In recent months, threat actors have broken into previously uncharted territory by accessing and abusing the Unified Extensible Firmware Interface (UEFI), which defines how firmware interfaces connect with computer operating systems.
Researchers in the ESET security community recently observed the first ever in-the-wild UEFI bootkit that is capable of bypassing UEFI Secure Boot - named BlackLotus. The bootkit is readily available for sale on black market forums and can run on even fully-up-to-date Windows 11 systems with UEFI Secure Boot enabled.
Researchers recently observed the first ever in-the-wild UEFI bootkit that is capable of bypassing UEFI Secure Boot - named BlackLotus.
How BlackLotus affects Microsoft systems
The bootkit exploits a relatively older vulnerability CVE-2022-21894 to bypass UEFI Secure Boot and set up persistence for the bootkit. This is the first publicly known, in-the-wild abuse of this vulnerability. Although the vulnerability CVE-2022-21894 was fixed in Microsoft’s January 2022 update, its exploitation is still possible as the affected, validly signed binaries have still not been added to the UEFI revocation list. This is leveraged by attackers who bring their own legitimate - but vulnerable - binaries to the system to go ahead with the exploitation.
The bootkit boasts some effective mechanisms for disabling OS security features, such as MS Defender and BitLocker.
Once installed, the bootkit’s main goal is to deploy a kernel driver and an HTTP downloader responsible for communication with the C2 infrastructure. It can load additional user-mode or kernel-mode payloads.
What a BlackLotus kill chain looks like
Although we believe that the bootkit is not currently leveraged by many attackers, the kill chain is described as follows:
-
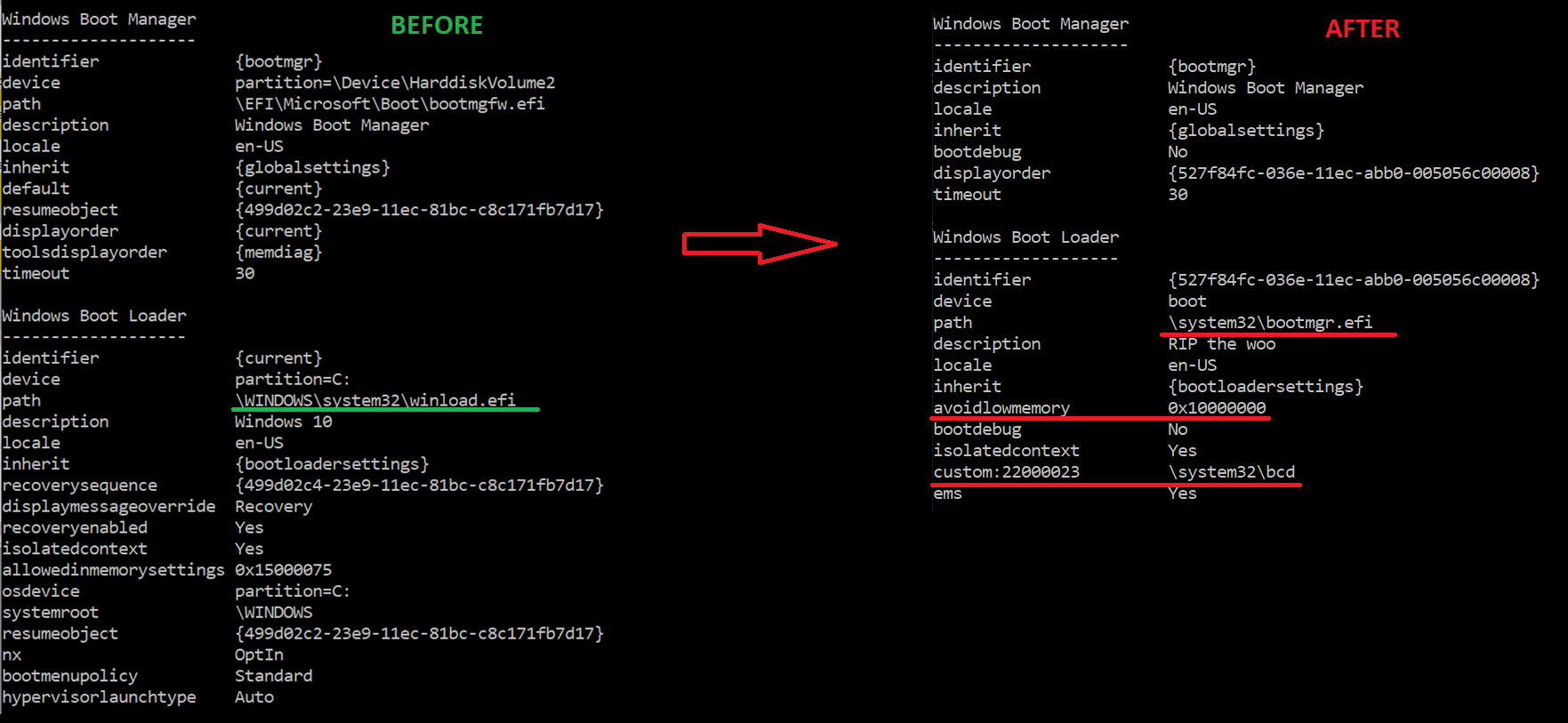
Execution of an installer responsible for deploying the bootkit’s files to the EFI System partition, disabling HVCI and BitLocker, and then rebooting the machine.
-
After the first reboot, exploitation of CVE-2022-21894 and subsequent enrollment of the attackers’ Machine Owner Key occurs, to achieve persistence even on systems with UEFI Secure Boot enabled. The machine is then rebooted again.
-
In all subsequent boots, the self-signed UEFI bootkit is executed and deploys both its kernel driver and user-mode payload, the HTTP downloader. Together, these components download and execute additional user-mode and driver components from the C2 server and protect the bootkit against removal.
CyberProof recommendations for protecting against BlackLotus
To mitigate the risk of a BlackLotus attack, monitor for the following legitimate Windows binaries that are regularly abused by BlackLotus:
-
https://msdl.microsoft.com/download/symbols/bootmgfw.efi/7144BCD31C0000/bootmgfw.efi
-
https://msdl.microsoft.com/download/symbols/bootmgr.efi/98B063A61BC000/bootmgr.efi
-
https://msdl.microsoft.com/download/symbols/hvloader.efi/559F396411D000/hvloader.efi
In addition, monitor for access to the KUSER_SHARED_DATA structure fields NtMajorVersion and NtMinorVersion in memory.
-
Monitor if the legitimate Windows Boot Manager (bootmgfw.efi) binary located in the ESP:EFIMicrosoftBoot directory is renamed to winload.efi. • Monitor for the creation of the custom directory ESP:/system32/.
-
Monitor if the enabled registry value under the HypervisorEnforcedCodeIntegrity registry key is set to zero.
-
Monitor for instances that could cause the BitLocker Drive Decryption to become disabled.
-
Monitor for attempts to establish persistence via the malware writing its own MOK to MOKLIST.
Want to ensure that your organization’s assets are monitored on a regular basis and protected against potentially undetectable threats? Reach out here to speak to an expert.