Managed security services
Our security services combine advanced SOC automation technologies with domain experts to manage your security requirements with full visibility and transparency.
speak with an expertSecurity Event Monitoring
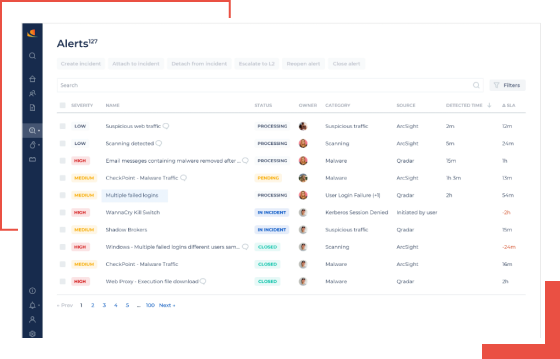
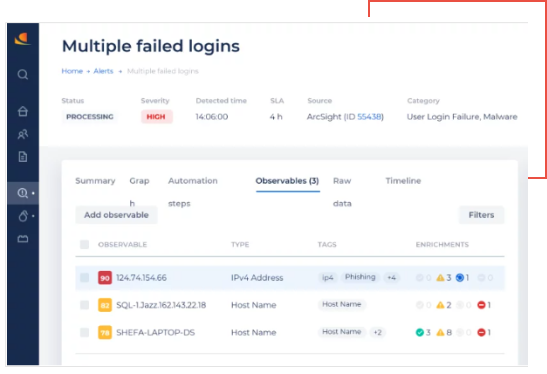
CyberProof provides 24×7 security event monitoring, alert enrichment, triaging, issue isolation and event escalation.
We monitor your security alerts and suspicious events, collected from multiple internal and external customer data sources including Microsoft Azure Sentinel SIEM. Threats are detected as they emerge in your critical cloud and on-premises infrastructure.
Event monitoring services include:
- 24×7 alert monitoring, event enrichment and triage
- Automated event enrichment
- Issue prioritization, isolation and containment
- Custom threat detection rules, use cases and playbooks
- Custom dashboards and reports
Managed Detection & Response
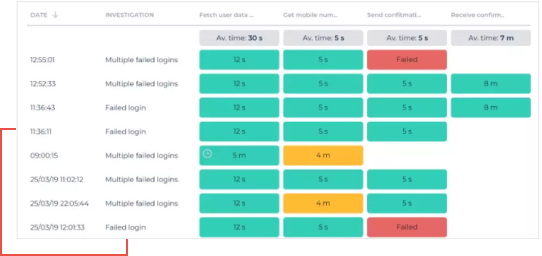
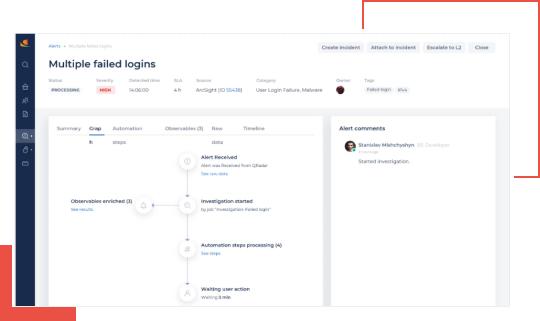
Our global response team proactively handles incidents and collects the response activities for analysis and reinforced learning leading to a continuous reduction in response time and associated exposure risk.
Utilizing ChatOps collaboration, managed incident response facilitates investigations and containment leveraging the collective expertise of the SOC analysts, threat intelligence experts, security specialists and customer team members. This improves efficiency and ensures full transparency, leading to better decision making.
Managed Response services include:
- Incident handling, threat investigation and response
- Sandbox analysis of suspicious files
- IOC validation and extraction
- Customized threat detection rules, use cases and playbooks
- Proactive automated response and escalation
- Targeted threat reconnaissance and CTI reports
Use Case Engineering
We baseline your detection rules against the Mitre ATT&CK matrix, identify gaps and take input from senior analysts, threat intelligence & hunting experts. We continually develop, test and deploy new use cases, threat detection rules, and digital playbooks.
Use Case Engineering services include:
- Access to threat detection rules
- Digital playbooks
- SIEM detection rules
- Customized use cases and playbooks
- All use cases are fully integrated into the CyberProof Defense Center platform
Advanced SOC Services
We provide specialist capabilities to enhance Security Operation Center (SOC) functions and get to the root cause of any incident.
Our team provides a service improvement roadmap aligned with your overall cyber strategy. We constantly look for services and capabilities to enhance your SOC activities and improve your overall cyber security posture.
Advanced SOC services include:
- Advanced malware analysis and reverse engineering
- Malware assessment and IOC extraction
- Flash Cyber Threat Intelligence investigations and reconnaissance
- Digital forensics
- Network security
- Documentation of IOCs and security best practices
RECOGNIZED LEADERS IN MANAGED DETECTION & RESPONSE




RESOURCES
Learn more about MDR

Speak with an expert
Discover how you can solve your log management challenges in an honest and easy conversation with one of our cybersecurity experts.
SPEAK WITH AN EXPERT