This blog post is the first in a series about APT attacks.
Advanced Persistent Threat (APT) groups worldwide tend to have similar characteristics: they are a group of highly skilled individuals, with substantial financial funding and, usually, a solid ideological affiliation. However, there are differences in how APT groups function based on their location of origin.
In this post, we’ll focus on the unique behavioral characteristics of APTs associated with Russian proxies and compare them to the behavior of proxy players from China, Iran and North Korea.
CyberProof’s research methods
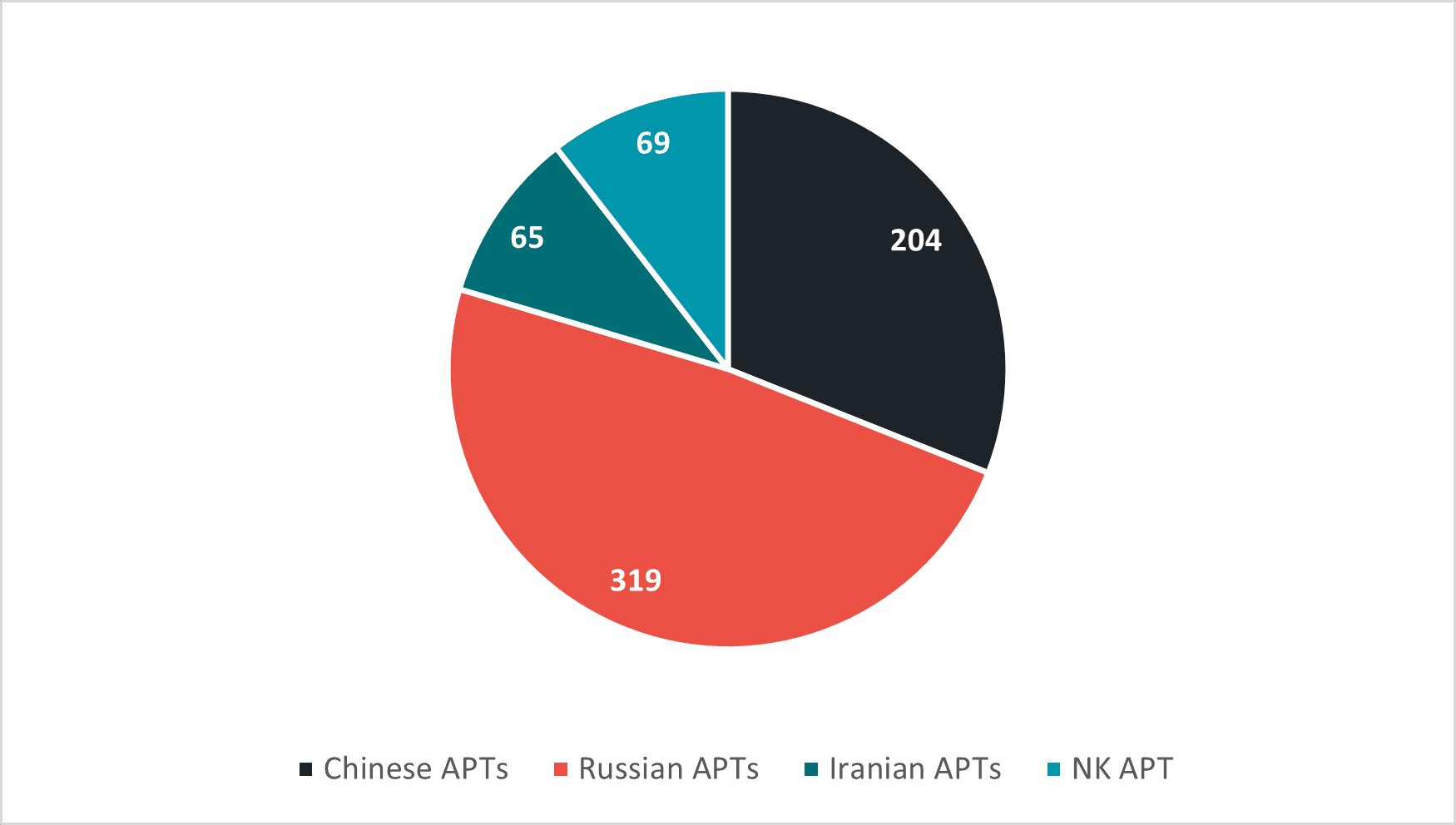
CyberProof researched APT attacks perpetrated in 2022. We focused on APTs associated with proxies in Russia, China, Iran, and North Korea.
Using the MITRE ATT&CK™ framework as our methodology, we developed several hypotheses regarding the behavioral characteristics of APTs. In this post, we explore two hypotheses, related to the tactics and techniques used by these groups. Utilizing the open web for references and verification, we were able to corroborate our theories.
For proactive measures, see the mitigations listed at the end of this post.
Hypothesis 1: APTs associated with Russian proxies have more creative, stronger & faster capabilities
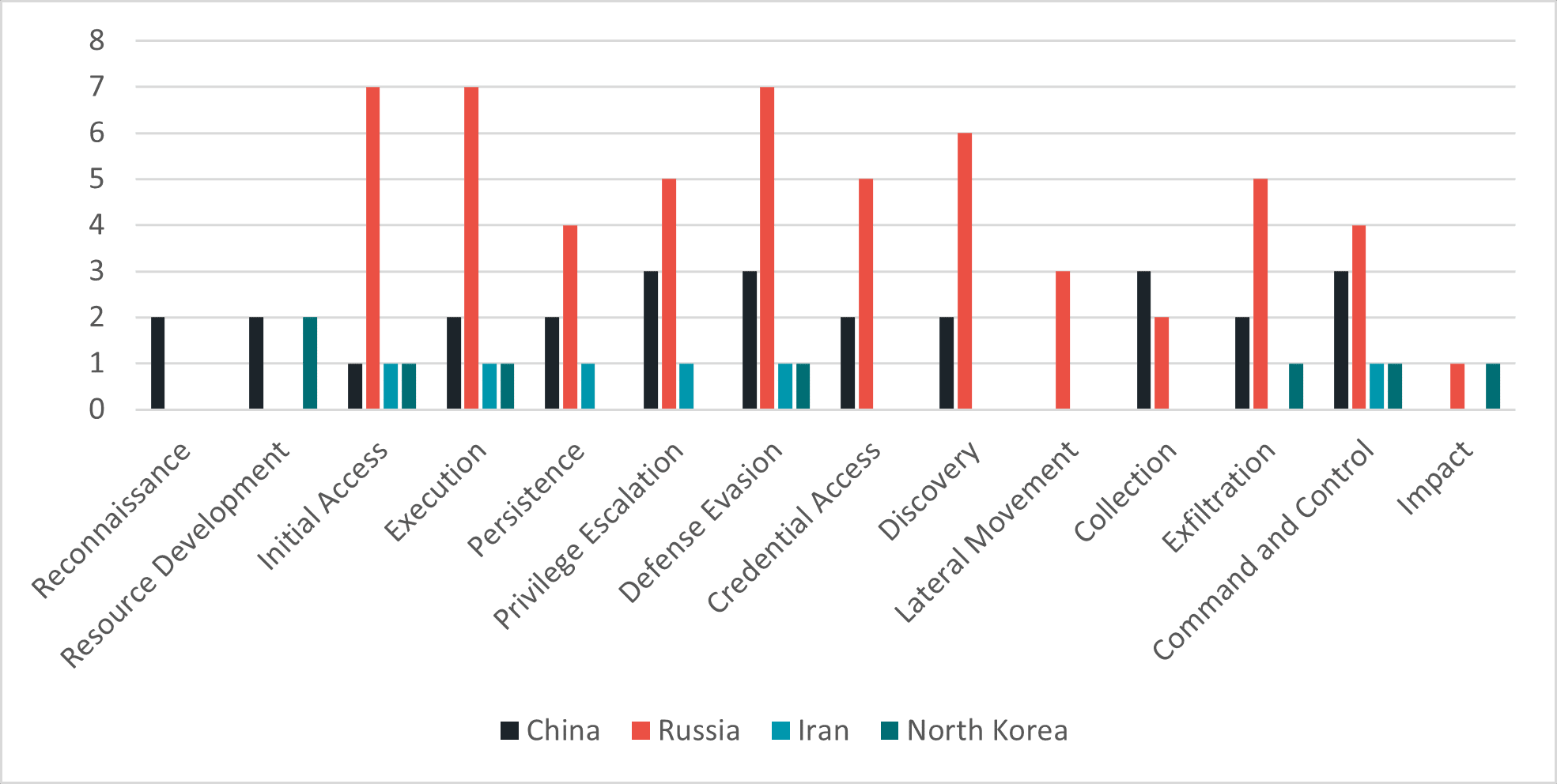
Proxies associated with Russian APTs exhibit more creative, stronger and faster cyber capabilities, especially with the tactics of: Initial Access, Execution and Defense Evasion.
Our research shows that these APTs include a much greater number of attacks that use the tactics of Initial Access, Execution and Defense Evasion. Not only do their attacks display unique techniques and a high level of competency, they also succeed in operating much more quickly.
Number of attacks by groups associated with Russian APTs, using the specified MITRE tactics
The following attacks support this hypothesis.
Innovative initial access techniques
Use of innovative initial access techniques was seen in the attack on high-profile Armenian websites in 2019 by an APT group linked to Russian proxies, Turla.
Turla carried out a watering hole attack compromising governmental websites, that allowed them to narrow their attack to specific victims – Armenian embassy employees or the ambassador himself. The group in this case was able to lure only victims of interest by delivering a script that was designed to track visitors’ browsing activity. If they were deemed interesting, the perpetrators moved to the second stage – deploying two never-before-seen pieces of malware (a downloader and a backdoor) using a fake Adobe Flash update.
Innovative execution tactics
An example of innovative execution is Sandworm, a threat actor known for attacking critical infrastructures, which tends to use PowerShell commands and previously undocumented scripts that contain malicious tools to detect system information, execute code or download malware.
A second execution example took place in 2020, with APT29 – a threat actor linked to Russia identified as setting up new infrastructure and malware while using custom tools and techniques. APT29 used encoded PowerShell commands and custom Cobalt Strike in its campaign targeting organizations involved in COVID-19 vaccine development.
Innovative defense evasion
One example of innovative defense evasion is APT29, also known as CozyBear, which is famous for creating cutting-edge ways to avoid its detection. In 2022, it was involved in a campaign that attracted victims and infected them with a malware designed to pack numerous anti-analysis capabilities, including sandbox evasion, API unhooking, and string encryption.
Another defense evasion example is Temp.Veles, an APT that utilizes malware with the intention of manipulating industrial control systems (ICS) and operational technology (OT) of global energy facilities. The life cycle of an ICS attack is measured in years, from reconnaissance to impact. As a result, this threat actor has gone to great lengths to avoid detection that could ruin a year’s worth of work. The group developed numerous custom-built tools with a special focus on anti-virus evasion to keep them hidden.
Quicker operational competency
In 2019, in a report published by CrowdStrike, it was found that Russian proxy players operate eight times faster than their Chinese, Iranian, and North Korean counter parts. While the global median dwell time for ransomware in 2020 and 2021 was five days, a group related to Russia managed to do so in less than four hours.
We have seen this type of operational competency again from the Conti group, another APT related to Russia. Just 32 hours after initial access, the threat actor managed to deploy ransomware successfully.
Hypothesis 2: APTs associated with Russian proxies conduct attacks using a greater number of techniques
APTs linked to Russian proxies carry out more sophisticated attacks using a wider range of techniques to achieve their goals.
Threat actors associated with Russian proxies successfully mastered diverse methods and use a higher number of techniques in each attack. In this, they are ahead of threat actors in other locations.
Threat actors associated with Russian proxies successfully mastered diverse methods and use a higher number of techniques in each attack.
The following are examples of sophisticated attacks that support this hypothesis.
SolarWinds attack
One of the most significant cybersecurity breaches of all time was the campaign on SolarWinds in 2020. This breach, suspected to be carried out by APT29, triggered a massive supply chain incident. It affected thousands of organizations worldwide by delivering a backdoor malware.
The perpetrators created the malware before compromising the victim. They acquired VPSs to use during the campaign. They then compromised the supply chain, installed their malware as windows service, and abused valid accounts.
They used seven different defense evasion techniques by renaming hostname, system utilities, task/services, making them appear legitimate, delaying Command and Control communication and deleting malicious files. The group was also able to hide its communication and traffic within an existing one using an application layer to avoid detection.
The attack started in January 2019 and went undetected for almost two years. Uncharacteristic of the usual modus operandi of proxies related to Russia – which generally involves disruptive, loud attacks – the evasion techniques employed in this breach show the great lengths gone to by the APT in order to stay out of sight.
The SolarWinds attack started in January 2019 and went undetected for almost two years.
Attack on the Winter Olympics
In 2018, a cyber campaign linked to Russian proxies demonstrated a high level of operational security when attackers used a total of 14 various techniques designed to disrupt the opening ceremony of the Winter Olympics held in South Korea. Sandworm, the APT associated with this attack, used among others, spear-phishing emails, PowerShell scripts, stolen certificates and credentials, fileless malware, and additional social engineering techniques to mask their identities and avoid detection.
This campaign shows the sophistication of this proxy player, which intentionally placed false flags inside the malware that lead everyone to attribute the attack to other actors, i.e., China or North Korea. Successfully mimicking TTPs ofother groups/countries implies deep knowledge and a strong skill set.
Successfully mimicking TTPs of other groups or countries implies deep knowledge and a strong skill set.
COVID-19 vaccine research
In 2020, APT29 was implicated in a widespread cyber espionage campaign that targeted organizations around the world, including several COVID-19 vaccine research organizations.
According to security researchers, APT29 demonstrated sophisticated social engineering capabilities, using convincing spear-phishing emails to gain initial access to target networks, and then using compromised credentials to move laterally within the network and escalate privileges. While doing so, the group exploited four known vulnerabilities found in : Pulse Secure, Zimbra, Citrix and FortiGate.
APT29 used a variety of techniques to evade detection and maintain persistence within targeted networks. For example, the group used custom-built malware that was designed to evade traditional antivirus detection by encrypting its communications and disguising its activity as legitimate traffic.
APT29 also used techniques such as living-off-the-land (LOTL) attacks, which involved using legitimate system tools and processes to carry out the malicious activity and avoid detection.
CyberProof’s proactive detection measures
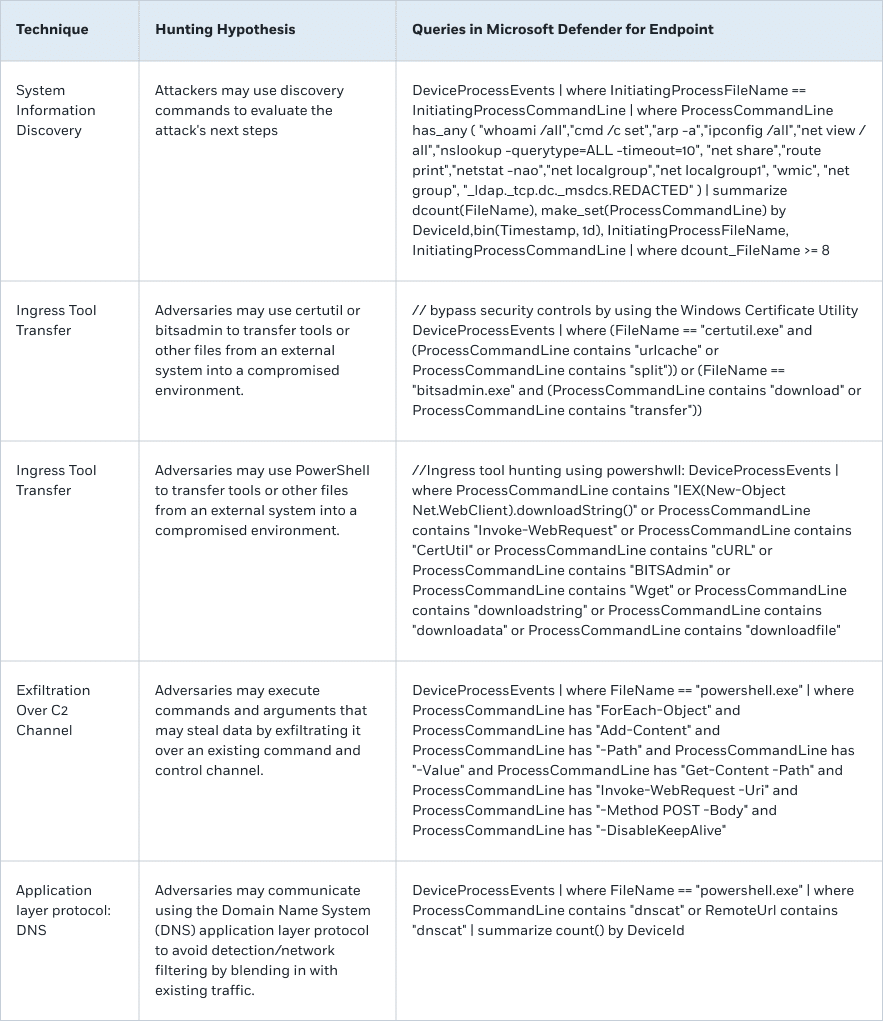
The ten techniques most favored by the Russian-related groups are System Information Discovery (T1082), Windows Command Shell (T1059.003), Web Protocols (T1071.001), Ingress Tool Transfer (T1105), Match Legitimate Name or Location (T1036.005), Process Discovery (T1057) and Exfiltration Over C2 Channel (T1041).
CyberProof provides hunting queries to detect the following techniques, which can be used for malicious activities:
This blog post is the first in a series about APT attacks. To learn more about how your organization can mitigate the risk of cyberattack, click here.