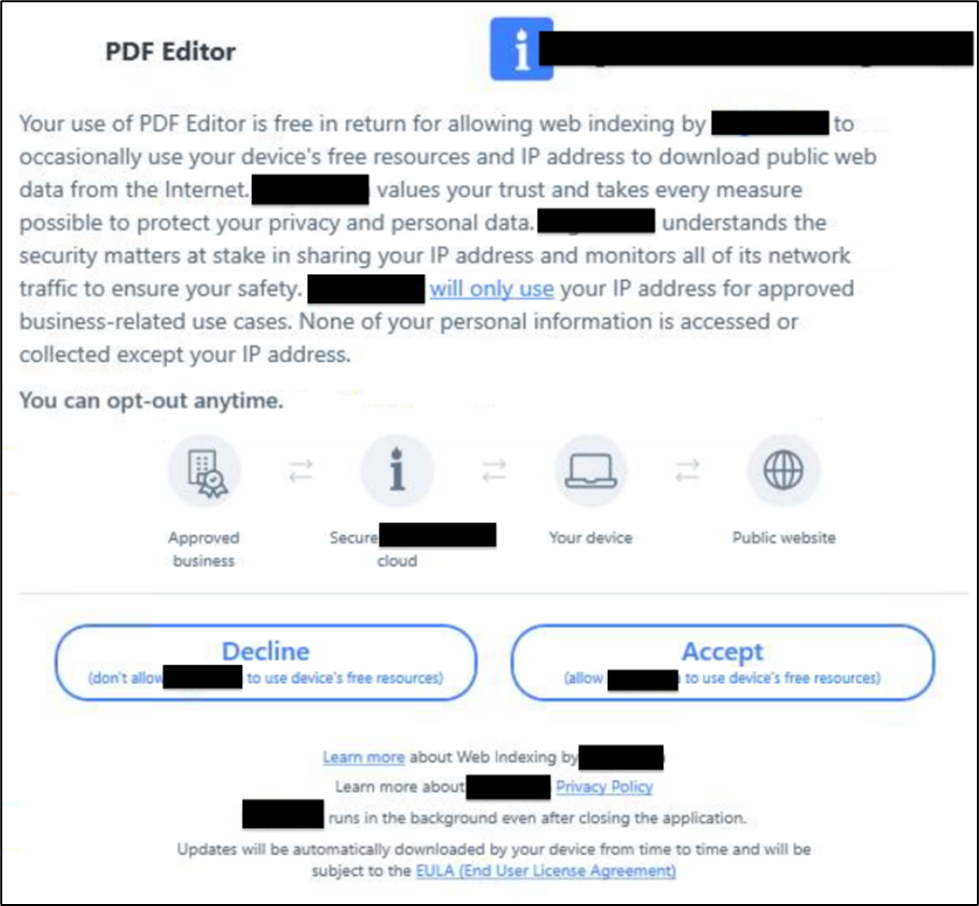
Fig. 14: GUI related to PDF Editor cluster
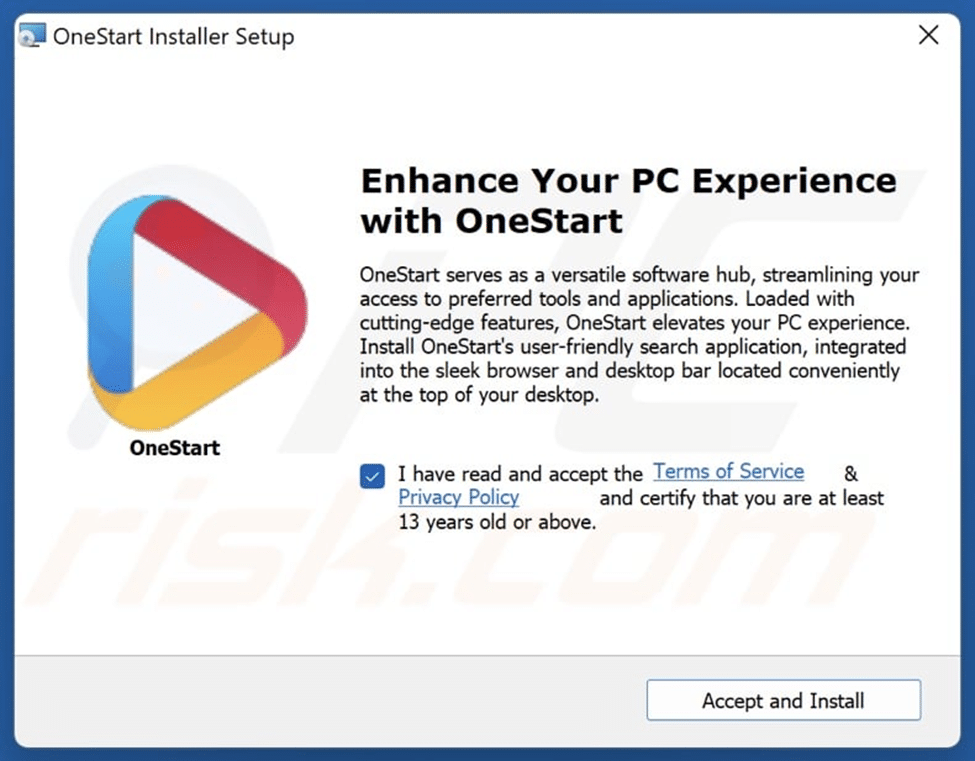
Fig. 15: GUI related to OneStart Cluster
KQL Hunting Query
source: FREAKJAM from reddit post
DeviceNetworkEvents | where Timestamp > ago(30d)
| where ActionType == "ConnectionSuccess"
| where InitiatingProcessFileName =~ "node.exe"
| where InitiatingProcessCommandLine matches regex @".*\\AppData\\Local\\TEMP\\[a-f0-9]{8}-[a-f0-9]{4}-[a-f0-9]{4}-[a-f0-9]{4}-[a-f0-9]{12}.*\.js"
| extend Username = extract(@"\\Users\\([^\\]+)\\", 1, InitiatingProcessCommandLine)
| summarize
FirstSeen = min(Timestamp),
LastSeen = max(Timestamp),
TotalConnections = count(),
UniqueRemoteIPs = dcount(RemoteIP),
UniqueRemotePorts = dcount(RemotePort),
Usernames = make_set(Username),
RemoteIPs = make_set(RemoteIP, 5),
RemotePorts = make_set(RemotePort, 5),
RemoteUrls = make_set(RemoteUrl, 5),
SampleCommandLines = make_set(InitiatingProcessCommandLine, 3)
by DeviceName
| sort by TotalConnections desc;
Indicator of Compromise
CrystalPDF Campaign:
- 0a1fd8b4ad7d3d00dd8e48c74ddc0ae9
- c9b3703a5a2417129bd75da8745d813f
- d7e6cf1104ddd987045a4334a78378d2
- 5c5fa3827b0648989d1f734f4f5b1437
- 3a12246519d58778025946f1d74a7dd6
- 099b45d8f53fda896d2d847d4aece489
- 8e8656355a5a0ff5683d1ccf6b46c9c3
- crystalpdf(dot)com
- negmari(dot)com/Cry
- strongdwn(dot)com/abg
- ramiort(dot)com/Cry
- Onestart.ai
- d0838244e7ebd0b4bd7d7486745346af6b9b3509e9a79b2526dcfea9d83c6b74
- mka3e8[.]com
- y2iax5[.]com
- portal[.]manualfinder[.]com
- Manualfinderapp.msi
PDFSuite Campaign:
- pdfadmin[.]com
- Pdfmeta[.]com
- Pdfartisan[.]com
- Pdfreplace[.]com
- fullpdf[.]com
- Appsuites[.]ai
- 4e8bd351aa8bc45d94c5f60086b5dad4
- e7311867d3a9c177b7ec81cf92f09c52
- 81bfa3fbe14bd30952dad17ce0daeeaa
- 98fa065c8d40d3b4f82e6b3f303aa4b3
- B66d89ee13a48e9c8d4a7aa2e3e1cb2b79f0b95e4f74f4184b85628656281588
- 6c36fd8afb93e7c9ae62d5962cb2c6bf
- f6bc17c61524935637887617e5752f88
- de792af1f053f582bb6fe971bcb16a20
- 08e42764571804aa3e27530b03dd5d99
- 365160a0259aa7f46bf5395ff5c27243
- 71a48137d84fee3bcbe885ab7f84c004
- ea4e4113b16411a9d2a5cc1e61586609
- 186996c413c8574c3b380043687ea677
- 532507b853dc28988915fd8e4327f0e8
- 4a32a922cd35839b2227e269e3953f53
- 15b187d465e8d02d715b69b8203e01bd
- aed64325de919c00588ba99cabc834d4
ManualReaderPro Campaign:
- abcd8cd8dce84186c04e3b83c93ee4bd
- 296690fcb018a76cbfd5c9a16123a575
- a340147e26151ef380b74c1c59d8086f
- 6b50bf28f3cf6d138089c6954085a076
- 287de08218ea23f7e795da3caf525bb6
- 71bddf977d92f3ad92ec678b0fa226da
- a603cf81719c036c35419aebf38f6952
- 07cfb523c055361030b806c2d3c9e41a
- 1f6137470ddf89659b1816eed26f3c46
- 3dbd10478d2d2b21d11c0e392e3cb751
- c35cb8e4ce9ae9e11509f241d40e99bf
- f6e7b560735df83efa3f10982af991fc
ManualFinder Campaign:
- 62e43638548bbe4909eaf8408d8b5686
- a5d7966e70b62f95ec2e3d18f5f8ab2a
- 92dbeca8f1d5710a3e180090bed44318
- 2d633863e4fe1c6223aebb67c992f478
- 1efaffcd54fd2df44ab55023154bec9b
- 4b561a4b6e430d9d8bc89058bb60ed43
OneStart PDF Campaign:
- 7c57900a9ee5e8af100323ceb66f5e15
- e5b4f5922c8a1a1259847f5707438814
- c2522f0dcc7d511396cd89f5139db164
- 59ccf747e93dae15c5af5d037b763bfe
- 17b0a6ff85e3715fa43fa8b78acbef1a
- 10a3d72209c889add463ba382a2c5def
- 2233b56b43392b0a9a4242e6e89bcd94
- 390e9809611e640ff8f15fc5d4fb711d
- 0f3d699e108c546769d5154a13332dab
- b04309c2dc6f6aa5d9caafd91a0e7ebf
- 5d5d019da21487b59f6ce4ab745d4f08
- c9e85b19c02828f4992c79f6de18e929
- 49f42fc87247db3d09baaee2dcc40273
- a6059a38bf4dcfd231e6a7dc508ebb40
- 0063eb128135844508bca784cede6207
- 88f220fa42e8214890f8a8f6a338a190
- 4ef5fe50c51728bab14761ae0983011b
- ec53c97d3d5e5a533a212070440073cd
- a99c9c45a26fa6cd2f25a94ae14e83bc
- 5c846698be10663d9c3bd755c18ad236
- 5031aab13b5a910673972b89f40855e4
- 11340d90a28496f3d410615bdd7b763e
- b2c1de6a86d5e896a54a21a421758670
- 49a075ba9c2067fa942e8447d88238d7
- c51de5f6311ac04d43eef52e8db3e61e
- b9dcd9da9b80d98798ccc352845d2a9d
- b9bf43a89b95a264ea434137652f0331
- bbb0deb9694b8f9de2309ae1c2de152e
- b8d2ba01f5b8c2dce60925c5c4523f97
- d72602a40437c71a02f72b159ac924b1
- 652ebea13847d6e422f7fd51c3bcae66
- 7ab778ef3e05b6cc862991fdc1f1c935
- ea61944963a7d863d346dad84bf302f6
- c5b163355dbace1734987116b7cd6d78
- 0d89b948d3748a22440e9fc2fdd1fde6
- d82f50b5fb015fa65a0a455d3af8a30b
- 73aa25ec608d576ddea7c1d04387d5a4
- 68ff4fafdc7f64877a443892c5f942f7
- 25b34222e021bffeae3ec852972b7b29
- 75494758823352c604627981bb9c3704
Malicious PDF Download Theme Domains:
- allpdflive.com
- apdft.com
- appsuites.ai
- businesspdf.com
- convertpdfplus.com
- easyonestartpdf.com
- easypdfbox.com
- fastonestartpdf.com
- fullpdf.com
- getonestart.co
- getonestartpdf.com
- getpdfonestart.com
- getsmartpdf.com
- gopdfhub.com
- gopdfmanuals.com
- itpdf.com
- justpdflab.com
- manualsbyonestart.com
- mypdfonestart.com
- onestartbrowser.com
- onestartpdfdirect.com
- pdf-central.com
- pdf-kiosk.com
- pdfadmin.com
- pdfappsuite.com
- pdfartisan.com
- pdfdoccentral.com
- pdfeditorplus.com
- pdfmeta.com
- pdfonestart.com
- pdfonestarthub.com
- pdfonestartlive.com
- pdfonestarttoday.com
- pdforsmartminds.com
- pdfreplace.com
- printwithonestart.com
- proonestarthub.com
- proonestartpdf.com
- quickfastpdf.com
- quickpdfmanuals.com
- smarteasypdf.com
- smartmanualspdf.com
- smartonestartpdf.com
- smartviewpdf.com
- thepdfbox.com
Recommendations
It is recommended that Threat Hunting Teams should:
- Check for code signers reported and revoked related to this campaign to avoid new installations.
- Investigate scheduled tasks that execute JavaScript with NodeJs (node.exe) and remove them.
- Keep your CTI feeds, AV, and EDR solutions updated.
Conclusion
We believe this long running campaign is not going to end until this year end at least because long holidays and festival season is different countries which attackers would take advantage of target users opportunistically and through SEO poisoning. We advise customers to invest in training their employees against cyber-attacks as such campaigns are long running and attackers constantly shift their infrastructure and code signers to evade detections. CyberProof analysts are utilizing both AI and human analysts’ skills to tackle such campaigns in proactively notifying customers when EDRs fail as seen in above campaigns.













