I recently had the opportunity to join a panel of top-tier cybersecurity experts to unpack the findings of the SANS 2025 Cyber Threat Intelligence (CTI) Survey. Navigating Uncertainty in Today’s Threat Landscape. Diving into the annual SANS CTI survey is always a moment I look forward to, a pulse check on the state of our field, how we’re evolving, and the common hurdles we all face. As information sharing is such a crucial element of CTI, I’ve pulled together some of the most compelling highlights.
CTI: From Niche to Necessity
One of the clearest signals from this year’s survey was that CTI has firmly moved out of its niche and into the mainstream. 93% of organizations now have some form of in-house CTI capability, and over half (52%) have a dedicated CTI team. This is a jump from 42% in 2018. The hybrid approach is also common, with roughly 60% of organizations combining internal expertise with external providers to bridge intelligence gaps.
When it comes to team size, most CTI teams remain relatively small: 62% reported having up to four full-time employees focused on CTI tasks.
Maturing CTI Processes
We dug into how organizations approach the three core pillars of CTI work, developing and tracking intelligence requirements, maintaining a collection plan to collect the data to generate intelligence, and threat modeling — how to address those threats. What we found was that requirements are the most clearly defined and well-documented processes across organizations.
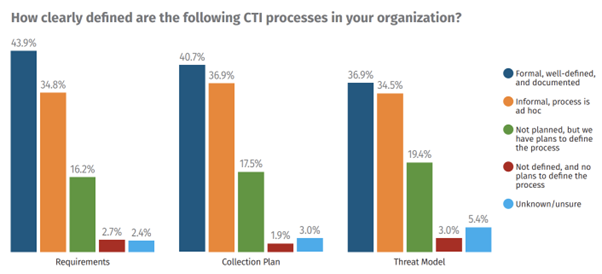
The survey also found that CTI programs are managing to remain agile and adaptive in their approaches, with 70% of respondents reporting a change to their processes in response to global events, from pandemics and digital threats to geopolitical upheaval. Through qualitative responses, we can see a heavy emphasis on certain changes, including:
- Moving from reactive to proactive: Such as adding threat hunting instead of just relying on incident response.
- Leaning on external data sources: 90% are using external data feeds such as media reports and public CTI feeds compared with just security analytics and SIEM.
- Reducing silos: Ensuring analysts can get value out of the rich data that’s inside an organization and can use this data to improve security posture.
MITRE ATT&CK: The CTI Framework of Choice
The MITRE ATT&CK framework continues to be the go-to standard for CTI teams. Threat hunting is the top use case for this framework with 84% of respondents leveraging it to proactively identify threats based on TTPs, but MITRE is also heavily used for detection (76%), threat actor profiling (65%), and incident response (60%). It’s become what SANS analysts dubbed the ‘lingua franca’ for CTI, giving security professionals across organizations a common language to describe and understand threats.
For organizations still early in their MITRE adoption, this presents a major opportunity. Integrating ATT&CK more deeply into workflows can improve everything from analyst communication to threat detection, making it one of the most impactful frameworks available to CTI teams today.
Communication and Reporting: CTI’s Front Line
Looking back at previous reports, this is the second year in a row that reporting has ranked as the top method for communicating threat intelligence. There has also been a huge increase in this approach over the past few years, from 62% in 2022 to 80% in 2025. Additionally, 72% of organizations now use threat intelligence platforms (TIPs) to feed insights into detection and response efforts.
And deliverables from this increase in reporting are expanding, too. Nearly 70% of teams produce landscape reports that inform both operational and strategic audiences. These reports help shape investment decisions, identify emerging threats, and support executive-level conversations. Other common products include “be on the lookout” reports, post-incident summaries, and business-focused quarterly or annual reports.
From the Theory of AI to Seeing it Work in Action
Last year, we saw a large percentage of respondents say that they were planning to implement AI into their CTI processes — and believe it or not, this year, those respondents have followed through, with over one third of organizations actively implementing AI for CTI! However, AI is being adopted across the intelligence cycle in varied ways.
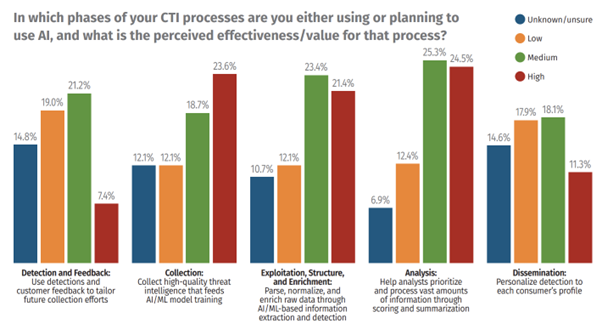
The highest value for AI in CTI is in collecting data, including getting teams’ hands-on high-quality threat intelligence, sifting through the increasing decibel level of noise, and understanding media reports better to eliminate duplicate information. The second highest value is seen in analysis — guiding analysts to prioritize and process data, doing some of that all-important initial triage and finding the right connections and patterns that can help drive analyst focus to the right areas.
Areas where AI was seen to have lower perceived value included detection and feedback, which makes sense, as it is not necessarily an area where AI can be easily plugged in and deliver immediate impact. Dissemination also ranked low, with only 11% of respondents seeing high value in AI for that area of the business. However, this could represent an untapped opportunity. Given the long list of reports enterprises are producing, the need to tailor and customize outputs for different audiences is significant, and this is exactly where AI could step in to add value.
The Impact of CTI on the Business
One of the questions we often ask ourselves is: How do we know CTI is working? Organizations want to show value and prove how CTI is benefiting an enterprises’ overall security posture. It’s difficult to prove but there are ways to do it! This year, 55% of respondents reported having some way to measure CTI effectiveness, up from 36% last year. That’s a step in the right direction, but with 32% still not measuring impact at all, there’s room for improvement.
Organizations generally use KPIs, benchmarking, or capability maturity models like the CTI-CMM to measure their CTI program. These help demonstrate CTI’s value to stakeholders and provide a roadmap for growth.
Top tip: Look for the appendix in the most recent version (1.2) of the CTI-CMM which includes CTI metrics and measurements and can be really useful for threat intelligence professionals.
Challenges and Opportunities for Cyber Threat Intelligence
What’s holding professionals back from going all-in on CTI? Funding remains the biggest roadblock, cited by 62% of respondents, a 10% increase on last year’s numbers. Management buy-in and lack of automation are also concerns to address, highlighted by 47% and 41% of enterprises respectively. Interestingly, a shortage of technical skills (34%) is more of an issue than a lack of analytical skills, which was only cited by 24% of respondents.
CTI teams should consider these challenges as opportunities for strategic investment.
Some of the biggest wins organizations are seeing include:
- Increased adoption of automation for time-consuming and repetitive tasks
- Tool integration that enables seamless data flow
- Stronger use of internal data, combined with rich external feeds
- Feedback-driven refinement of processes and tooling
What’s Next in the Industry?
The CTI industry is clearly maturing. We’re seeing regulatory pressure play a greater role, with more organizations expected to adopt formal CTI programs, perform threat landscape evaluations, and participate in information sharing. Even organizations that previously relied solely on external providers are now building internal capabilities to meet these regulatory demands.
But with growth comes complexity. CTI teams will need to stay flexible, adaptive, and strategic. That means investing in skills and tooling, partnering with the right vendors who can support you with fast adaptation to technology changes, team changes and landscape changes, and always remaining open to course correction as new challenges arise. Here are some recommended next steps:
- Read the complete SANS 2025 Cyber Threat Intelligence (CTI) Survey. Navigating Uncertainty in Today’s Threat Landscape.
- Get in touch to discuss implementing a more robust CTI program in your organization.
Ultimately, CTI is about creating value through insight, turning information into understanding, and understanding into action. As our threat landscape continues to evolve, so too must our ability to anticipate, respond, and communicate.






