The retail sector has been reeling from a wave of cyberattacks, with grocery retailers particularly hard hit. Recent months have seen an alarming acceleration in attacks across the grocery-retail industry worldwide—from ransomware campaigns against UK major food retailer like Co-op1 to supply chain disruptions in North America that left Whole Foods shelves bare.2 Some of the most active threat actors groups in 2025—including Qilin, Play, Safepay, Akira, and Scattered Spider—have all turned their attention to the food sector, showing how widely this industry is now being targeted.
The question now is not just how companies protect themselves at an organizational level, but how entire countries should address the systemic risk of cyberattacks on food distribution networks.
The Grocery Retail Industry in the Crosshairs
Imagine walking into your local grocery store only to find empty shelves, frustrated customers, and apologetic staff explaining that a cyberattack has disrupted their entire supply chain. This is no longer a hypothetical scenario—2025 has seen multiple incidents where ransomware and data breaches directly affected food retailers and distributors, leaving communities without access to essential goods. What once might have been viewed as an IT problem is now a pressing issue of food security. As grocery supply chains become increasingly digitized and interconnected, they have become prime targets for cybercriminals who know that disrupting food distribution delivers immediate and widespread impact.
Grocery companies are attractive targets for several reasons:
- Ransom leverage – Disrupting food access affects every consumer, giving attackers maximum leverage. The perishable nature of grocery inventory means even brief disruptions lead to direct financial loss, while minimal stock buffers make shortages immediately visible.
- Low security maturity and investment – Grocers have historically underinvested in cybersecurity compared with sectors like finance or tech, partly because thin operating margins make large-scale investment difficult to justify. 3
- High-value data – Loyalty programs, payment information, and supplier contracts provide lucrative monetization opportunities for attackers.
- Legacy systems – Outdated point-of-sale and ERP platforms remain common, often unpatched and unsupported.
- Rapid digitization – Grocery retailers accelerated digital transformation during the COVID-19 pandemic, but the speed left exploitable gaps. Payment systems, loyalty apps, and delivery platforms handle large volumes of sensitive data, while even simple actions like scanning QR codes can be abused without safeguards. Contactless payments, mobile ordering, and IoT-enabled refrigeration further expanded the attack surface faster than defenses matured.
The result is a perfect storm: threat actors know that downtime quickly leads to spoiled goods, lost sales, and angry customers—pressure points that increase the likelihood of ransom payments. This ongoing trend of cyberattacks targeting grocery retailers and distributors shows no signs of slowing down.
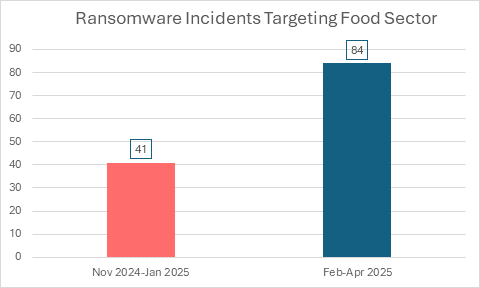
Fig. 1: Ransomware incidents in the food sector doubled between Feb–Apr 2025 compared to the previous quarter.4
Case Study: UNFI and the Ripple Effect Across North America
United Natural Foods Inc. (UNFI), the primary distributor for Whole Foods Market, suffered a ransomware attack in June 2025 attributed to the Scattered Spider group. The breach was discovered on June 5, when attackers used phishing and impersonation tactics, posing as IT staff to trick employees into resetting credentials and logging into fake portals. This allowed the group to steal data and deploy ransomware, forcing UNFI to shut down its entire network across 52 distribution centers. Order processing and shipment systems were taken offline, leaving perishable sections at Whole Foods empty, smaller grocers without deliveries, and even U.S. military commissaries facing shortages. UNFI operated manually for several days before restoring its primary electronic ordering systems by June 16, with core systems largely normalized by June 26. 5
The financial toll was severe—up to $400 million in lost sales, $60 million in net income impact, and $25 million in remediation costs. But beyond the numbers, the attack underscored the fragility of just-in-time food distribution. A single compromise rippled across tens of thousands of retail locations, exposing how ransomware groups can leverage basic social engineering and credential theft to create cascading disruption in critical supply chains.
Case Study: Co-op and Empty Shelves Across the UK
In April 2025, Co-op, the UK’s fifth-largest food retailer, was hit by a sophisticated ransomware attack attributed to the DragonForce group, linked to the Scattered Spider collective. The intrusion began around April 22 through social engineering tactics, with attackers even contacting Co-op’s security leadership directly via Microsoft Teams and phone calls. This access allowed the exfiltration of personal data from roughly 20 million customers, including names, addresses, emails, phone numbers, and dates of birth. While the company avoided full ransomware encryption by disconnecting networks, the breach still exposed data belonging to 6.5 million active members, triggering significant privacy concerns and reputational fallout.
The operational disruption was equally severe. Co-op stores across the UK experienced stock shortages and service interruptions. The company ultimately reported a $275 million revenue hit, and unlike the UNFI breach, which rippled outward from a single distributor, the Co-op incident demonstrated the fragility of frontline retailers themselves. When a major chain goes offline, the effects are immediate and highly visible: empty shelves, long queues, and communities left without reliable access to food. 6
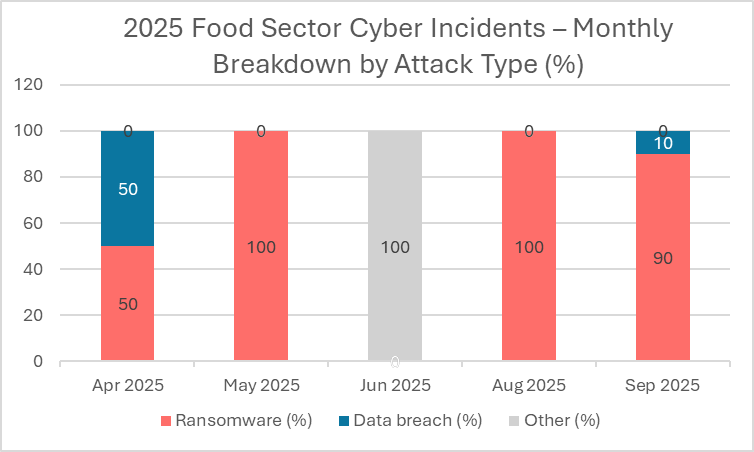
Fig. 2: Ransomware accounted for the vast majority of food sector cyberattacks in the past six months, peaking in September 2025.
Recommendations:
To meet the escalating threat, both companies and regulators need to embrace resilience as a core principle. Key recommendations include:
- Employee awareness: Expand training against phishing and social engineering, which remain primary attack vectors.
- Invest in modernization: Replace legacy payment systems and ERP systems with secure, cloud-ready platforms.
- Sector-wide collaboration: Share intelligence and best practices across retailers, distributors, and regulators.
- Diversify suppliers: Reduce dependency on single distributors by maintaining contingency partnerships.
- Recognize criticality: Position grocery retail alongside energy and healthcare in national security frameworks.
Conclusion: The Grocery Aisle as the New Frontline
Cyberattacks on the grocery retail industry are no longer isolated IT issues—they are societal risks. Empty shelves, supply chain breakdowns, and community hardship all highlight the consequences of treating cybersecurity as optional.
Cybersecurity in grocery retail can no longer be left to individual companies. Attacks on food distribution create national-level risks, raising the question of how governments should step in. In the United States, lawmakers introduced the Farm and Food Cybersecurity Act of 2025, mandating sector-wide risk assessments and training. In the UK, discussions around NIS2 and broader critical infrastructure protections now explicitly include food distribution alongside energy and telecom. This shift reflects a new reality: grocery retail is critical infrastructure. Just as regulators oversee utilities and banks, they must now ensure food supply chains can withstand cyber disruption. 7 8
The stakes are as basic as they come: ensuring that communities can put food on the table. If 2025’s wave of grocery disruptions has shown us anything, it is that cybersecurity is now inseparable from food security.
References
- https://www.bbc.com/news/articles/cze1eg3z307o
- https://edition.cnn.com/2025/06/10/business/whole-foods-cyber-attack-unfi
- https://cyberscoop.com/united-natural-foods-cyberattack-400-million/
- https://therecord.media/ransomware-attacks-food-and-ag-double-2025
- https://www.grocerydive.com/news/unfi-cyberattack-response-supply-chain-grocery-wholesale/750831/
- https://therecord.media/retailer-the-co-op-cyberattack-lost-revenue
- https://industrialcyber.co/regulation-standards-and-compliance/farm-and-food-cybersecurity-act-reintroduced-to-protect-food-supply-chain-from-cyber-threats/
- https://nis2directive.eu/foods/