Part 2 of 2
In part 1 of this blog we discussed how building a use case package requires specific skills – from building effective cyber security threat detection rules in the SIEM to defining robust playbook logic and powerful automation for faster response. This means a use case factory should be a mix of SIEM experts, security analysts, and automation specialists.
But what’s the process for developing a new use case? Let’s have a closer look.
Understanding the process
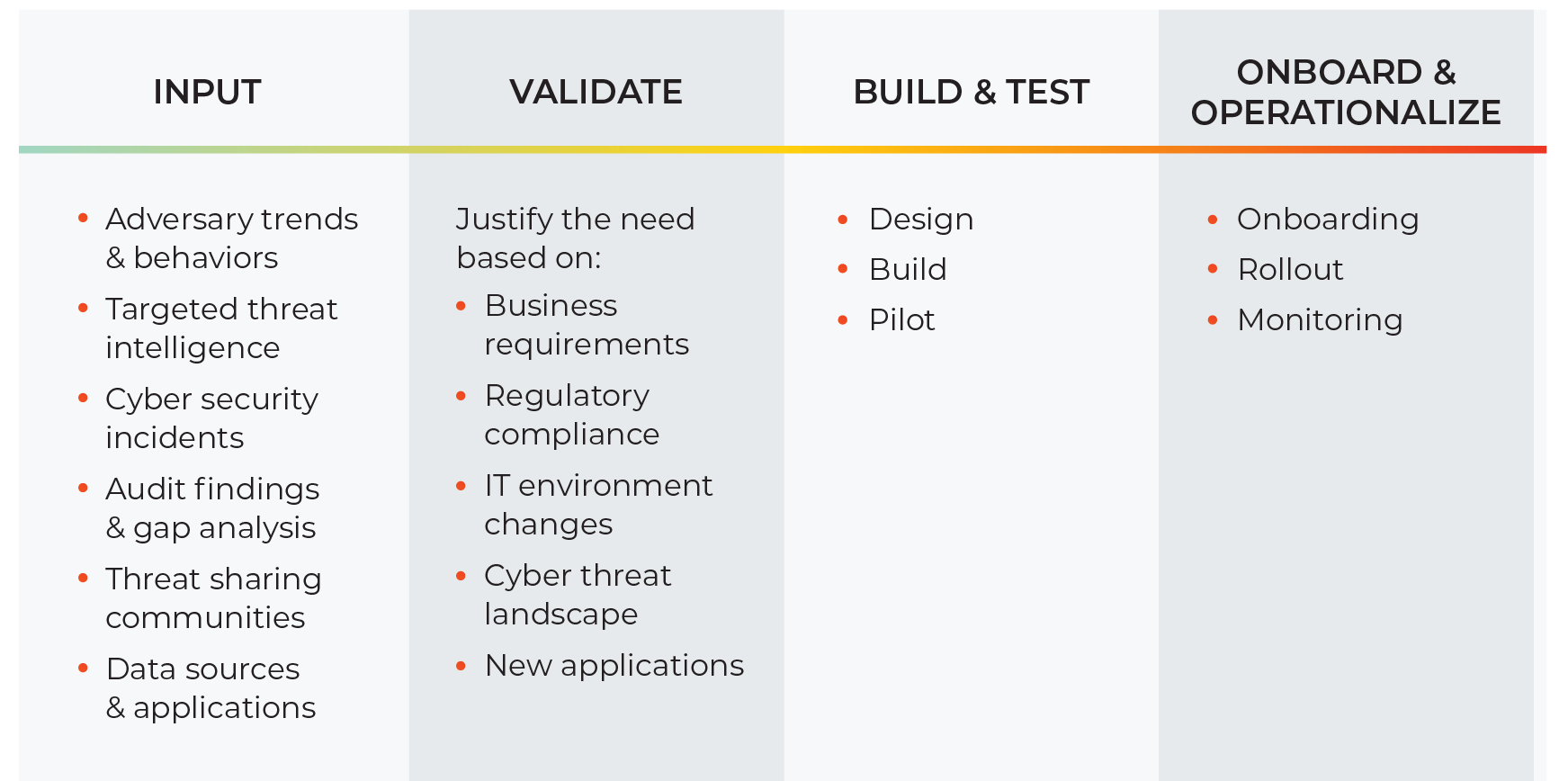
The development of a new use case involves an agile development process that includes the following steps:
1. Use Case Identification
The first step involves collecting information and analyzing the threat landscape as it relates to your organization:
- Evaluate your assets and establish which ones are the most critical.
- Develop a list of attack scenarios that could result in significant loss: data loss, integrity compromise, regulatory failure, etc. Prioritize these based on damage to the organization, then create a list of the most likely attacks.
- Start with a combination of threat detection rules (correlation rules in the SIEM) that relate to scenarios, which could result in significant loss. Screen this information against:
- Threat intelligence information
- Threat potential, i.e., do the tools exist to conduct the attack
- Preventative controls that are already in place.
In analyzing the threat landscape, the following kinds of information should be researched:
- Adversary trends and behaviors
- Targeted threat intelligence
- Cyber security incidents
- Audit findings and gap analysis
- Threat sharing communities
- Data sources and applications
For an SOC (Security Operations Center) to obtain the necessary information requires its integration with a wide variety of external technologies – in addition to having internal sources of information. At CyberProof, these external integrations are handled via the CyberProof Defense Center, a security orchestration, automation and response (SOAR) platform.
2. Validating the Business Case
The second step involves establishing that the use case will add value and solve the problem. This part of your cyber security strategy should focus on defining the objectives and identifying the threat detection gaps that justify the need for the use case development.
Define the objectives and identify the threat detection gaps that justify the need for the use case development.
The justification for developing a particular use case may relate to:
- Business requirements
- Regulatory compliance
- IT environment changes
- Cyber threat landscape
- New applications that need to be monitored
Validation of a new use case is crucial in gaining buy-in from the organization’s stakeholders – who must later review and approve the development of the use case – its design, build, and pilot.
3. Design, Build, Test
Once the stakeholders have approved development of a use case, it’s time to move ahead with development:
- Design: Identify data sources, define correlation logic, finalize enrichments and external feeds, analyze integrations and automations, develop incident workflow and playbooks, decide on dashboards and report, and agree on a deployment plan.
- Build: Create threat correlation and queries, configure alert content, integrate enrichments, establish a digital playbook and automation processes, and set up dashboards & reports.
- Test: Test the use case in a staged environment, validate the enrichment process, verify digital playbooks, finalize dashboards & reports, and get stakeholders to sign off.
4. Onboarding, Rollout, Monitoring
Once the use case is ready, pilot it for select environments and approve it for rollout. Continue to monitor the use case and begin an ongoing process of fine tuning, maintenance, and optimization.
Here’s an example of a use case that’s “in operation” in CyberProof’s CDC:
Maximize your Organization’s Cyber Health!
In the context of a traditional cyber security risk assessment process, the Use Case Factory is an effective means of regularly ensuring the agile development of new use cases that add business value to your organization.
Implementing a Use Case Factory process – which guides everything from effective selection and design of use cases to successful implementation – provides the means for keeping security operations up to date and allows you to identify and respond to cyber security threats fast enough to mitigate business damage.
Want to learn more? Read Part 1 of this post – and contact CyberProof for more information about building a Use Case Factory for your organization.