American IT outsourcer Cognizant is the latest high-profile company that has been hit by the Maze ransomware. Classed as a severe cyber attack, Maze disrupted Cognizant systems and caused service disruptions to some of their clients. This is the latest in a series of high-profile attacks internationally that have been carried out by Maze operators.
Maze is particularly dangerous because after it spreads through the network and locks out users, it exports data to the hackers’ servers. Maze operators frequently threaten to leak the compromised data or use it in future attacks – if ransom demands are not met.
A Short History of the Maze Malware
Maze was previously known as ChaCha ransomware and was first discovered on May 29, 2019.
The cyber criminal group behind this ransomware is the Russian APT, TA2101. Their main goal is to encrypt all of the files that the ransomware can find in a breached system, and demand a ransom to recover the files.
Since it was first seen, the ransomware has used different attack vectors to infect targeted companies around the world. Attack vectors include: sending malicious emails, using exploit kits, and attacking RDPs.
Recently, Maze operators started using a new technique to pressure victims to pay ransom: threatening to publish sensitive data gathered during the attack. This threat is followed by additional techniques designed to increase the campaign’s impact on affected companies – such as stealing backups before encrypting the files.
Recently, Maze operators started using a new technique to pressure victims to pay ransom: threatening to publish sensitive data in addition to locking out users.
When Maze first emerged, it was distributed via Fallout and Spelevo exploit kits, which exploited a vulnerability in Flash Player (CVE-2018-15982). Maze was also distributed by means of malicious websites and through emails with malicious attachments, which were used to drop the ransomware’s payload.
Maze has also been detected stealing data through FTP servers by running commands in PowerShell. In some cases, the attackers first stole data from the organization’s cloud backups before encrypting the files.
Recent High-Profile Data Breaches Using Maze
Maze attacks have been seen in the US, the UK, Europe, the Middle East, and Asia targeting dozens of organizations across a variety of sectors. In the past week alone, approximately ten companies were targeted in Maze ransomware attacks.
The operators make no distinction between governmental and private companies. For example, earlier this year, in November, the group was focused on Germany – impersonating a German service provider and German governmental organizations, and sending out malicious emails. In December, the group attacked Pensacola, Florida; the attack took place via systems that were exposed publicly by RDP.
Customized Ransoms
A novel feature of this ransomware is that it customizes ransoms according to the type of device being attacked. It tries to detect if the device is a home computer, workstation, domain controller, server, etc. and then adjusts the size of the ransom accordingly.
In the last few months, Maze operators have claimed responsibility for dozens of ransomware attacks in which they demanded millions of dollars to decrypt the files. They announced their attacks on their official news website. If they were not paid immediately, they published portions of the data they gathered on a Russian hacking forum.
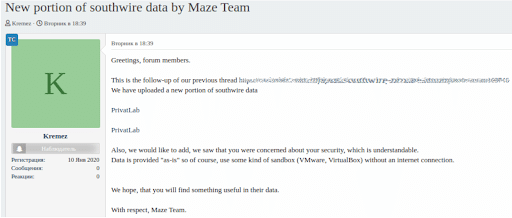
The Maze Team Spreading Stolen Data from Southwire on a Russian Hacking Forum
Maze Exploits During COVID-19
Maze operators claimed they would not target healthcare companies during the COVID-19 pandemic.
Yet, a few days after making this claim, they attacked a vaccine testing facility in the UK.
They are continuing their wave of attacks despite the pandemic. There was additional news this week when the operators published a press release offering tips to victims about how to act after they are attacked. The group claims to be open to price negotiations with companies that adhere to their rules.
The Maze Attack on Cognizant
After Cognizant was hit by Maze, the company notified its clients and provided them with related IoCs. A few hours after the attacks, a security researcher provided a YARA rule to detect the Maze ransomware DLL file.
Maze operators deny responsibility for the attack. This is not surprising, as in the past, Maze operators did not discuss attacks or victims until negotiations with a victim stalled.
The Cognizant attack is recent, and it is likely that the threat actors are not discussing it in order to retain leverage and avoid complications in what they hope may turn into a potential ransom payment. It is possible that they will announce the attack soon and perhaps publish portions of the data they gathered, to pressure Cognizant into paying the ransom.
Because of the way that Maze works, it is likely that it was present in Cognizant’s network for weeks, spreading slowly and stealthily throughout their system, and stealing files and credentials. Usually, once the threat actors obtain administrator credentials on the network, they deploy the ransomware – taking the first steps to encrypt data and publish a ransom note – using tools such as PowerShell Empire.
Maze Mitigation and Best Practice Recommendations
Maze is a complex piece of malware with highly sophisticated stealth techniques, with this variant acting mostly within the device’s memory section (including the encryption phase). It leaves almost no traces of evidence on disk.
Maze is a complex piece of malware with highly sophisticated stealth techniques, with this variant acting mostly within the device’s memory section
CyberProof has worked to uncover IoCs and IoAs to actively hunt for evidences of this Maze variant and to provide data protection assistance to our customers.
Here are some of the mitigations that we recommend:
- Keep applications and operating systems running at the current released patch level, ensuring the mentioned vulnerabilities are patched.
- Block RDPs from access to the Internet. Limit external connections on Port 3389 in the organization’s firewall.
- Ensure RDP is only accessible via VPN. In addition, protect the VPN by using MFA and encourage the use of complex passwords to prevent brute-force attacks.
- Consider placing RDP servers behind a restricted area of the network, such as a DMZ.
- Conduct periodic employee awareness campaigns for suspicious emails and attachments; educate your users on how to spot and avoid phishing and malspam. Teach users to be suspicious of emails that have a sense of urgency, or that ask the user to bypass standard procedures and common sense.
- Create an effective backup strategy by following the 3-2-1 rule:
- Create at least 3 copies of the data.
- Save them in 2 different storage formats.
- Ensure that at least 1 saved copy is located off-site.
- Adopt strong passwords throughout the network.
- Consider network segmentation to separate important processes and systems from the wider access network.
- Monitor and audit network traffic for any suspicious behaviors or anomalies.
- Scan system backups for registry persistence.
- Scan system backups for other malware infections.
- Disable macros in MS® Office programs and never enable them unless it is absolutely essential to do so.
If you would like to speak to a CyberProof expert about protecting your organization from ransomware and other cyber threats, contact us today.