Introduction
Ransomware in 2025 remains one of the most financially and operationally devastating threats facing organizations across sectors. What began as a disruptive cybercrime model over a decade ago has now evolved into a global criminal ecosystem powered by professional Ransomware-as-a-Service (RaaS) operations, cross-group collaboration, and fast-paced TTP innovation.
CyberProof today, releases its 2025 Mid-Year Cyber Threat Landscape Report, that highlights the cyber threat landscape for the first half of 2025. Key findings from H1 2025 show a landscape characterized by the emergence of sophisticated AI-powered ransomware groups, intensified targeting of critical infrastructure, and the continued blurring of lines between nation-state actors, cybercriminals, and hacktivists.
Top Ransomware Trends
Recent reporting shows a 38% year over year increase in enterprise ransomware incidents, with a significant portion involving multi-layer extortion, cloud infrastructure compromise, and critical service disruption across finance, IT, healthcare, manufacturing, and government entities.
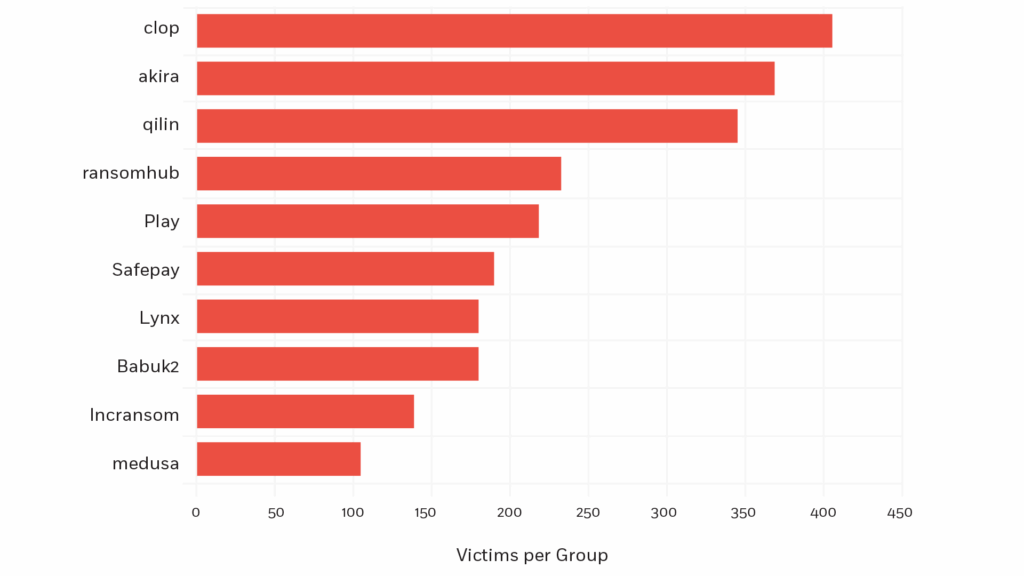
Fig.1: Top 10 Ransomware of 2025 (source: https://www.ransomware.live/)
Among the dozens of active ransomware variants, four groups—Akira, RansomHub, Qilin, and Cl0p—have emerged as particularly aggressive and technically sophisticated. Each represents a different philosophy and operational pattern, yet collectively, they reflect broader trends in 2025’s ransomware scene. This blog provides a technical comparison of their Tactics, Techniques, and Procedures (TTPs), highlights key emerging trends, and offers defense recommendations.
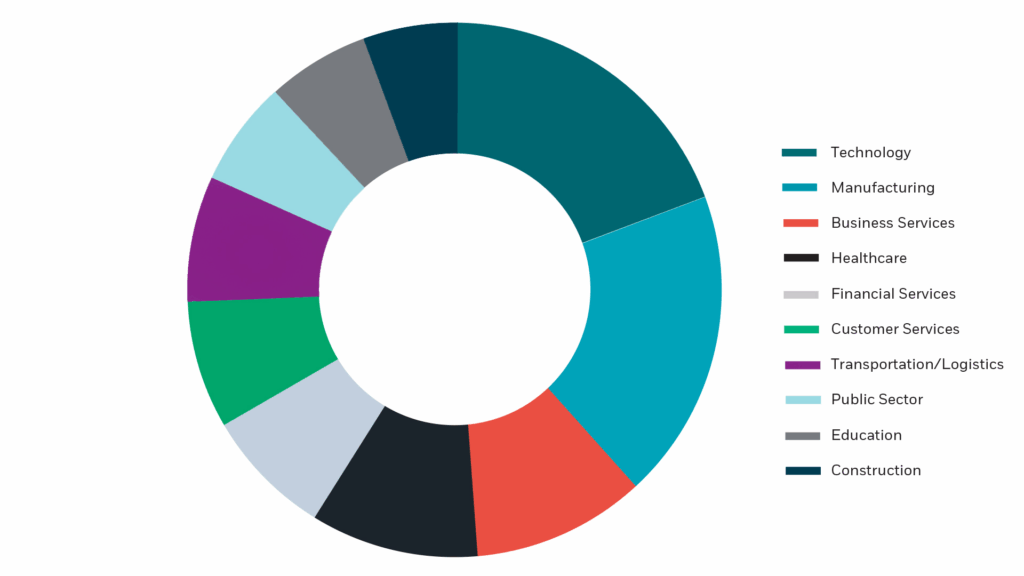
Fig. 2: Top 10 Targeting Sectors in 2025 (source: https://www.ransomware.live/)
TTPs Comparisons: Akira, RansomHub, Qilin, and Cl0p
Despite their differences, these ransomware groups exhibit a high degree of tactical overlap, reflecting both the commoditization of ransomware tooling and the exchange of operational playbooks on dark web forums.
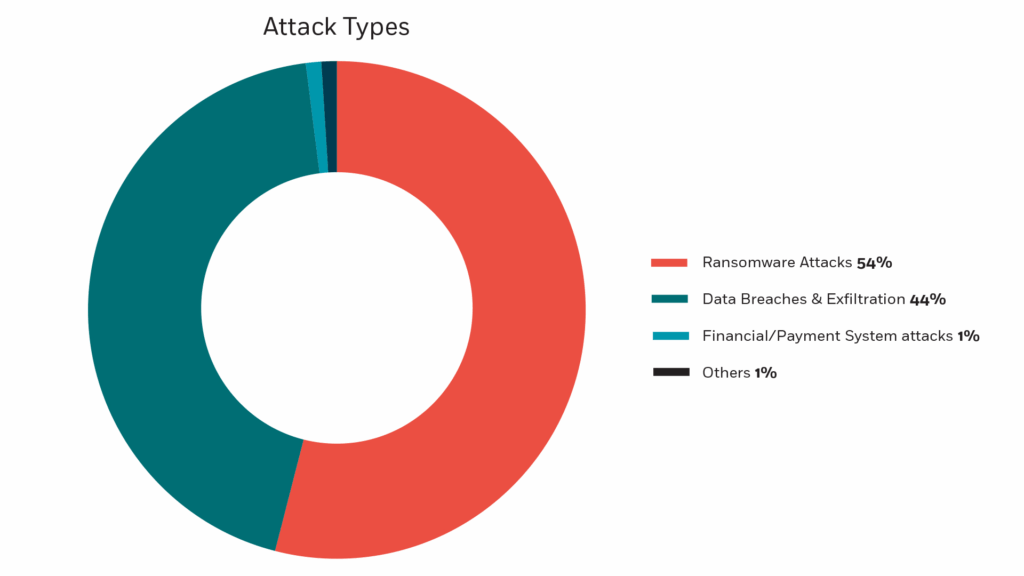
Fig. 3: Top 10 Attack types in 2025
Initial Access
Threat groups such as Cl0p and RansomHub gain initial access by exploiting vulnerabilities in public-facing applications and remote access services. They often rely on phishing campaigns, malicious attachments, and credential abuse to infiltrate environments. Akira, on the other hand, focuses heavily on exploiting single-factor VPNs and external remote services by using stolen or purchased credentials. Qilin is known for targeting vulnerabilities in backup and virtualization platforms—such as Veeam—and abuses compromised VPNs for access.
Execution
All four groups—Cl0p, Akira, Qilin, and RansomHub—employ command and scripting interpreters like PowerShell and Bash to execute payloads, automate lateral movement, and disable security mechanisms. Cl0p and Akira frequently deploy custom executables that masquerade as legitimate processes to evade detection. Qilin stands out by using advanced loaders such as NETXLOADER and SmokeLoader, which facilitate in-memory execution to bypass security controls.
Persistence
To maintain access, Akira and Qilin install or modify system services, configure scheduled tasks, and deploy legitimate remote access tools like AnyDesk and Radmin. RansomHub achieves persistence by creating or reactivating user accounts and manipulating registry keys, in addition to scheduling malicious tasks.
Privilege Escalation and Credential Access
All groups rely on credential dumping techniques, including LSASS memory scraping and tools like Mimikatz, to escalate privileges and enable lateral movement. Valid accounts are also abused extensively. Cl0p and RansomHub are particularly skilled in Kerberos ticket theft and account manipulation. Qilin and Akira leverage deeper Active Directory manipulation and Kerberos ticket abuse to expand their foothold within networks.
Discovery and Lateral Movement
Reconnaissance is conducted using tools like AdFind, MASSCAN, and SharpHound to enumerate Active Directory objects and map the network. Lateral movement techniques include the use of RDP, SMB, VPNs, and remote monitoring and management tools such as PsExec and AnyDesk. Cl0p and RansomHub favour stealthier, legitimate channels for movement across systems.
Defense Evasion
Each group demonstrates strong capabilities in evading detection. They routinely disable or tamper with endpoint security tools, clear logs, and use obfuscation and masquerading techniques to blend into normal operations. Cl0p and Qilin have increasingly adopted Bring Your Own Vulnerable Driver (BYOVD) techniques to bypass endpoint detection and antivirus solutions. Meanwhile, Akira and RansomHub have shown advanced capabilities in log clearing and service impersonation.
Exfiltration and Impact
Double extortion is a common tactic among these groups. They archive sensitive data using tools like WinRAR and Rclone, exfiltrate it via cloud services or SFTP, and subsequently encrypt victim files. Backups, such as volume shadow copies, are deleted to hinder recovery. The threat of public data leaks is leveraged through dedicated leak sites to maximize pressure on victims. Qilin also takes the additional step of overwriting free disk space after encryption, making data recovery virtually impossible.
MITRE ATT&CK Mapping Table
| Tactic | Technique | ID | Groups Involved |
| Initial Access | Exploit Public-Facing Applications | T1190 | Cl0p, RansomHub, Qilin |
| External Remote Services | T1133 | Cl0p, Akira, Qilin | |
| Phishing | T1566 | Cl0p, RansomHub | |
| Valid Accounts | T1078 | Cl0p, Akira, RansomHub | |
| Valid Accounts: VPN Credential Abuse | T1078.001 | Akira | |
| Execution | Command and Scripting Interpreter | T1059 | All |
| PowerShell | T1059.001 | All | |
| Bash | T1059.004 | All | |
| User Execution: Malicious File | T1204 | Cl0p, Akira | |
| In-Memory Execution: Reflective DLL Injection | T1055.002 | Qilin | |
| In-Memory Execution: Indicator Removal from Tools | T1620 | Qilin | |
| Persistence | Create or Modify System Process: Windows Service | T1543 | Akira, Qilin |
| Scheduled Task/Job | T1053 | Akira, Qilin, RansomHub | |
| Remote Access Software | T1219 | Akira, Qilin | |
| Create Account | T1136 | RansomHub | |
| Modify Registry | T1112 | RansomHub | |
| Privilege Escalation | Credential Dumping | T1003 | All |
| LSASS Memory | T1003.001 | All | |
| Valid Accounts | T1078 | All | |
| Kerberos Ticket Theft | T1558 | Cl0p, RansomHub | |
| Account Manipulation | T1098 | Cl0p, RansomHub | |
| Kerberos Golden Ticket | T1558.003 | Qilin, Akira | |
| Discovery | Remote System Discovery | T1018 | All |
| Network Service Scanning | T1046 | All | |
| Account Discovery: Domain Account | T1087.002 | All | |
| Lateral Movement | Remote Desktop Protocol | T1021.001 | All |
| SMB/Windows Admin Shares | T1021.002 | All | |
| Remote Services: PsExec | T1563.002 | All | |
| Defense Evasion | Impair Defenses | T1562 | All |
| Clear Windows Event Logs | T1070 | All | |
| Obfuscated Files or Information | T1027 | All | |
| Masquerading | T1036 | All | |
| BYOVD | T1216 | Cl0p, Qilin | |
| Log Clearing | T1070.004 | Akira, RansomHub | |
| Masquerading: Service Impersonation | T1036.004 | Akira, RansomHub | |
| Exfiltration | Archive Collected Data | T1560 | All |
| Exfiltration Over Alternative Protocol: SFTP | T1048.002 | All | |
| Impact | Data Encrypted for Impact | T1486 | All |
| Data Destruction: Disk Content Wipe | T1485 | Qilin | |
| Inhibit System Recovery | T1490 | All | |
| Data Leak Sites | T1537 | All |
Emerging Trends to Watch
- Modular Payloads & Automation: Ransomware is becoming plug and play. Affiliates can customize TTPs with automation tools reducing dwell time and increasing speed of impact.
- Stealth Through LOLBins and Signed Binaries: Increased usage of Windows native tools and signed binaries is allowing ransomware actors to evade behavioural detection and reduce forensic artifacts.
- Narrative-Driven Extortion: Groups now write their own blogs, issue “press releases,” and even publish breach analysis to drive victim compliance and public outrage.
- Cloud & SaaS Attacks: There’s growing interest in targeting Microsoft 365, Google Workspace, and Slack via token theft, MFA fatigue, and OAuth app abuse.
- AI-Enhanced Development: Groups like FunkSec are leveraging AI tools for malware development, using large language models to generate code with perfect language comments, enabling rapid development and evasion techniques.
- BYOVD (Bring Your Own Vulnerable Driver) Attacks: Ransomware groups continue using legitimate but vulnerable signed drivers to gain kernel level access and disable security tools, with tools like EDRS and blast and backstab lowering technical barriers
- Cross-Group TTP Borrowing: There’s increased reuse of techniques, codebases, and infrastructure between unrelated groups, indicating shared playbooks or common training grounds for affiliates.
Recommendations
- Invest in EDR/XDR solutions with behavioral analytics tuned to detect LOLBin abuse and script-based lateral movement.
- Harden VPNs and external facing infrastructure – patch aggressively, monitor logs for unusual access patterns, and implement geo-blocking where possible.
- Segment networks and implement MFA – particularly on critical infrastructure and administrative consoles.
- Implement Zero Trust principles – across identity, devices, and network segmentation.
- Monitor for data leaks – Leverage dark web monitoring tools to detect if your data appears in extortion portals or forums.
Conclusion
The ransomware landscape in 2025 is more fractured, decentralized, and unpredictable than ever before. Groups like Akira, RansomHub, Qilin, and Cl0p are refining their playbooks, aligning with either profit driven or ideological goals, and innovating faster than most enterprises can react. By understanding their shared and unique TTPs, defenders can better prepare for the evolving threat landscape. The days of ransomware being “just about encryption” are over—2025 marks the era of full spectrum digital coercion.
Learn more about major threat trends, cyber and geopolitical events, as well as top attack indicators for the 1H 2025 in the CyberProof 2025 Mid-Year Cyber Threat Landscape Report.
References
- https://www.cysecurity.news/2025/07/ransomware-attacks-surge-in-2025-with.html
- https://unit42.paloaltonetworks.com/2025-ransomware-extortion-trends/
- https://ciso.economictimes.indiatimes.com/news/cybercrime-fraud/cyble-report-highlights-new-ransomware-groups-and-spike-in-supply-chain-attacks/121974930
- https://reliaquest.com/blog/ransomware-cyber-extortion-threat-intel-q2-2025/
- https://www.checkpoint.com/cyber-hub/threat-prevention/ransomware/funksec-ransomware-ai-powered-group/
- https://www.picussecurity.com/resource/blog/ransomhub








