What is incident response
CyberProof’s approach to mitigating cyber-attacks
Maintaining an effective incident response plan enables companies to respond to threats more quickly and minimize the business impact of cyber-attacks. This article explores the key components of incident response plan management and CyberProof’s approach to incident response.
What is an Incident Response Team?
An incident response team maintains an organization’s security best practices and responds to various types of cyber security incidents from cyber attacks to data breaches, and beyond.
The incident response team should include a variety of cybersecurity professionals with various roles and responsibilities so they can collaborate in a well-rounded, holistic approach to cybersecurity.
At CyberProof, for example, our team includes L1 and L2 Analysts, Threat Hunters, SIEM Engineers, and others.
How incident response planning mitigates the risk of cyber-attacks
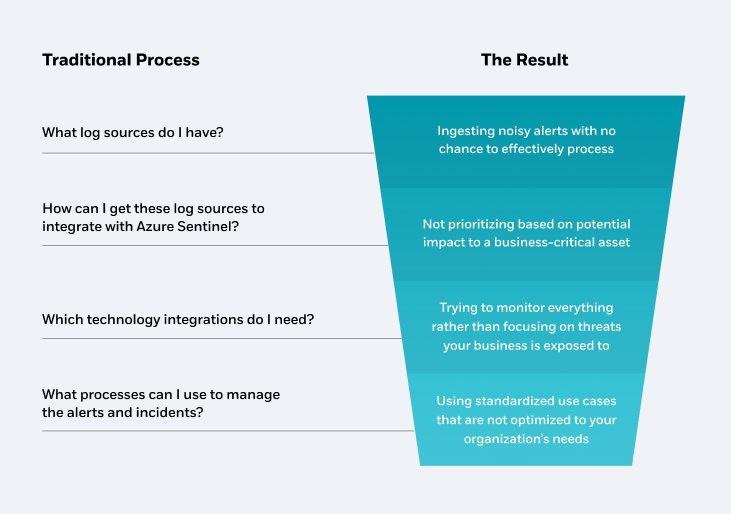
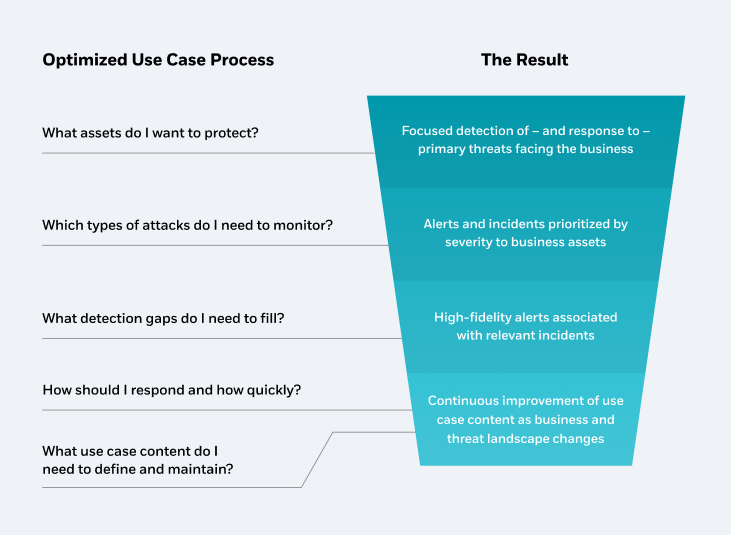
Incident response planning starts by developing use cases to define which types of threats need monitoring, and how to respond to different types of threats.
This is particularly important when onboarding new cloud sources that provide new attack surfaces. Use cases also help you evaluate which log sources from your legacy SIEM should be transitioned over to your cloud-native SIEM (for example, Azure Sentinel).
Unfortunately, use cases are frequently missed when organizations evaluate log sources, resulting in an escalating number of complex and noisy alerts for your security team. Done correctly, however, use cases make threat detection and response processes much easier to manage, while making the system more accurate and capable of mitigating threats more quickly.
Threat visibility using the traditional process
Threat visibility using an optimized use case process
Who is responsible for incident response?
SOC teams are typically those responsible for incident response as they consist of analysts with expertise in incident response services.
The following are just a few examples of the specific skills you should look for when hiring SOC team members:
- Program management – Highly organized managers with strong project management and stakeholder management experience. They should be able to put in place a governance and resource management plan when carrying out a large migration to cloud-based security monitoring infrastructures.
- Cloud forensics experts – Digital Forensics and Incident Response (DFIR) experts that specialize in cloud forensics – with the ability to identify digital evidence and artifacts in cloud infrastructure.
- Security Information and Event Management (SIEM) content engineering – Technically proficient engineers with experience creating custom analytics rules, queries, and dashboards. They should be able to leverage automation, hunting, and querying tools – along with their own processes to reduce the risk of an incident.
- SC-200 certified – Level 1 and Level 2 analysts that have been certified as having the required skills to mitigate threats across Microsoft 365 Defender, Azure Defender, and Azure Sentinel.
- Az-104 certified – Subject matter experts in implementing, managing, and monitoring cloud-native environments.
- Az-500 certified security engineers – Subject matter experts in implementing security controls and threat protection, managing identity and access, and protecting data, applications, and networks.
- Az-400 DevOps Engineers – Experts in designing and implementing Microsoft DevOps solutions using Infrastructure as Code (IaC) knowledge to continuously improve services.
Is outsourcing the answer to improving incident response?
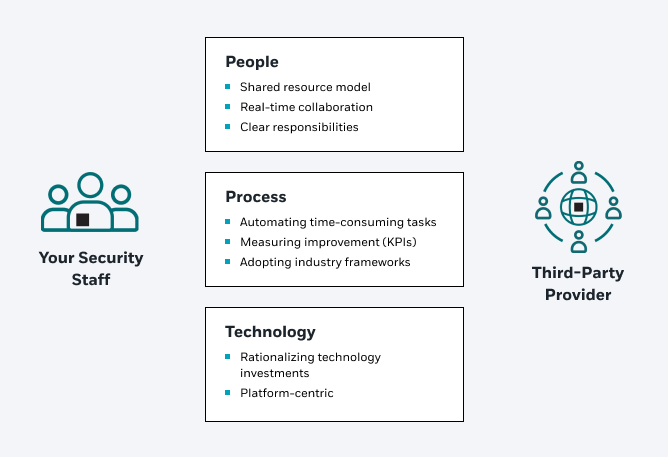
Not always. But if your current security team does not have these skills in place, you should consider working with a Managed Detection & Response (MDR) provider who has experts from these disciplines on their team and can bring their resources alongside yours to act as an extension of your team both in terms of day-to-day operational support and for compliance and governance.
This hybrid model (of internal security teams and an external MDR provider) uses tools and practices that enable transparent communication between internal and external teams, supplementing and extending your cybersecurity capabilities without requiring you to relinquish control.
Hybrid engagement model
Incident response platforms, technologies and tools
When building a new SOC or augmenting an existing SOC, you should consider incorporating key technologies to improve your enrichment, detection, and response capabilities, such as follows:
- Cloud native SIEM – With a cloud-native SIEM, there are no upfront costs, you pay only for what you use. Cloud-native SIEMs helps you collect data at a cloud scale across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds, and incorporates threat intelligence and other sources of enrichment.
- Automation and orchestration – Automation and orchestration capabilities include the collection of software solutions and tools that allow organizations to streamline security operations in three key areas: threat and vulnerability management, incident response, and security operations automation.
- Threat Intelligence – Threat intelligence is evidence-based knowledge about an existing or emerging threat to assets that can be used to inform decisions regarding the subject’s response to that threat. There are three levels of Threat Intelligence: Strategic, Operational, and Tactical. Strategic looks at the changes in the broader threat landscape and is primarily aimed at executives. Operational seeks to understand how an organization could be attacked by outlining Tactics, Techniques and Procedures (TTPs). Tactical covers the details of an attack with the shortest lifespan, such as Indicators of Compromise (IOCs) that are usually fed into the SIEM or firewalls.
- Threat Hunting – Threat hunters typically work assuming the network has already been breached. Threat hunting involves proactively searching for evidence of malware or attackers hiding within a network. However, threat hunting is not only about threat detection, threat hunters also help reduce the attack surface of an organization – improving the network’s security posture over time.
- Vulnerability Management – Vulnerability Management includes four stages: Vulnerability Scanning, Vulnerability Intelligence, Vulnerability Simulations (aligned to the MITRE ATT&CK matrix and Cyber Kill Chain methodologies), and Vulnerability Remediation.
- Endpoint Detection and Response – EDR combines real-time continuous monitoring and collection of endpoint data with rule-based, automated analysis and response capabilities. Integrating it with your SOC gives Security teams a centralized platform for continuously monitoring endpoints and responding to incidents as they arise – often via automated response.
Defining an incident response process
The incident response process defines how organizations manage potential cyber-attacks. This includes having a comprehensive incident response plan in place – one that covers both internal and external processes for handling and managing cyber security incidents as they happen.
An effective incident response plan should include periodic risk assessments, performing systematic analysis and containment for security breaches, and utilizing monitoring systems and dashboards to monitor and identify security incidents.
What are the incident response steps?
Adopting next-generation SOC components enables proactive detection and response, and helps your team maintain a detailed action plan, enabling them to respond quickly to an attack.
The process of implementing a smarter SOC includes the following incident response steps and layers of development:
- Define Log Collection – what needs to be included?
- Tackling the data side – collection, management, and storage.
- Security Analysis – leveraging the capabilities of a SIEM.
- Implement orchestration, automation, and collaboration.
Let’s explore these areas in more detail.
Incident Response Lifecycle
Incident response phases include:
- Log Collection
Building a smarter SOC first involves identifying which assets, tools, technologies, and applications need to be integrated. The log collection layer covers on-premises applications, cloud-hosted apps, and SaaS applications.
- Tackling the Data Side
Once the log collection layer is defined, it becomes possible to implement effective log collection, data management, and data storage.
At CyberProof, we leverage Azure Log Analytics and CyberProof Log Collection (CLC) SaaS technology to pull logs from all sources of data. These include a customer’s existing Microsoft investments – including on-premise, SaaS, and Azure assets – and existing Microsoft security controls that generate alerts across identities, endpoints, data and email, and cloud apps.
- Security Analysis
Conduct analytics using the SIEM, which utilizes detection rules in identifying anomalies while also monitoring whether your log sources are operating correctly.
Organizations are increasingly adopting solutions such as Microsoft’s Azure Sentinel – a cloud-native SIEM that supplies correlation, analytics rules, and the filtering of massive volumes of events to obtain high-context alerts.
- Orchestration, Automation, and Collaboration:
Increased adoption of orchestration, automation, and collaboration provides a key element to productivity. Greater orchestration allows the SOC to work faster in enabling incident resolution, and facilitates efficiency by supporting a centralized view of threat intelligence.
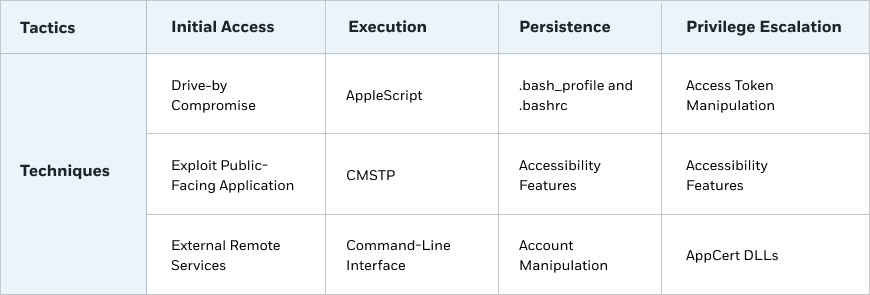
Incident Response Framework: The MITRE ATT&CK
The MITRE ATT&CK framework provides security experts and researchers with a common language for handling threats. The framework is composed of a comprehensive knowledge base of threat-related data, including tactics and techniques that attackers use to achieve their objectives.
Organizations can use this framework to perform both external and internal evaluations, and to provide guidelines for cyber defense teams to assess the vulnerabilities and security protocols that their companies face.
The matrix below details the various steps, tactics, and techniques used in the MITRE ATT&CK.
Incident response playbooks: Effective response processes
To maximize efficiencies and react quickly to threats, modern SOCs should implement automated enrichment and response activities using playbooks and computer security incident management workflows.
Level 1 analysts generally function as the alert triage team that is responsible for examining alerts, escalating those that may represent an attack. The work done by L1 analysts today mostly involves understanding context, making judgement calls about alerts, and escalating where necessary to L2 analysts.
CyberProof’s incident response automation capabilities
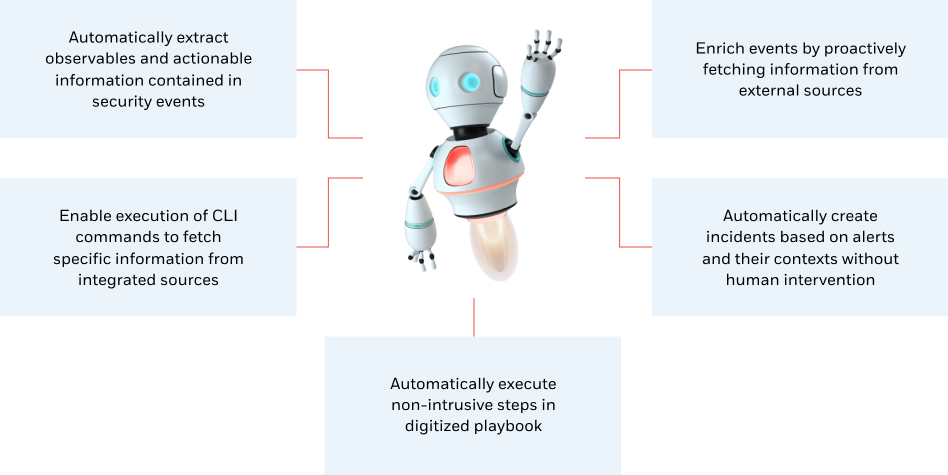
CyberProof’s CDC is a homegrown service delivery platform that provides customers with access to our IP in areas such as Automation, Orchestration, Collaboration and AI, but “as a service.” Our virtual analyst, SeeMo, takes much of the manual strain away from analysts by automating routine SOC tasks such as alert triage, event enrichment, investigation, issue containment and execution of response playbooks.
SeeMo, CyberProof’s virtual analyst
Incident Response Plan Management Use Case Factory
An effective component of incident response plan management is for SOC teams to continuously produce new and relevant use cases (aka attack scenarios). These use cases should include all aspects of the use case lifecycle.
Use cases should represent the outcome of an attack, or the outcome that an attacker seeks to achieve. This outcome should map to the MITRE ATT&CK Matrix Impact category. The use case “factory” should utilize a mix of various specialists and team members, for optimal outcomes.
CyberProof’s incident response service helps you transition to the cloud
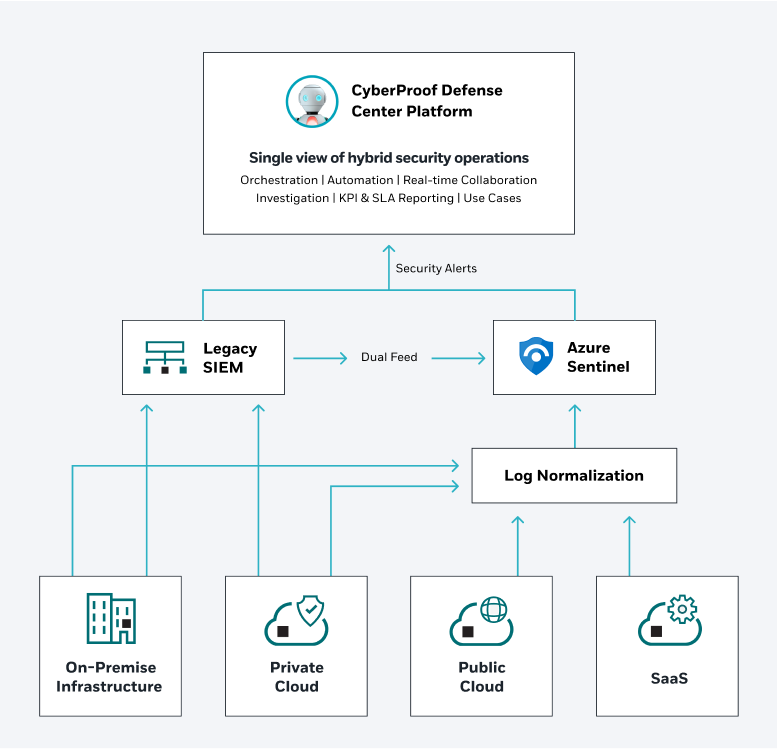
During the initial stages of the process of migrating to the cloud, it’s best to continue running your legacy SIEM in parallel to a staged version of Azure Sentinel. This way, you can dual-feed use case content from your legacy SIEM, including detection rules and security events, into the staged environment. You can test and tune this data without impacting the production environment.
Working with an MDR provider like CyberProof that has a centralized platform pre-integrated with Azure Sentinel helps significantly. At CyberProof, we leverage our home-grown CDC platform to help migrate from legacy tools to Azure Security platforms such as Sentinel and Defender. It acts as a single pane of glass before, during and after migration, ingesting and triaging alerts from SIEM, EDR, Vulnerability Scanning and Threat Intelligence Platforms and facilitating incident investigation and response.
What are incident response services at CyberProof
CyberProof provides a comprehensive solution to manage your incident detection and response intelligently. SeeMo, our virtual analyst, automates and accelerates your cyber operations by learning and adapting from endless sources of data. This allows our experts to prioritize the most urgent incidents and proactively identify and respond to potential threats.
In addition, CyberProof’s Defense Center (CDC) platform provides complete transparency of all cyber activities at any point in time, dramatically reducing the cost and time needed to respond to security threats, which ultimately minimizes their business impact.
We perform continuous monitoring of security events and triaging of alerts as they emerge in any of your environments, as well as a full suite of incident handling, security analytics, threat hunting, and managed response capabilities.
Frequently asked questions
What is an incident response?
What are the 7 steps in incident response?
What are the steps of incident response?
Why is incident response important?
What is an incident response plan?
What are the six steps of an incident response plan?
How do you write an incident response plan?
What are incident response procedures?

Speak with an expert
Explore how CyberProof can help you anticipate, prevent, and mitigate ever-evolving cyberattacks in hybrid and cloud-native environments.
SPEAK WITH AN EXPERT