Executive Summary
In 2025, East Asia continues to be one of the most targeted and volatile cyber regions in the world. Nations like Japan, South Korea, and Taiwan, known for their innovation, digital dependency, and geopolitical relevance, face an increasingly hostile environment driven by sophisticated, persistent cyber campaigns. State-backed threat actors from China and North Korea continue to dominate the region’s threat profile, using cyber operations as a key instrument of geopolitical leverage, financial gain, and information warfare.
With critical sectors under attack from semiconductors and public infrastructure to defence and finance the cybersecurity challenges facing East Asia are deep-rooted and increasingly multi-dimensional.
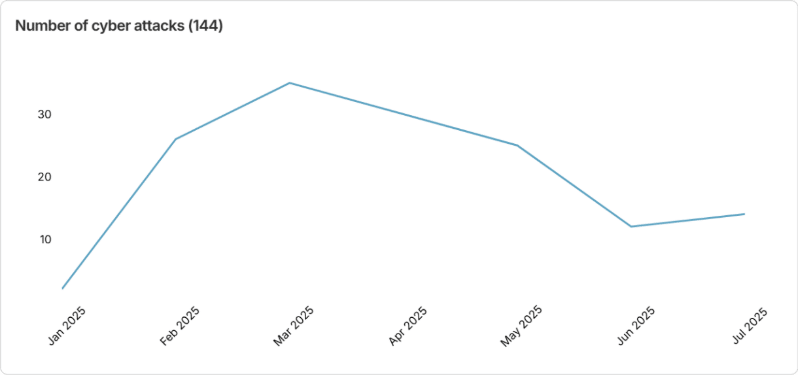
Fig. 1: Cyber Attack Trends
Sector-Specific Targeting: From Critical Infrastructure to Intellectual Property
The cyberattacks plaguing East Asia in 2025 are highly targeted, with adversaries focusing their efforts on strategic sectors vital to national resilience and global competitiveness.
Government and military institutions continue to face high volumes of intrusion attempts aimed at intelligence theft and operational disruption. Technology and manufacturing sectors, especially those tied to aerospace and semiconductors, are prime targets for espionage-driven campaigns. Financial services, including banks and cryptocurrency exchanges, remain under constant assault from financially motivated actors. Healthcare and academic sectors, once considered secondary targets, are now routinely attacked due to the value of personal data and research assets.
China and North Korea: Operational Objectives and Tactical Playbooks
Two primary state-aligned cyber actors dominate activity across East Asia—China and North Korea each employing distinct tradecraft, infrastructure, and motivations.
Chinese threat groups are driven by long-term strategic gains. Their operations are typically geared toward economic espionage, critical infrastructure mapping, and influence campaigns. Groups like MirrorFace and Salt Typhoon are known for multi-vector attacks against telecom, academic, and manufacturing sectors, often mimicking state behaviour patterns like pausing activity during national holidays and aligning with business hours in Beijing.
North Korean groups, particularly Lazarus Group, continue to specialize in high-return cybercrime. Their attacks frequently target cryptocurrency platforms, while also engaging in espionage and data theft. Phishing remains a primary delivery method, often disguised through fake job recruitment messages on platforms like LinkedIn.
Japan: Multi-Vector Espionage and Infrastructure Attacks Intensify
Japan faced a surge in sophisticated cyberattacks throughout 2025, driven by a mix of Chinese espionage and regional disruption campaigns.
In January, the MirrorFace group launched a multi-sector campaign targeting Japan’s semiconductor, telecom, aerospace, and academic organizations. The attackers exfiltrated sensitive intellectual property, revealing a strategic focus on industries critical to Japan’s economic edge.
Parallel to these espionage efforts, Japan was hit by an expansive wave of DDoS attacks, affecting at least 46 high-profile entities, including Mizuho Bank, NTT Docomo, Japan Airlines, and multiple government agencies. The infrastructure used for these attacks suggested a high degree of coordination, leveraging malware reuse to disable online services and overwhelm systems.
Other incidents included a ransomware attack on the DIC Utsunomiya Central Clinic, unauthorized access at Hamamatsu’s Regional Innovation Promotion Organization, and a data breach from the Hands Club App. These attacks exposed vulnerabilities in Japan’s healthcare systems and municipal IT networks, prompting urgent reviews of incident response capabilities. In response, Japan implemented the Active Cyber Defence Law in 2025, authorizing pre-emptive defence measures to disrupt imminent cyber threats before they materialize.
South Korea: AI-Driven Threats and the Lazarus Campaign
South Korea’s cybersecurity landscape in 2025 has been shaped by a surge in both nation-state campaigns and emerging AI-driven threats.
A significant event unfolded in June when the ticketing giant Yes24 suffered a ransomware attack that disrupted e-book services, community forums, and concert bookings. This led to multiple event cancellations including high-profile K-pop performances and sparked investigations into the platform’s data privacy practices.
Statistics released mid-year show 1,887 cyber breaches in South Korea during the first half of 2025 alone, reflecting a dramatic increase from previous years. Much of this spike is attributed to North Korean APTs, including the Lazarus Group, which remains active in phishing, ransomware deployment, and cryptocurrency theft.
Of particular concern is the growing use of artificial intelligence by threat actors to automate reconnaissance, evade detection, and improve malware payload delivery. South Korea’s Cyber Operations Command has initiated the deployment of AI-based defence platforms, though officials acknowledge that gaps in cyber infrastructure and workforce readiness still hinder full-scale mitigation.
Taiwan: Persistent Chinese Targeting and Geopolitical Spillover
Taiwan remains a frontline target in East Asia’s cyber conflict, with daily cyberattack attempts reaching into the millions a trend that began in 2024 and has continued aggressively into 2025.
The primary aggressor continues to be China, which is accused of launching sustained campaigns against Taiwanese government systems, telecom infrastructure, and private enterprises. Taiwanese officials report ongoing espionage activity and disruption attempts, including incidents involving infrastructure reconnaissance and data exfiltration.
In a geopolitical twist, China in May 2025 publicly accused Taiwan of cyberattacks against a domestic tech company. Taiwan denied the allegation, reaffirming that it is instead the victim of ongoing, state-aligned Chinese cyber aggression.
Intelligence experts warn that China’s digital incursions ranging from espionage to interference with undersea internet cables could represent early stages of kinetic escalation in the Taiwan Strait. In response, Taiwan has announced plans to launch a centralized Cybersecurity Coordination Center to improve incident detection, coordination, and attribution.
Strategic Threat Trends: AI Arms Race, Policy Shifts, and Persistent Ransomware
Several macro-level trends are defining East Asia’s threat environment:
- Ransomware remains the dominant threat vector across the region. In the first half of 2024 alone, the Asia-Pacific recorded over 57,000 ransomware attacks, and this aggressive pace has extended into 2025, disrupting healthcare, transportation, and government services.
- AI is changing the offensive landscape. Threat actors are using AI to create more sophisticated social engineering lures and malware variants, while defensive teams scramble to integrate AI into threat hunting, anomaly detection, and automated incident response.
- National cybersecurity policy is evolving. Japan’s Active Cyber Defense Law, South Korea’s military-grade AI countermeasures, and Taiwan’s investment in a national cybersecurity hub all signal that governments are moving from reactive defence to proactive cyber resilience.
Yet even with stronger policy frameworks, regional cooperation and cyber workforce development will remain critical if East Asia is to contain escalating threats in a fast-moving digital battleground.
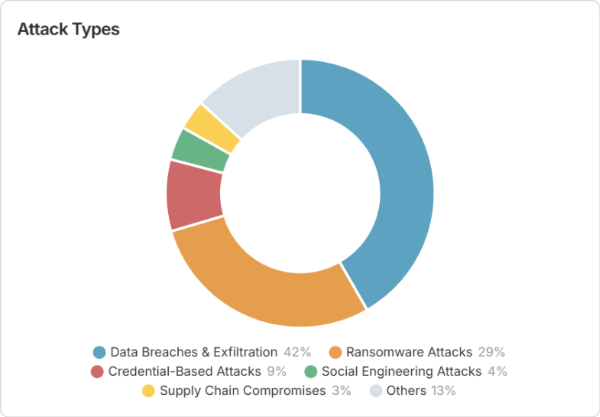
Fig. 2: Attack Type Distribution
Conclusion: Navigating the Digital Frontline
The cybersecurity terrain in East Asia has become increasingly complex, marked by hybrid threats that blend cybercrime with statecraft. As China and North Korea continue to exploit regional tensions through digital operations, nations like Japan, South Korea, and Taiwan find themselves defending against not just cyberattacks—but strategically calculated campaigns meant to weaken resilience and shift power balances. While legislative reforms and AI-driven defences represent progress, they are not silver bullets. Long-term cybersecurity in East Asia will depend on deep regional partnerships, cross-sector coordination, and a clear-eyed recognition that cyber defence is now a pillar of national strategy not just an IT concern.
Learn more about these and other global campaigns in the recently released, CyberProof 2025 Mid-Year Cyber Threat Landscape Report. The report provides insights into the most active ransomware groups, top threat trends, and an analysis of 2024 predictions versus 2025 realities.
References
- https://www.crnasia.com/news/2025/cybersecurity/asia-pacific-had-the-most-cyberattacks-in-2024
- https://www.cnas.org/press/press-release/new-cnas-report-calls-for-a-cyber-shield-to-meet-rising-threats-in-the-indo-pacific
- https://dxc.com/us/en/insights/growth-drivers/staying-ahead-of-cyber-threats-in-asia-pacific
- https://securitybrief.asia/story/cybersecurity-predictions-for-asia-pacific-in-2025