Contributors: Prajeesh Sureshkumar, Niranjan Jayanand
Executive Summary
A multi-factor authentication (MFA) attack, often called MFA fatigue or MFA bombing, is a social engineering technique where attackers repeatedly spam a user with MFA requests, such as push notifications to their mobile device, hoping to overwhelm them. The goal is to trick the user into blindly approving one of these requests, granting the attacker unauthorized access to their account.
In July 2025, CyberProof SOC analysts identified a user account that was compromised from a phishing attack, followed by successfully logins with MFA satisfied using Mobile app notifications. Audit logs revealed no suspicious activity, and all authentication attempts were successful using the correct password and mobile-based MFA.
This article details the techniques used for MFA attacks and the recent investigation into such an attack.
Technical Details
The incident investigation started after a CyberProof SOC analyst received an alert regarding suspicious sign-in activity for a user account originating from a Cloudflare IP address. During initial triage, several red flags emerged including:
- The user’s reported location matching the IP location
- The IP not being associated with any known proxy or VPN services
- The sign-in being completed using the correct password with MFA successfully satisfied via a mobile app notification
Further investigation confirmed that the victim clicked on a suspicious SharePoint URL (as shown in Fig 1).
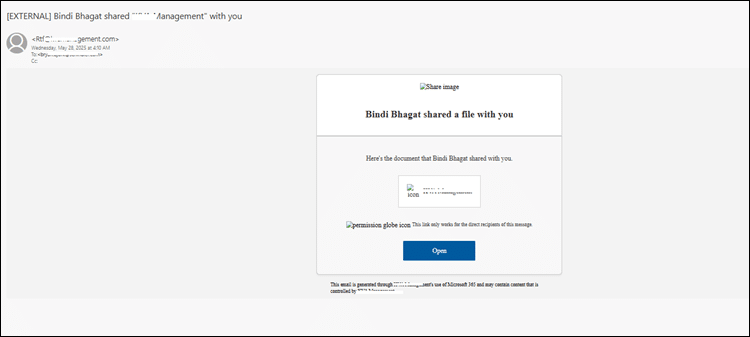
Fig. 1: The phishing email sent by the attacker
CyberProof SOC analysts were swift in taking action but faced challenges after learning that the attacker has moved leading to 404 error.
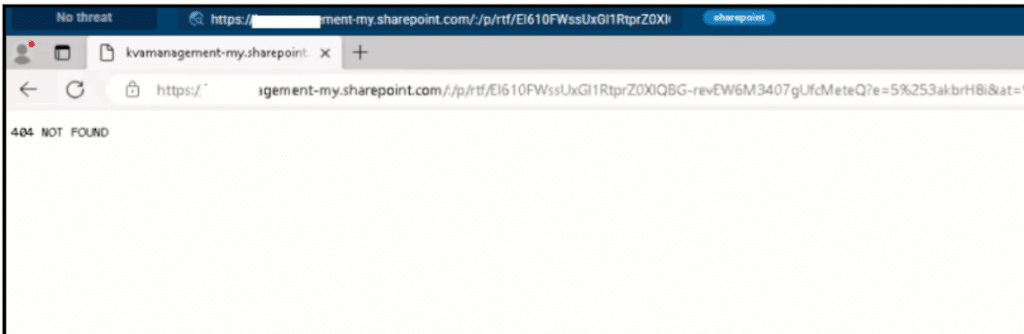
Fig. 2: 404 error on the SharePoint Page accessed by the user
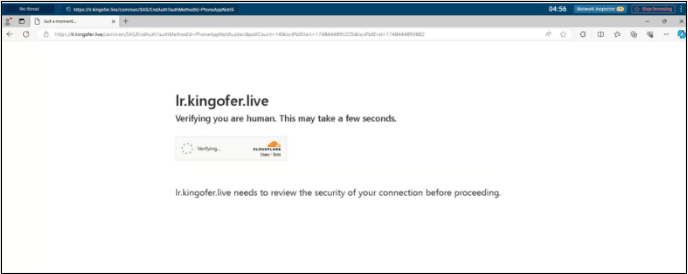
Fig. 3: Phishing site hosted via a SharePoint site
Further analysis confirmed the phishing page hosted on SharePoint, was indeed used to steal usernames and passwords. After the target/victim’s username and password was collected by the attacker, the attacker performed SSO via SAS (Session Authentication Service). This is followed by multiple poll request sent to the target/victim by the attacker intentionally to overwhelm the user as shown below.
The moment the user accidently approves the request the account is taken over. The below image clearly shows the attacker sent 14 poll requests to the user, leading to approval and account compromise.
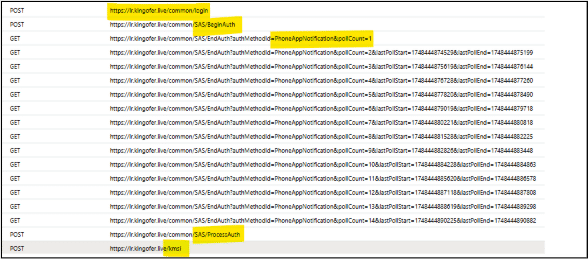
Fig. 4: Poll requests send by the attacker to the target.
Challenges Faced by SOC Teams
MFA fatigue attacks don’t leave any traditional IoC’s. SOC analysts often rely on alerts from security product platforms which are the usual investigation triaging starting point. In this case:
All sign-ins originated from the user’s usual location, with no evidence of VPN usage. Audit logs revealed no suspicious activity, and all authentication attempts were successful using the correct password and mobile-based MFA.
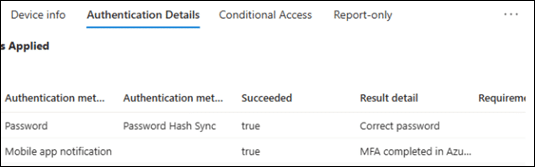
Fig. 5: Successful bypass of MFA
These factors can lead analysts to believe there is no indication of compromise, potentially allowing the attack to go unnoticed.
Remediation Actions
In the event of a security compromise, a swift and decisive response is critical to contain the threat and restore the integrity of the affected systems and accounts.
These actions are highly recommended immediately after an MFA attack is suspected:
- Immediately revoke user sessions and reset password.
- Require MFA re-registration in case any new authentication methods or MFA is added
How to Defend MFA Push Abuse/ MFA Fatigue
Proactively defending against these sophisticated social engineering attacks requires a multi-layered approach that combines heightened user awareness with robust technical controls.
Here are some common best practices to consider:
- Creating Awareness:
Educate users about the risks of phishing and MFA fatigue attacks and the importance of reviewing all push notifications before approving them. - Strong Passwords and Credential Hygiene:
Enforce strong password policies and discourage the reuse of passwords to minimize the risk of credential theft. - Consider Alternatives:
Implement more secure MFA methods like FIDO2 compliant authentication or security keys, which are less vulnerable to MFA fatigue attacks. - Use Privileged Identity Management (PIM):
For high priority accounts and high-risk accounts implement PIM - Enabling Conditional Access Policy:
Block logins or MFA from risky locations, malicious or untrusted IPs







