This is part 1 of a 2-part series about the advantages of working with a Managed EDR provider.
With the adoption of digital transformation combined with the rapid move to remote work due to COVID-19, the security perimeter has dissolved. Attackers are leveraging this changing IT landscape to launch cyberattacks involving highly sophisticated tools, and by employing various tactics, techniques and procedures (TTPs).
Businesses should look at security architecture that shrinks the blast radius to reduce the potential of a cyberattack. This need is encouraging organizations to embrace the Secure Access Service Edge (SASE) model to secure their networks and systems – converging network and security into a single, cloud-delivered service model. Protecting end user compute devices and servers is still a vital component in their overall security strategy.
In this complex IT environment, enterprises that are considering the implementation of Endpoint Detection & Response (EDR) are facing three primary challenges: complexity, cost and a shortage of skilled experts. Let’s take a “deep dive” into each of these challenges.
Enterprises that are considering the implementation of Endpoint Detection & Response (EDR) are facing three primary challenges: complexity, cost and a shortage of skilled experts.
Challenge 1: Complexity of Implementation
Security tools have played a cat & mouse game to protect organizations from cyber threats. New security tools were developed to keep pace with new forms of attacks. This resulted in businesses deploying multiple security controls and developing complex, layered security architectures. Modern day attacks leverage this complexity to slip through defences.
Endpoint security is one of the security controls that is part of the overall SecOps security strategy. Protecting endpoints with traditional Antivirus (AV) solutions worked on file and signature-based detection capabilities, but attackers found evasion techniques that bypassed these tools. Next-Gen AV then detected threats that used Artificial Intelligence/Machine Learning (AI/ML) detection capabilities. These tools proved inefficient in spotting highly sophisticated attacks such as supply chain attacks .
EDR is an evolution of these tools that helps to detect & respond to highly advanced cyber threats, reducing risks to the businesses. EDR requires careful planning and execution and may require extensive resources to build and operate the platform. This is often seen as a challenge for businesses looking to secure their endpoints.
EDR requires careful planning and execution and may require extensive resources to build and operate the platform.
Challenge 2: Cost
EDR is a huge leap from Next-Gen AV (NGAV), and it requires highly skilled resources to design, implement and operate. The platform provides in-depth insights into an endpoint from a network, user, file and process perspective that help detect Indicators of Attack (IOA).
EDR is a huge leap from Next-Gen AV (NGAV), and it requires highly skilled resources to design, implement and operate.
The tool generates a huge amount of telemetry related to these components that must be analyzed and correlated to detect suspicious behavior, provide actionable information to block malicious activity, and mitigate against cyber-attacks. If not implemented and operated properly, EDR can prove costly to an organization and reduce the organization’s effectiveness in protecting itself against cyber threats, leaving it more vulnerable.
Challenge 3: Skills Shortage
EDR solutions are feature rich and have various implementation models – cloud-hosted, or cloud-native, for example. Endpoint sensor deployment models can vary, too.
EDR solutions provide detailed telemetry of events occurring on the endpoint. To leverage the full potential of the solution requires highly skilled security personnel.
-
The design and rollout of EDR sensors requires a team of IT experts to help with rollout of the security sensors.
-
There is a need for 24/7/365 staff to continuously monitor and investigate alerts and detect suspicious activity.
-
A high level of configuration and tuning is required to ensure the tool is generating true positive alerts and eliminating all the false positives that often lead to alert fatigue.
Highly skilled cybersecurity staff increases the cost of running a security function. Moreover, the cyber security skills shortage and high employee churn rate in the security domain makes it difficult to find, train, and retain the staff.
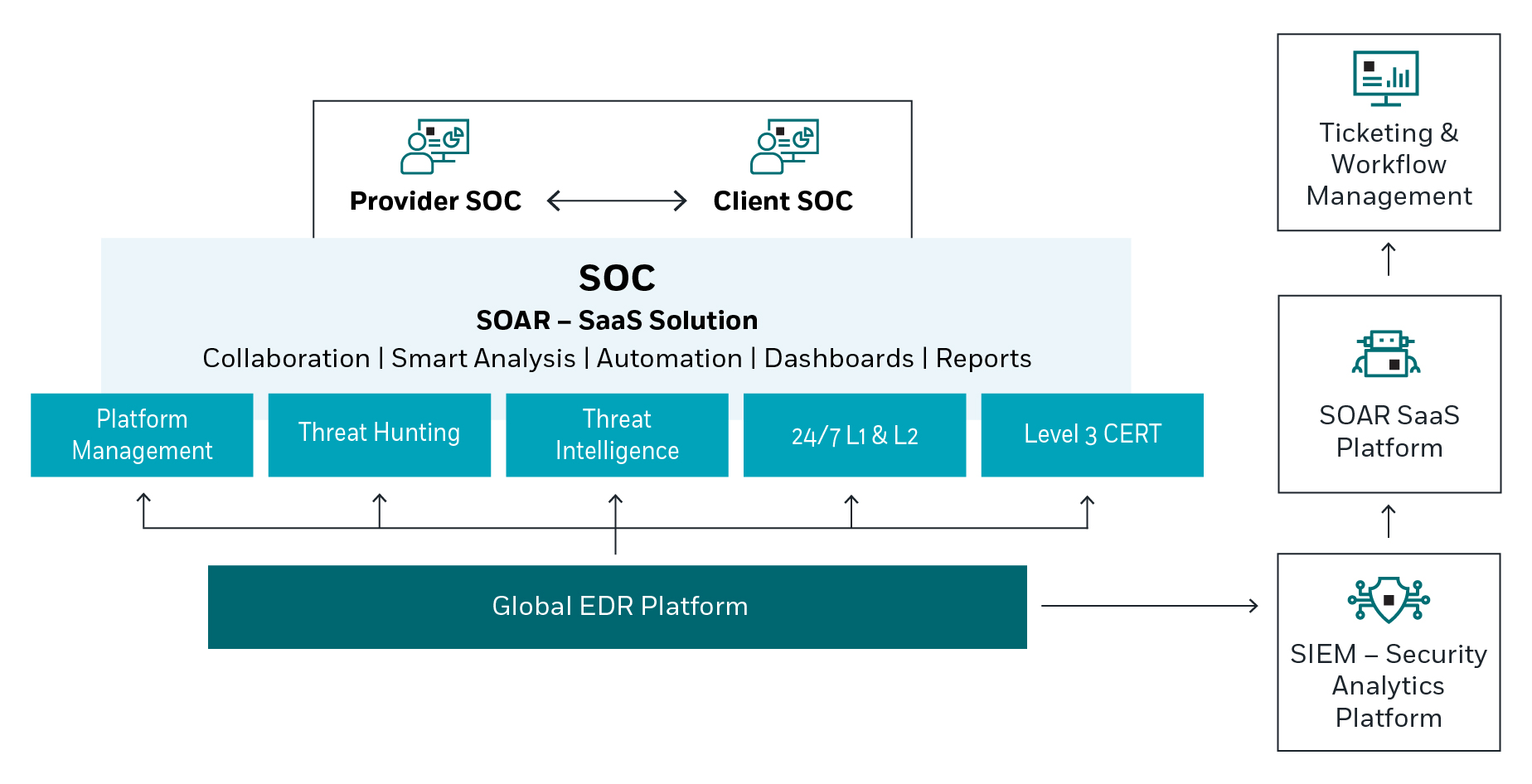
The value of working with a Managed EDR service provider
Gaining visibility and control into endpoint devices to detect & respond to threats is one of the quickest ways for security operations (SecOps) to improve an organization’s security posture. Implementing an EDR solution can provide that visibility and detection capability. Traditionally AV and NGAV solutions served the purpose of protecting endpoints but, today, they are not enough to provide protection against Advanced Persistent Threats (APT). Organizations need to implement EDR solutions to detect and respond to cyberattacks.
Managed EDR Solution
Gaining visibility and control into endpoint devices to detect & respond to threats is one of the quickest ways for security operations (SecOps) to improve an organization’s security posture.
Cloud adoption has brought huge benefits to organizations, making use of technologies like Docker and Kubernetes applications can now be deployed and scaled with great efficiency. Applications can be built and rolled out at scale instantly. Securing containers and the life cycle of DevOps is also crucial to protecting an organization’s cloud assets. When choosing an EDR vendor, make sure the vendor offers support for Kubernetes security.
The complexity and burden of managing and orchestrating alerts from EDR and many other point products is a real challenge. Each security solution may have its own team and management console, often leading to layered security solutions to provide a defense-in-depth strategy. Attackers use different entry points into IT systems; when one team spots an alert on its own, it may look trivial – but connecting multiple alerts from different security tools can shed light on a bigger picture and help spot attacks faster. A Managed EDR (MEDR) service can be valuable when it comes to detecting & responding to attacks faster and minimizing the risk of a cyberattack and providing better Return on Investment (ROI).
Interested in speaking to our experts about Managed EDR services? Contact us today!