Are Your Defenses Truly Battle-Ready?
In the constant arms race of cybersecurity, knowing what your potential vulnerabilities are is critical. But perhaps even more crucial is knowing whether those vulnerabilities are actually exploitable by real-world attackers and, even if they are, whether your existing security controls would detect or prevent the attack. Relying solely on theoretical vulnerability data leaves a significant gap in understanding your true risk.
This is where Adversarial Exposure Validation (AEV) comes in. Our takeaway from the recently released Gartner® Market Guide for Adversarial Exposure Validation, is AEV represents a critical evolution in how organizations measure their security posture, moving beyond simple theoretical assessments to deliver consistent, continuous, and automated evidence of the feasibility of an attack. AEV technologies confirm how potential attack techniques would successfully exploit an organization and circumvent prevention and detection of security controls.
The Gartner strategic planning assumption is that through 2027, 40% of organizations will have adopted formal exposure validation initiatives, most relying on AEV technologies and managed service providers for maturity and consistency.
What is Adversarial Exposure Validation?
“Gartner defines adversarial exposure validation (AEV) as technologies that deliver consistent, continuous and automated evidence of the feasibility of an attack.” Think of it as putting your security defenses to the test against realistic attack simulations tailored to your environment.
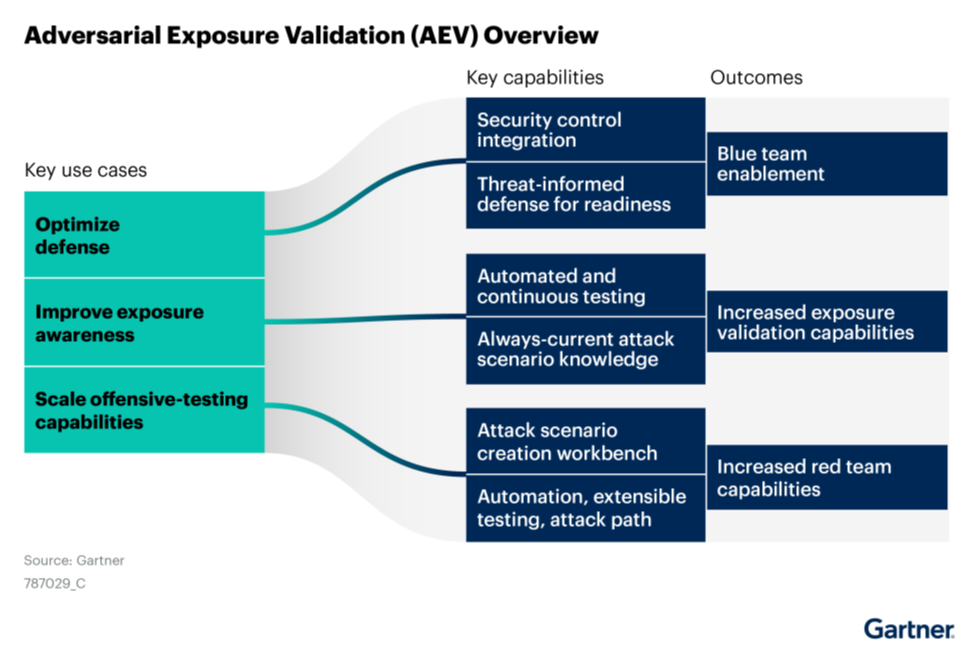
AEV overview diagram (source: Gartner Market Guide for Adversarial Exposure Validation)1
AEV is an emerging technology area, effectively replacing the market categories of Breach and Attack Simulation (BAS), Automated Penetration Testing and Red Teaming technology from previous years. These solutions help security teams validate theoretical exposures as real, automate frequent controls testing, improve preventive security posture, and enhance detection and response capabilities.
Why Adversarial Exposure Validation Matters in Today’s Threat Landscape?
The volume of potential security findings from traditional vulnerability management programs can be overwhelming. AEV solutions provide a vital “filtering” component by ratifying the authenticity of issues and gauging their accessibility to potential threat actors. This helps organizations gain greater visibility into the actual priority of exposures or attack scenarios by contextualizing impact.
AEV moves beyond theoretical data, providing empirical results about how your defensive posture relates to various attack techniques and scenarios. This is particularly important because traditional exposure assessment platforms, while providing broad information, can’t offer accurate guidance on whether a vulnerability is actually exploitable or provide context on the potential “blast radius” of an exposure. AEV takes a “closed loop” approach, proving attack scenario success within your specific environment.
By conducting frequent and consistent testing, AEV allows organizations to create trending metrics that show their ability to find, prioritize, and remediate exposure or non-readiness to attack scenarios. This automated scheduling increases testing frequency without constant human intervention.
Adversarial Exposure Validation is Foundational to Continuous Threat Exposure Management (CTEM)
Gartner highlights that AEV solutions support an organization’s strategic decision to shift from ad hoc testing to a more continuous exposure validation that enables Continuous Threat Exposure Management (CTEM) programs. In fact, the need to reduce threat exposure by implementing CTEM is a primary justification for adopting AEV solutions for many organizations.
According to Gartner, by 2026, organizations that prioritize their security investments based on a continuous exposure management program will be 3x less likely to suffer a breach.
Validation is a stage unique to CTEM. It is essential for CTEM because it provides the necessary continuous and consistent testing needed for such a program. AEV solutions can leverage both virtual validation (like Attack Surface Mapping creating a “digital twin”) and real-world testing to balance volume and impact. They help identify exploit scenarios that might be successful and invisible to SOC teams, increasing their priority and suggesting remediation actions beyond just patching. Implementing a robust Adversarial Exposure Validation capability is essential for organizations looking to move towards a truly threat-informed and proactive security posture.
How Adversarial Exposure Validation Benefits Your Security Teams
AEV solutions offer significant benefits for both defensive (“blue”) and offensive (“red”) security teams:
- For Blue Teams: AEV provides a “defender’s advantage” by quickly assessing how their defensive posture withstands various attack scenarios in their actual environment. This data is invaluable for detection stack tuning, preventive posture changes, exposure prioritization, and validating security vendor performance. It helps make existing investments in security infrastructure perform as best as possible and provides data to tune controls for readiness against the latest attacks.
- For Red Teams: AEV offers the ability to create custom attack scenarios and multi-staged attacks. It helps automate tasks associated with red team testing, increasing their scale and reach. By using workbenches for scenario creation, AEV helps codify and automate manual validation functions. AEV solutions can even help scale red-teaming functions economically, potentially reducing the required entry-level skill set with the aid of AI and automation.
AEV tools often use frameworks like MITRE ATT&CK to relate findings and operationalize defenses in a threat-informed manner. They can also integrate with existing security controls and workflow systems to recommend vendor-specific detection content and mobilize findings efficiently.
Achieving Adversarial Exposure Validation with CyberProof
Gartner recognizes CyberProof as a Representative Vendor in the Adversarial Exposure Validation market with its Continuous Threat Exposure Management platform (powered by Interpres). In our opinion, CyberProof’s inclusion in this market signifies its capability to provide solutions that help organizations achieve AEV outcomes.
By leveraging a platform designed for managing exposure risks, like CyberProof’s Threat Exposure Management Platform, organizations can facilitate the kind of consistent, continuous, and automated testing that AEV requires. A platform approach provides the necessary technology foundation to move beyond ad-hoc testing and integrate validation into a broader CTEM strategy. Adopting an AEV-capable platform allows organizations to:
- Validate the true exploitability and impact of exposures in their specific environment.
- Improve the effectiveness of their existing security controls and defensive posture.
- Prioritize remediation efforts based on validated, real-world risk.
- Move closer to a state of continuous threat exposure management.
To learn more about how we believe Adversarial Exposure Validation solutions can help your organization proactively assess and reduce risk, get the latest Gartner Market Guide for Adversarial Exposure Validation.
Gartner, Market Guide for Adversarial Exposure Validation, Eric Ahlm, Dhivya Poole, Angela Zhao, Mitchell Schneider, 11 March 2025
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.
1This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document.
The Gartner document is available upon request from CyberProof.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.






