MDR Security: What is it?
In this article, we'll deep dive into what MDR Security is,, how MDR works, as well as what makes an effective MDR solution.
Managed Detection & Response (MDR) services provide continuous visibility of your on-prem., cloud, SaaS, and endpoint environments through proactive threat detection and response activities.
What is MDR?
MDR stands for “Managed Detection & Response,” which includes all cybersecurity activities related to the continuous analysis, monitoring, identification, and remediation of a company’s risks, threats, and vulnerabilities across its on-prem., cloud, SaaS, and endpoint environments.
An MDR provider is a third-party service provider that acts as an extension of your organization’s in-house team, carrying out daily security operations and handling tasks including alert triage, validation, threat intelligence enrichment, threat hunting, and incident response. MDR providers use MDR tools, expert human analysts, and smart technology to help keep their clients safe and secure.
The best MDR providers have open and transparent communication with their clients, which enables them to collaborate with a company’s existing security team in real-time and to enrich each others’ work.
How does MDR Security Work?
Most MDR service providers help companies stay protected through the following cybersecurity activities:
- 24×7 security alert monitoring
- Automated enrichment
- Triage
- Detailed investigation and response activities
Some MDR vendors have dedicated teams with very specific types of expertise. At CyberProof, for example, nation-state level security analysts continuously enhance their work by leveraging up-to-date information provided by our teams for threat intelligence and threat hunting. MDR services provided by CyberProof’s teams involve a high level of collaboration with in-house experts, who enhance threat detection and allow SOC analysts to perform focused investigations and identify previously unknown threats.
What are the benefits of MDR?
You may be wondering exactly what is an MDR provider and exactly what value they can deliver in terms of reducing your organization’s risk of cyber-attacks. The truth is, advanced managed detection and response providers can bring incredible value to companies – both from a security perspective and from a business perspective – as they:
- Free up your security team’s capacity – They complement your staff so they can shift their focus to higher priority tasks.
- Offer guided remediation and investigation – They provide real-time analyst support via an orchestration & automation platform, such as CyberProof’s CDC platform supports real-time collaboration.
- Provide transparency into all cybersecurity activities through the Security Operations Center (SOC) – They offer full visibility into all activities performed by the provider’s analysts and by the client’s team.
- Understand the root cause of incidents – They quickly correlate multiple alerts into one incident to get to the heart of the threat or breach.
- Collaborate with experts – They enable multiple teams to collaborate in real-time, increasing the efficiency of responses to complex incidents.
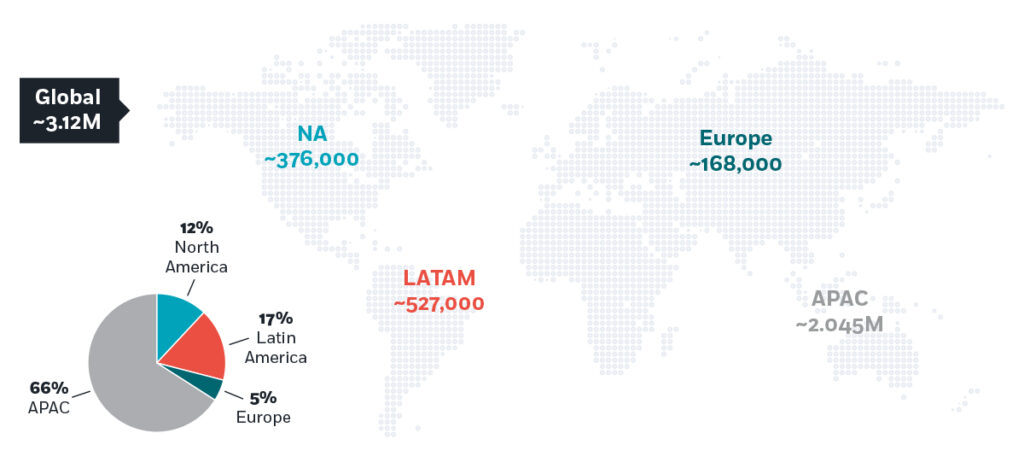
THE GLOBAL CYBERSECURITY SKILLS GAP, BY REGION
What Challenges can MDR Security Address?
As an organization transitions its assets from physical data centers to public cloud or multi-cloud infrastructures, security operations must also make the shift. Meaning that security operations also need to move to the cloud to allow cost-effective detection and response of threats.
Organizations can then migrate to the cloud with confidence, by working with an MDR service provider that has deep experience in helping complex, global enterprises transition to and manage their cloud-native security operations.
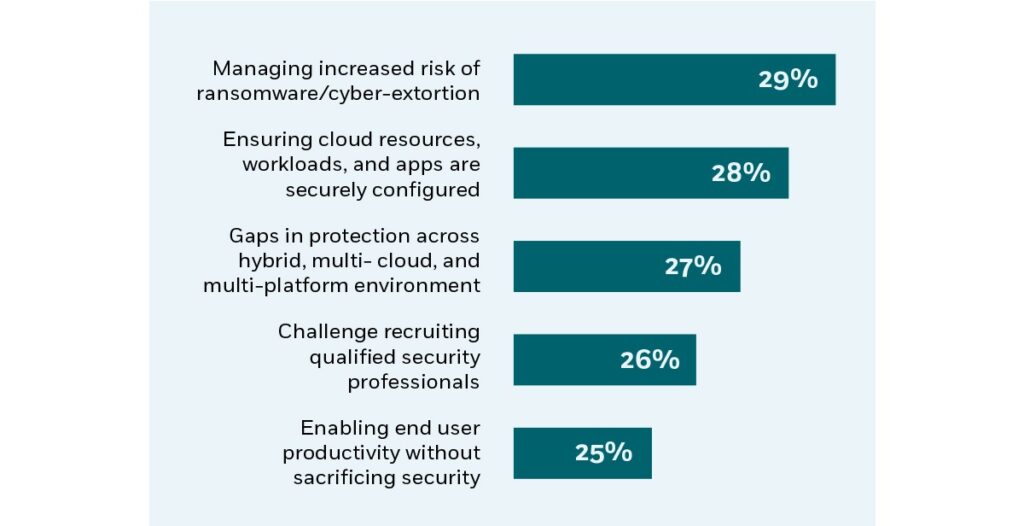
TOP 5 CYBERSECURITY CHALLENGES FOR CISOS
Why is MDR important? MDR tools, technology, and platforms
Facts are facts, and it may be impossible to prevent all cyber-attacks now and into the future. This is why MDR is crucial for organizations: they enable you to identify and remediate attacks quickly so that the impact of any single attack is minimal, at most, on the business.
But aside from prevention, MDR tools, technology, and platforms must be prepared to meet any challenges the future holds. Which is why companies should strongly consider MDR providers who incorporate AI/ML, cyber threat intelligence, analytics, collaboration, and human expertise to identify threats and then respond at maximum speed. These modern Managed Detection & Response services can help organizations create and implement highly effective cybersecurity strategies that improve their risk posture and enable them to effectively remediate threats.
What makes an effective MDR security solution?
An effective MDR solution is one that is delivered through a transparent Security Operations Center (SOC). This is because a transparent SOC enables real-time communication and collaboration between the MDR provider’s specialized cybersecurity experts, the client’s in-house security team, and stakeholders.
At CyberProof, for example, we have cybersecurity experts on staff with these areas of knowledge:
- L1 analysts
- L2 analysts
- SIEM engineers
- Digital Forensic and Incident Response (DFIR) specialists
- Threat hunters
- Vulnerability management experts
- Endpoint Detection & Response (EDR) experts
- Cyber Threat Intelligence (CTI) analysts
Many SOCs do not have access to this type of diverse expertise. But even if your SOC is composed exclusively of Level 1 and Level 2 analysts, you can still adopt this dual concept. You can develop a degree of individual expertise in several areas of cybersecurity and then leverage that expertise internally by promoting greater real-time collaboration.
To do so, first identify who on your team may be interested in learning new skills. Check who is interested in taking responsibility for a specific area of knowledge. For example:
- One of the analysts starts training in cyber threat intelligence – and starts providing information about IoCs to the rest of the team.
- Another analyst learns about threat hunting – proactively searching for information about threats, then creates a hunting hypothesis relevant to the environment.
- A third explores intrusion detection – learning to detect threats across data sets and identify exploitation attempts.
Next, you can begin leveraging the expertise of team members in daily SOC operations. It’s a question of definition, to some extent: when you have someone take responsibility for threat intelligence, for example, the team will turn to that individual with related questions. You can encourage and formalize this by integrating the existence of specific experts in your SOC’s standard procedures.
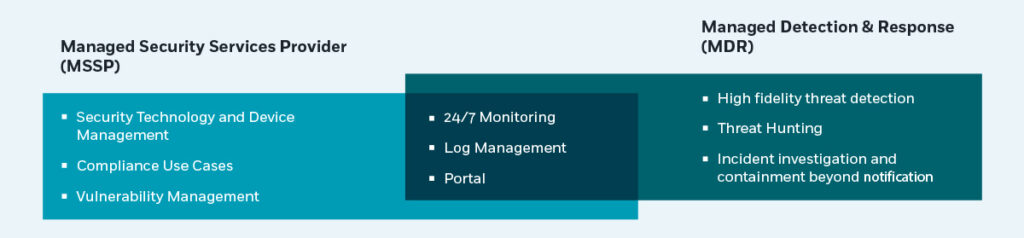
How do MDR providers compare with MSSPs?
In comparing MDR vs. MSSP services, be aware that some MSSPs offer very basic services. These types of companies generally rely on a team of analysts who monitor the SIEM, review alerts, and provide pre-defined responses (following a workflow) – without incorporating threat intelligence. The team reports on each problem or alert that comes up, but the burden is on the client to remediate it.
In some instances, an MSSP may conduct an initial investigation, determining if an alert is false or positive, but not more than that. When you need help handling more serious security issues, you need to look for vendors that are equipped to handle all types of cybersecurity activities and responses: including forensics, threat intelligence, computer security incident responses, and laboratories.
However, advanced managed detection and response providers like CyberProof, come with multiple internal teams that are dedicated to different areas of cybersecurity expertise or activities, and can integrate multiple resources to provide a real-time, collaborative response when a threat is detected. By getting to know an organization before a crisis occurs and working cohesively during an attack, top MDR providers can deliver a faster mean time to detect (MTTD) and mean time to response (MTTR), lower risk levels, and the business impact of an attack is minimized.
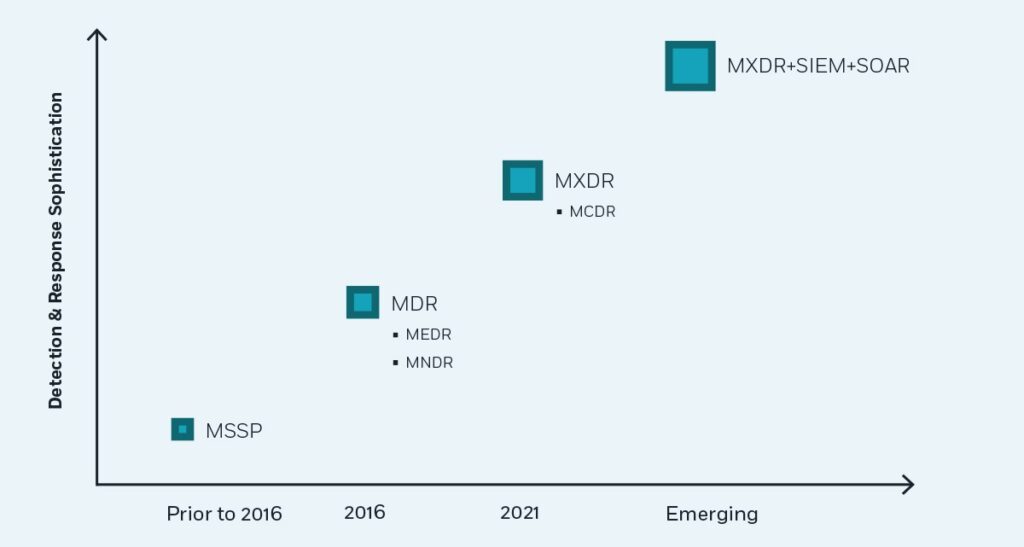
THE INDUSTRY SHIFT FROM MSSP TO MDR
What is the difference between MDR vs. XDR?
Advanced MDR solutions should support the planning, design, implementation, configuration, and optimization of EDR and SIEM based on each company’s specific business and technical requirements. No matter how mature your cyber defenses may be, they can help implement the appropriate cybersecurity solutions.
Moreover, MDR solutions should maintain continuous monitoring of EDR and SIEM alerts. They work with policies and custom detection rules that are based on the most recent threats for each industry, by proactively conducting historical searches of raw data collected by agents. They can also provide Extended Detection and Response (XDR) capabilities that offer the advantages of EDR and SIEM combined. XDR correlates telemetry across systems and detects and responds to incidents quickly, while hunting for threats that may have evaded detection.
An advanced MDR company should have this ability to incorporate XDR visibility from endpoint, network, and security log data – a key capability in detecting threats that may otherwise be missed – and in scaling the analysis of data collection.
What is the difference between MDR vs. EDR?
EDR stands for Endpoint Detection Response, a tool cybersecurity companies and teams use to protect specific endpoints. MDR, on the other hand, represents fully managed cybersecurity services delivered by an external provider. A company may use some EDR tools as part of their MDR services, but EDR is not a standalone solution.
Advanced managed detection and response providers may offer three tiers of services:
- Managed Detection and Notification (MDN) – Monitoring validated threats from any environment leveraging the SIEM, conducting an investigation, and providing notification.
- Managed Detection and Response (MDR) – Monitoring from any environment (endpoint, cloud, network) leveraging the SIEM and hunting, investigating, and responding to threats.
- Managed Endpoint Detection and Response (MEDR) – An enhancement to MDR services that includes a hunt & respond service at the endpoint to reduce dwell time and manages the EDR platform and contents.
THE EVOLUTION OF MSSP TO MXDR
Common managed detection and response scenarios
As enterprises migrate from on-prem. and legacy environments to cloud-native environments they open themselves up to new threats, endless alerts from multiple endpoints, and new vulnerabilities. This is often very stressful for companies trying to juggle their company’s fast-changing needs and requirements.
However, an advanced MDR service provider like CyberProof can provide the expertise necessary to transform your cyber defense with the Microsoft Security stack. For example, using a DevOps deployment model provides quick time to value by establishing customized Microsoft Sentinel infrastructures and Use Case content in just a few days.
Moreover, having an integrated orchestration & automation platform such as CyberProof’s CDC platform acts as a single pane of glass for security operations, integrating with both legacy SIEMs and cloud-native SIEMs such as Microsoft Sentinel. This allows organizations to take a phased approach while maintaining visibility of both on-premises and cloud security alerts and incidents.
MDR security features and capabilities - cloud-native security
Enterprise clients frequently ask: What is managed detection and response and how is it managed, in the context of transitioning to the cloud? Transitioning to cloud-native security is a complex process. In our experience, here’s some of what’s necessary to support this process:
- Advanced Data Engineering – Data engineers can set up a centralized, cost-effective data lake solution as part of your cloud-native monitoring infrastructure to enable the archiving, fast querying, and compliance of Big Data.
- Quick “time to value” using DevOps deployment – DevOps can use an Infrastructure-as-Code deployment model to establish Microsoft Sentinel infrastructures and pre-configured Use Case content, in just a few days.
- Log integration from any source – This is the key to maintaining an efficient, cost-effective cloud-native solution. At CyberProof, we’ve developed our CyberProof Log Collector (CLC) to connect all data types from any source not supported by default. The CLC improves the flow and handling of data, augmenting Azure Sentinel’s predefined rules and capabilities to provide customers with automated and dynamic threat detection.
- Continuous Improvement – Threats continue to emerge and these must be addressed. CyberProof has a unique Use Case Factory supported by a dedicated team of engineers and developers, who continuously identify and fill detection and response gaps with customized Use Case content – and a Use Case Catalog consisting of detection rules, digital playbooks, and third-party API integrations for response automation.
What to consider when selecting an MDR vendor
In considering different MDR Security platforms and vendors, you can define MDR providers’ work and evaluate the effectiveness of their capabilities based on the following qualities:
- Expertise: What is the quality of the team? Do team members have in-field knowledge and experience? What is their knowledge of the necessary processes? As there is currently a global shortage of security experts, not all vendors can offer the same high levels of expertise.
- Facilities: What physical facilities does the MSSP have at its disposal? Good physical facilities are crucial to support processes – and are particularly significant where a provider offers 24/7 support. Make sure a vendor has advanced facilities allowing effective communication internationally.
- Methodology: Some vendors focus on being cost-effective and function relatively superficially, maintaining a small team and supporting multiple clients. These vendors rely on standardized processes and their knowledge level of each customer is basic. Other vendors, however, invest time in learning about each client intimately. They offer a tailored cyber security strategy – taking advantage of threat intelligence, ChatOps, playbooks, and operations – to tune SIEM processes. At CyberProof, we believe effective cyber security protection needs this customized, in-depth work.
MDR services reviews and ratings
An MDR vendor should be able to offer the following capabilities, which successfully contribute to mitigating attack scenarios:
- CTI analysts that conduct research across the open, deep and dark web – The CTI team assists the SOC team in understanding whether any IOCs discovered in the network are part of attack campaigns. Ongoing collaboration with a CTI team enables the SOC to anticipate the attacker’s next steps and helps Threat Hunters obtain information that helps them search for evidence of attack in hidden areas of the network.
- Proven Threat Hunting methodology – Threat hunters play a critical role by searching across the client’s environment to find evidence of compromise, and providing feedback to the SOC to improve the organization’s security posture. It is important to have a defined methodology covering these phases:
- Data collection – including from the network, endpoint, cloud instances, email gateway, etc.
- Acquiring leads – including research from threat intelligence or incident reports.
- Developing a hypothesis – by working collaboratively to create a plan that is fully actionable.
- Executing the hunt – including the use of both live and historic data.
- Validation – of identified events.
- Providing feedback – to improve future security procedures.
- Centralized SOC delivery platform – An integrated SOC platform such as the CDC platform, which is integrated with existing security technology, enables multiple teams to collaborate in real-time. It helps the team capture relevant data and orchestrates response actions quickly.
About CyberProof’s Managed Detection and Response (MDR) services
Managed incident response should take advantage of the collective expertise of SOC analysts, threat intelligence experts, security specialists, and customer team members. It also should ensure full transparency, leading to better decision-making.
As an advanced MDR service provider, CyberProof uses MDR technology and Chat Ops collaboration to manage incident response and facilitate investigations and containment. Our global response team proactively handles incidents and collects data on all cybersecurity activities for analysis and reinforced learning, which leads to a continuous reduction in response time and the associated risk of exposure.
Our Managed Response services include:
- Incident handling, threat investigation and response
- Sandbox analysis of suspicious files
- IOC validation and extraction
- Customized threat detection rules, use cases and playbooks
- Proactive automated response and escalation
- Targeted threat reconnaissance and CTI reports
THE CYBERPROOF DEFENSE CENTER (CDC) PLATFORM
You can learn more about CyberProof’s advanced MDR Security services in our ebook: Migrating to Cloud-Native Threat Detection and Response

Frequently asked questions
What is MDR security?
Managed Detection & Response (MDR) security includes all cybersecurity activities related to the continuous analysis, monitoring, identification, and remediation of a company’s risks, threats, and vulnerabilities across its on-prem., cloud, SaaS, and endpoint environments.
What is the difference between EDR and MDR?
EDR stands for Endpoint Detection Response, a tool cybersecurity companies and teams use to protect specific endpoints. MDR, on the other hand, represents fully managed cybersecurity services delivered by an external provider. A company may use some EDR tools as part of their MDR services, but EDR is not a standalone solution.
What is the difference between SOC and MDR?
MDR stands for Managed Detection & Response services while SOC stands for a Security Operations Center. MDR services are often provided through the SOC, which is a dedicated security team and operations hub through which all cybersecurity events and data are handled.
What does MDR stand for in SIEM?
MDR, in fact, is not a part of SIEM. MDR stands for Managed Detection & Response services, which proactively searches for and investigates cybersecurity risks, threats, and vulnerabilities. On the other hand, SIEM stands for Security Information & Event Management – which is a reactive approach that involves analyzing collected data from security events.
What are MDR services?
Managed Detection & Response (MDR) services include all cybersecurity activities related to the continuous analysis, monitoring, identification, and remediation of a company’s risks, threats, and vulnerabilities across its on-prem., cloud, SaaS, and endpoint environments.
What is managed detection and response?
Managed Detection & Response (MDR) is the continuous analysis, monitoring, identification, and remediation of a company’s risks, threats, and vulnerabilities across its on-prem., cloud, SaaS, and endpoint environments.
What is managed endpoint detection and response?
Managed endpoint detection and response refers to the ongoing analysis, monitoring, identification, and remediation of cybersecurity risks and threats across networks and environments that are closest to the end-user, such as email accounts, social media accounts, smart devices (laptops, smartphones, tablets), and more.
How does an MDR work?
MDR works by using MDR tools, expert human analysts, and smart technology to monitor all security events across a company’s on-prem. and cloud environments, detect when threats arise and breaches occur, and remediate security incidents.

Speak with an expert
Explore how CyberProof can help you anticipate, prevent, and mitigate ever-evolving cyberattacks in hybrid and cloud-native environments.
SPEAK WITH AN EXPERT