Updated: July 28, 2025
Contributors: Kithu Shajil, Niranjan Jayanand, Veena Sagar, Anagha Prabha
Executive Summary
On July 19, 2025, security researchers and enterprise defenders began tracking a large-scale exploitation campaign targeting on-premises Microsoft SharePoint Servers (CVE-2025-53770), as first reported by Eye Security.
On July 19th, Microsoft confirmed that a zero day vulnerability impacting on-premises Microsoft SharePoint Servers, dubbed “ToolShell” (by researcher Khoa Dinh @_l0gg). CVE-2025-53770 has been added to CISA’s Known Exploited Vulnerabilities (KEV) catalog on July 20, 2025. Successful exploitation of this vulnerability leads to installation of “ToolShell” that can provide unauthenticated access to systems and enable malicious actors to fully access SharePoint content, including file systems and internal configurations, and execute code over the network.
CyberProof researchers have identified and blocked multiple attacks as early as 17 July, where different probing IPs attempting to exploit this SharePoint vulnerabilities as reported in this blog. Researchers also identified Linen Typhoon, Violet Typhoon, and Storm-2603 had in fact started using the two flaws (CVE-2025-49706 and CVE-2025-49704) as zero-days, based on its investigation into ongoing attacks on SharePoint Servers.
The vulnerabilities impacting SharePoint can give away attackers to execute arbitrary commands on vulnerable versions and are tagged as:
- CVE-2025-49704
- CVE-2025-49706
- CVE-2025-53770
- CVE-2025-53771
Affected Products
These vulnerabilities affect on-premises installations of:
- Microsoft SharePoint Server Subscription Edition
- Microsoft SharePoint Server 2019
- Microsoft SharePoint Server 2016
- Microsoft SharePoint 2010 and 2013 may also be affected by these vulnerabilities
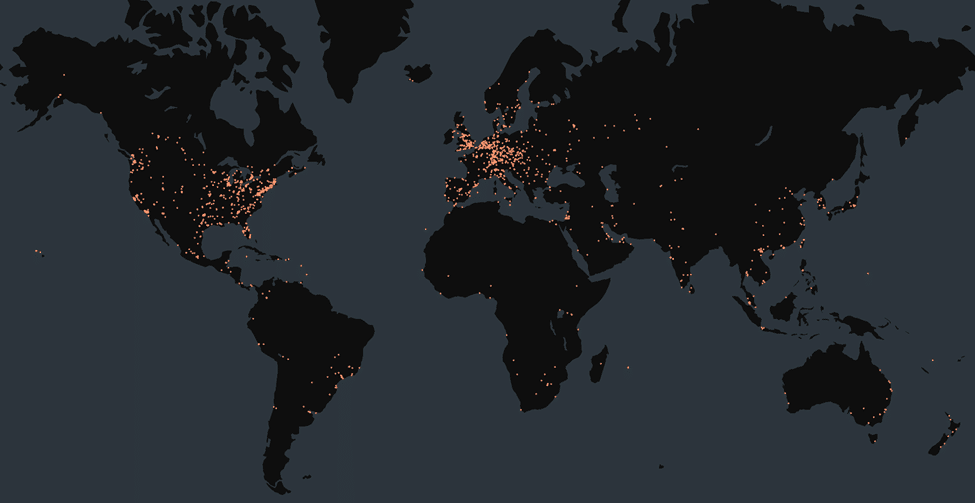
Censys shared below view of global distribution of vulnerable SharePoint servers on 22nd July:
Vulnerability Overview: The SharePoint Attack Chain
This exploitation chain involves multiple steps and have observed threat actors combining these CVEs to gain unauthorized access, execute code, and persist within SharePoint servers:
CVE-2025-49704:
- Type: Unauthenticated File Upload
- Allows arbitrary .aspx files (webshells) to be written to accessible paths
- Commonly used to drop initial foothold files like spinstall0.aspx
CVE-2025-49706:
- Type: XAML Deserialization
- Enables post-auth remote code execution (RCE)
- Used to invoke encoded PowerShell commands via trusted system APIs
CVE-2025-53770:
- Type: Authorization Bypass
- Allows attackers to elevate privileges or access internal SharePoint functions without proper access controls
CVE-2025-53771:
- Type: Input Validation / Path Traversal
- Used to overwrite or plant files in sensitive directories, aiding persistence
The kill chain diagram below shows the post exploitation view in Microsoft Defender:
Svchost.exe
└── w3wp.exe (IIS worker process)
└── cmd.exe /c powershell -EncodedCommand […]
└── powershell.exe
└── interacts with spinstall0.aspx
The below two images shows two instances of SharePoint vulnerability exploitation caught from our telemetry to help security analyst know what to look for and infer at.
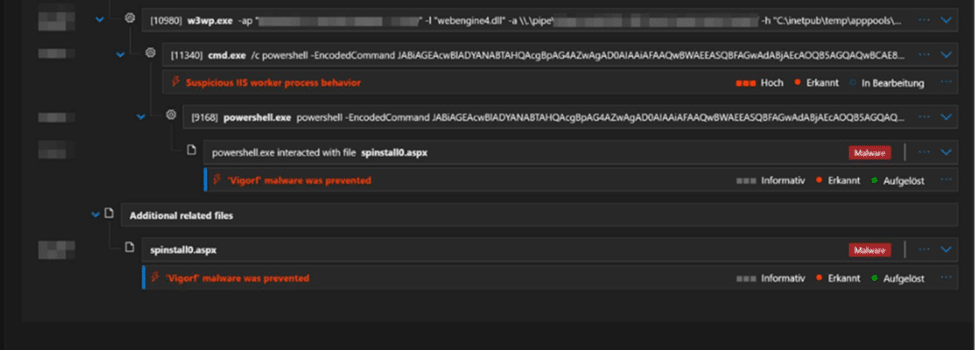
Figure 1: Observed attack against a manufacturing company
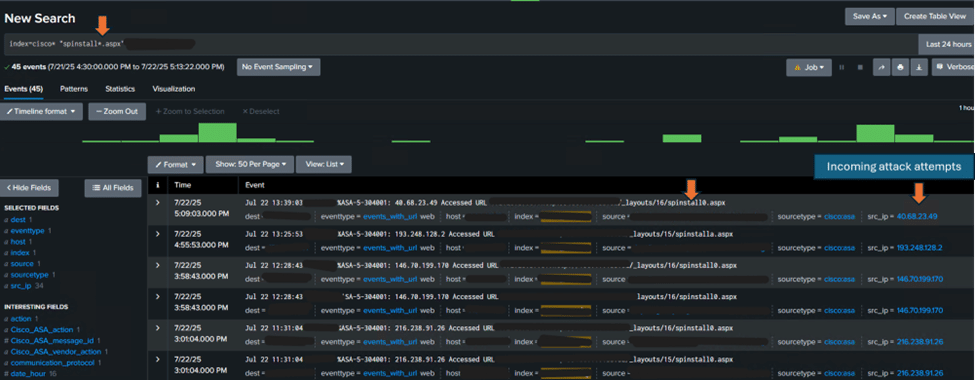
Figure 2: Observed attack against a financial firm
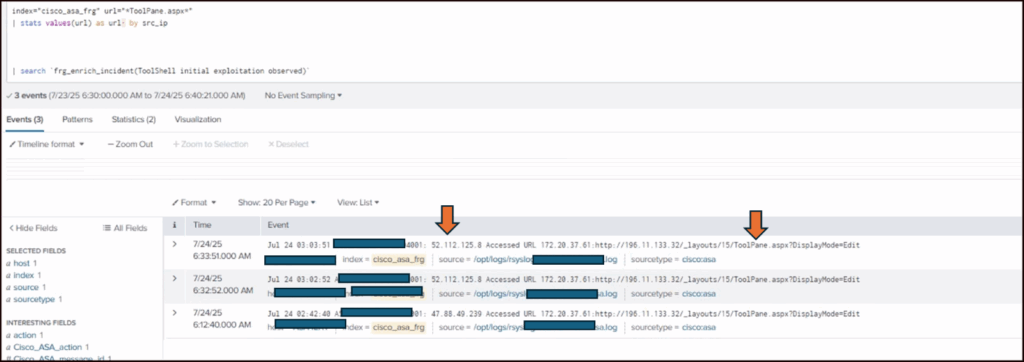
Figure 3: Second attack against a financial firm
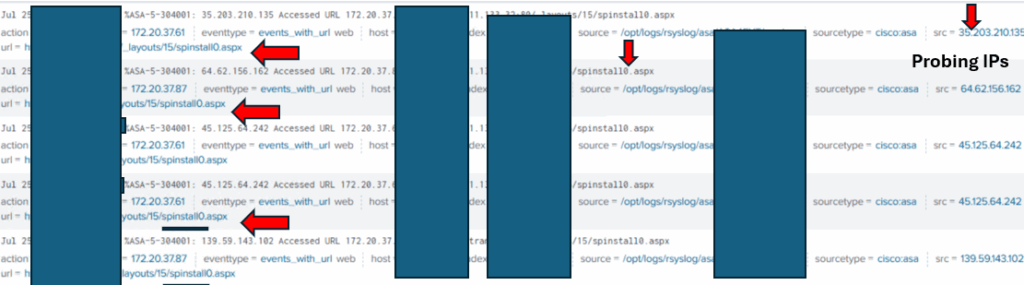
Figure 4: Third attack against a financial institute, observed on July 25, 2025
Threat Hunting Queries
Defender KQL: Detect Encoded PowerShell from IIS

Defender KQL: Detect ASPX Webshell Execution

Defender KQL: Base64-Decoded PowerShell from SharePoint (IIS)

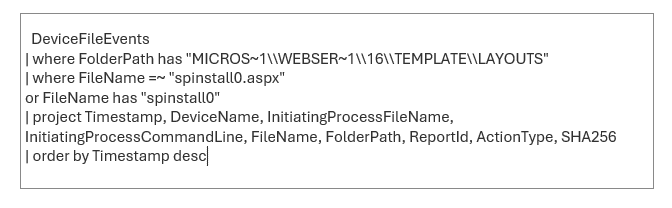
Query Based on Webshell Filename
Recommendations & Hardening
CISA recommends the following actions to reduce the risks associated with the RCE compromise:
- Configure Antimalware Scan Interface (AMSI) in SharePoint and deploy Microsoft Defender AV on all SharePoint servers.
- If AMSI cannot be enabled, disconnect affected products from service that are public-facing on the internet until official mitigations are available. Once mitigations are provided, apply them according to CISA and vendor instructions.
- Follow the applicable BOD 22-01 guidance for cloud services or discontinue use of the product if mitigations are not available.
- For information on detection, prevention, and advanced threat hunting measures, see Microsoft’s Customer Guidance for SharePoint Vulnerability and advisory for CVE-2025-49706.
CISA encourages organizations to review all articles and security updates published by Microsoft on July 8, 2025, relevant to the SharePoint platform deployed in their environment. - Monitor for: POSTs to /_layouts/15/ToolPane.aspx?DisplayMode=Edit
- Conduct scanning for IPs (particularly between July 18-19, 2025):
- 107.191.58[.]76
- 104.238.159[.]149
- 96.9.125[.]147
- Update intrusion prevention system and web application firewall rules to block exploit patterns and anomalous behavior.
For more information, see CISA’s Guidance on SIEM and SOAR Implementation. - Implement comprehensive logging to identify exploitation activity.
For more information, see CISA’s Best Practices for Event Logging and Threat Detection. - Audit and minimize layout and admin privileges.
- Rotate SharePoint Server ASP.NET machine keys:
After applying the latest security updates above or enabling AMSI, it is critical that customers rotate SharePoint server ASP.NET machine keys and restart Internet Information Services (IIS) on all SharePoint servers.- Manually via PowerShell: To update the machine keys using PowerShell, use: the Set-SPMachineKey cmdlet.
- Manually via Central Admin: Trigger the Machine Key Rotation timer job by performing the following steps:
- Navigate to the Central Administration site.
- Go to Monitoring -> Review job definition.
- Search for Machine Key Rotation Job and select Run Now.
- After the rotation has completed, restart IIS on all SharePoint servers using iisreset.exe.
- NOTE: If you cannot enable AMSI, you will need to rotate your keys after you install the new security update.
Indicator of Compromise
Malicious IPs (Some cab be possible probing IPs):
- 151.242.63.238
- 172.174.82.132
- 157.119.40.17
- 157.119.40.21
- 157.119.40.39
- 157.119.40.23
- 157.119.40.30
- 157.119.40.27
- 157.119.40.19
- 139.59.136.184
- 157.119.40.28
- 45.135.232.205
- 157.119.40.16
- 157.119.40.18
- 172.174.82.132
- 157.119.40.21
- 157.119.40.23
- 157.119.40.39
- 157.119.40.30
- 157.119.40.18
- 157.119.40.27
- 157.119.40.16
- 157.119.40.17
- 157.119.40.28
- 139.59.143.102
- 157.245.204.205
- 206.189.19.19
- 35.203.210.135
- 45.125.64.242
- 64.62.156.162
- 65.49.1.172
- 47.88.49.239
- 52.112.125.8
- 178.62.19.162
- 178.62.22.251
- 178.62.94.45
- 209.38.25.188
- 209.38.30.33
- 209.38.89.80
- 46.101.76.8
- 64.227.46.153
- 68.183.32.194
- 68.183.43.128
- 134.199.145.128
- 134.199.146.47
- 134.199.148.6
- 134.199.151.169
- 134.199.160.228
- 134.199.167.247
- 134.199.171.55
- 134.199.172.205
- 138.197.137.124
- 138.197.173.50
- 138.68.140.245
- 139.59.162.129
- 139.59.174.68
- 142.93.34.22
- 142.93.41.111
- 143.110.168.198
- 143.110.223.168
- 146.190.253.92
- 146.190.255.140
- 147.182.145.28
- 159.203.14.38
- 159.65.25.70
- 159.65.30.237
- 159.65.82.37
- 161.35.162.232
- 165.22.116.82
- 165.22.236.127
- 165.227.33.111
- 167.99.182.131
- 170.64.145.178
- 170.64.146.19
- 170.64.146.203
- 170.64.152.118
- 170.64.159.178
- 170.64.197.57
- 170.64.209.86
- 170.64.217.216
- 170.64.234.75
- 178.128.173.36
- 178.62.118.168
- 85.254.181.230
- 93.113.125.239
- 104.238.159.149
- 104.28.195.186
- 104.28.195.187
- 107.191.58.76
- 130.195.209.198
- 134.209.252.63
- 139.59.145.68
- 154.201.95.141
- 154.210.100.19
- 156.238.224.177
- 167.253.155.55
- 196.10.113.13
- 212.7.209.245
- 45.77.155.170
- 96.9.125.147
- 104.28.236.175
- 45.121.147.174
- 192.42.116.219
- 64.226.79.90
- 186.189.103.192
- 143.110.148.163
- 165.22.74.207
- 192.241.251.196
- 40.160.13.162
- 146.70.165.94
- 45.141.56.114
- 52.111.236.22
- 96.9.125.147
- 45.191.66.77
- 34.121.207.116
- 162.159.36.2
- 199.232.210.172
- 199.232.214.172
- 20.59.87.226
Malicious SHA256 Hashes:
- 92bb4ddb98eeaf11fc15bb32e71d0a63256a0ed826a03ba293ce3a8bf057a514
- 8d3d3f3a17d233bc8562765e61f7314ca7a08130ac0fb153ffd091612920b0f2
- 30955794792a7ce045660bb1e1917eef36f1d5865891b8110bf982382b305b27
- 27c45b8ed7b8a7e5fff473b50c24028bd028a9fe8e25e5cea2bf5e676e531014
- 10e01ce96889c7b4366cfa1e7d99759e4e2b6e5dfe378087d9e836b7278abfb6
- 4a02a72aedc3356d8cb38f01f0e0b9f26ddc5ccb7c0f04a561337cf24aa84030
- b39c14becb62aeb55df7fd55c814afbb0d659687d947d917512fe67973100b70
- fa3a74a6c015c801f5341c02be2cbdfb301c6ed60633d49fc0bc723617741af7
References
– https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-49704
– https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-49706
– https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53770
– https://msrc.microsoft.com/update-guide/vulnerability/CVE-2025-53771
– https://nvd.nist.gov/vuln/detail/CVE-2025-49704
– https://nvd.nist.gov/vuln/detail/CVE-2025-49706
– https://nvd.nist.gov/vuln/detail/CVE-2025-53770
– https://nvd.nist.gov/vuln/detail/CVE-2025-53771










