Contributors: Niranjan Jayanand, Madhuri Syamakala, Venkatesh Bolla
Executive Summary
- On 01 April, researchers reported RansomHub infrastructure going offline and signs of affiliates possibly joining another Qilin RaaS. This is not new in the ransomware world, where we have seen affiliates getting hired across groups, encryptors’ code getting reused, and rebranding of ransomwares.
- RansomHub remained as one of the top active Human Operated ransomware groups in last 12 months reported to have targeted over 600+ organizations. The group is known to target Windows, Linux, ESXi and FreeBSD platforms and capable of encrypting files in local and remote file systems via SMB and SFTP.
- RansomHub is known to also infect users through SocGholish infection, a well-known JavaScript based malicious loader atleast since 2020. CyberProof customers are well protected against SocGholish campaigns.
- RansomHub has caught the news in early 2024 when they reported to have acquired stolen data from a former ALPHV / BlackCat affiliate to target Change HealthCare that caused the firm to lose about $872 million to the incident. The group is believed to share code from BlackCat and Knight.
- DragonForce has recently begun promoting a new service where they allow cybercrime teams to white-label their services.
Technical Details
Global ransomware threats have not slowed down since the beginning of 2025. Below stats show the most active ransomware groups from a public research. Reports identity the threat actors classified as Scattered Spider have been known to act as affiliates for various ransomware operations, including RansomHub, Qilin, and now, DragonForce.
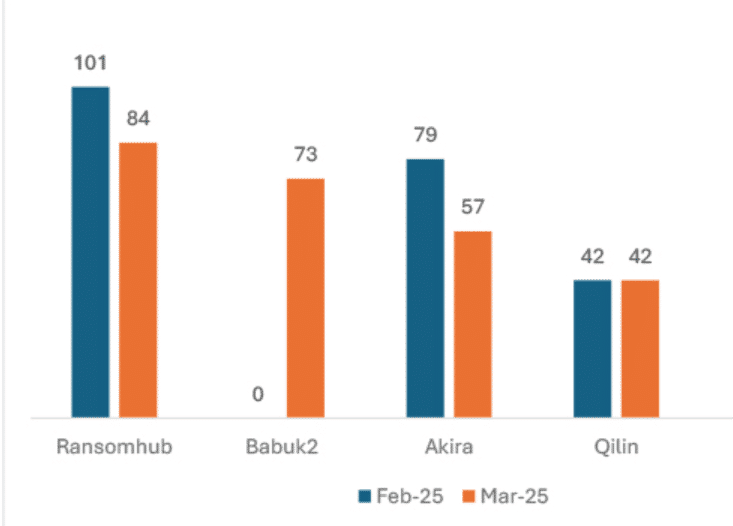
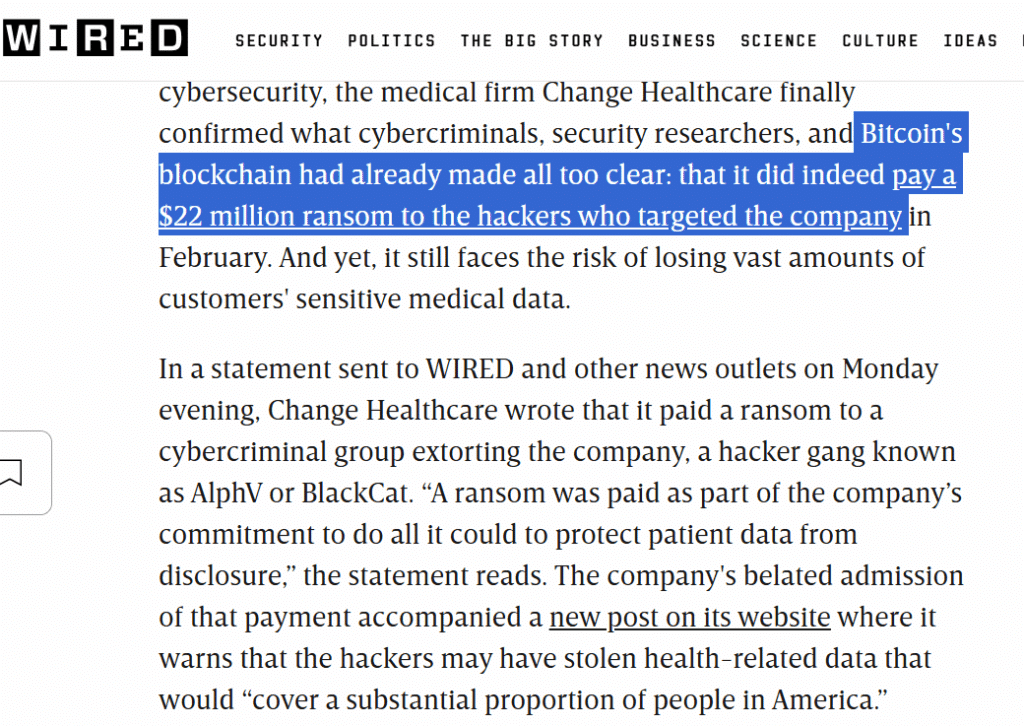
In 2024, RansomHub caught the world’s attention when Change HealthCare was targeted by them and ALPHV where the organization had to pay a ransom amount to whopping $22 million USD.
BlackCat operators pulled an exit scam, the disgruntled affiliate may have leaked the allegedly stolen data to sell it to other cybercriminals – possibly to RansomHub.
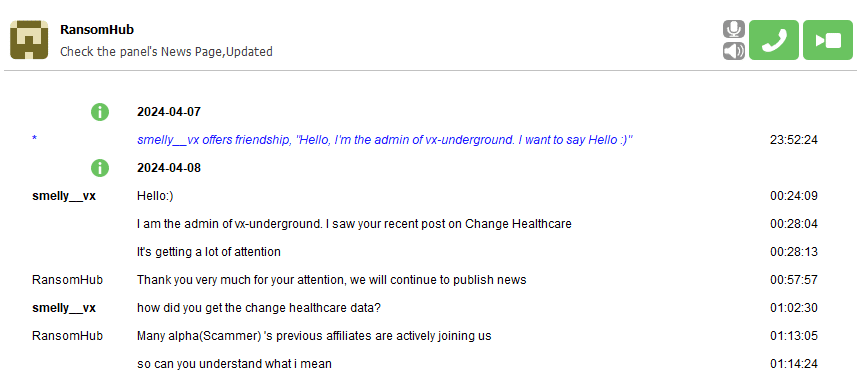
RansomHub later listed on its leak site, claiming to be in the possession of the 4TB of stolen.
RansomHub is known to target multiple critical sectors including manufacturing, healthcare, and financial services, with a particular focus on organizations in the United States and Europe. On 01 April 2025, DragonForce claim that some affiliates have already joined other groups signally a possible instability within the group (possibly through new hiring within Qilin that resulted in a surge in Qilin’s DLS announcing new victim names in recent weeks).

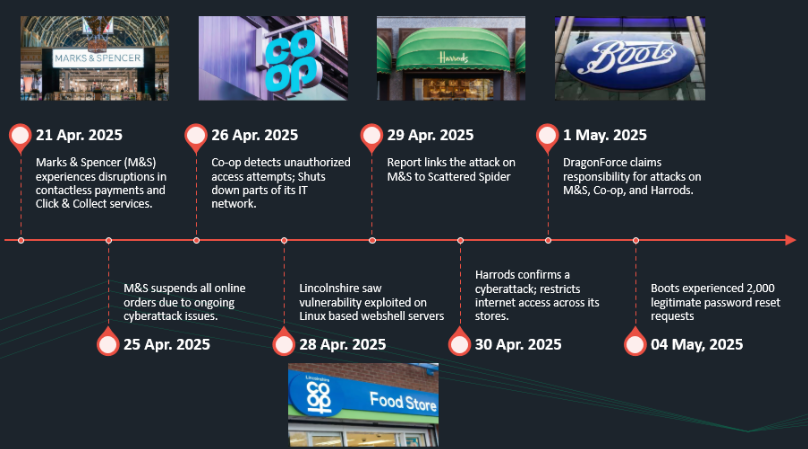
DragonForce’s most recent and high impactful attack was reported to hit Mark and Spencer that results in a lose more than 700 million pounds ($930m) in its market value. Mandiant and a public reporting has suggested that threat actors used tactics consistent with Scattered Spider to target a UK retail organization and deploy DragonForce ransomware. Subsequent reporting by BBC News indicates that actors associated with DragonForce claimed responsibility for attempted attacks at multiple UK retailers. Below is the timeline of the group’s coordinated attack against UK organizations.
Code Similarity Between RansomHub and Knight Ransomware
Below 2 images show some level of code sharing between these two ransomware stains. Samples considered for quick review are
- RansomHub – EEC3A55B1599EEE16A47954E1BB230EC99DB5F96
- Knight – 63C31BCDA20194821D142A0ED131EB32649AA32E
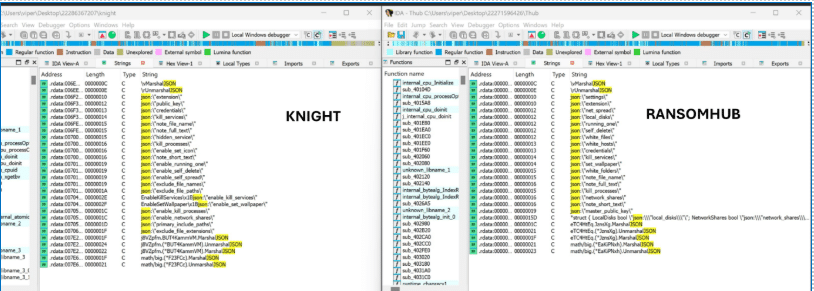
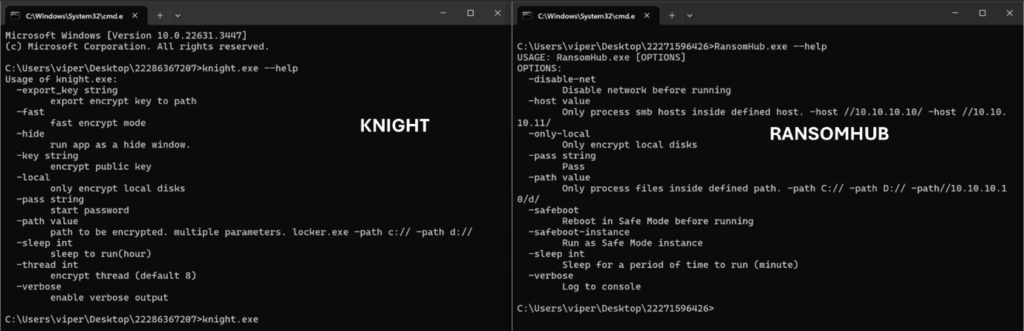
Both support similar arguments for execution as shown below:
Recorded Future has shared a visual representation on similarities seen between BlackCat/ALPHV, RansomHub, and Knight as shown below:
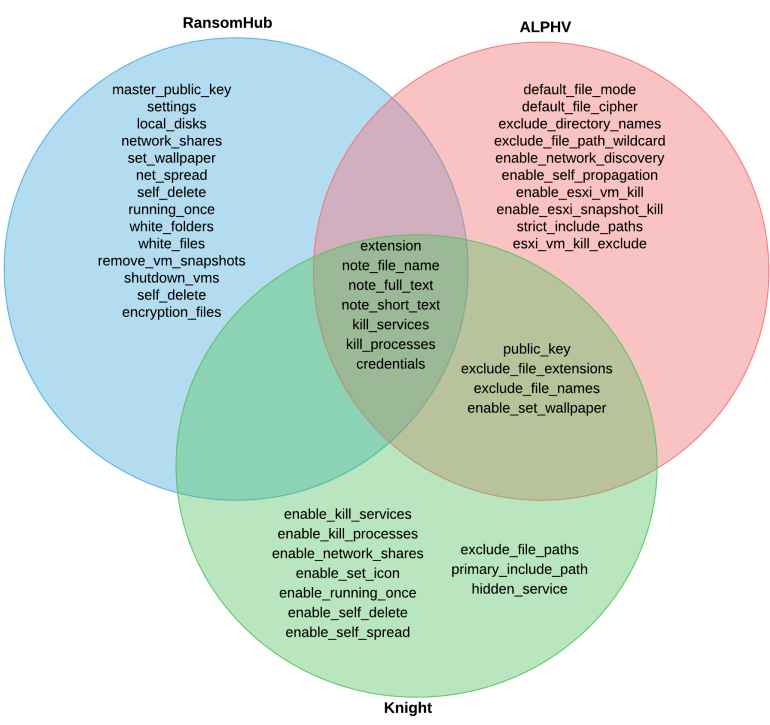
Source: Recorded Future
Malwares, Tools and Exploits Used
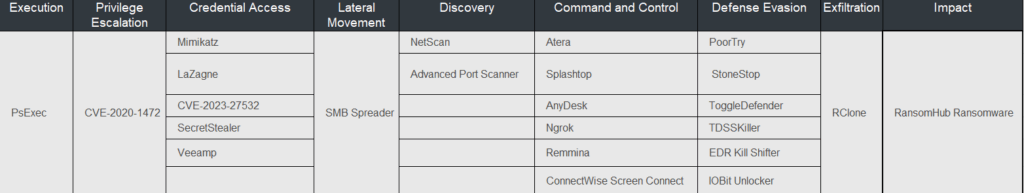
Source: TrendMicro
Conclusion
Ransomware groups becoming inactive and resurgence of groups under new branded logo is not new. We expect rise in activities tied to DragonForce operating as a Cartel in coming months. Our team of researchers will continue to review malicious files at code level and perform additional analysis to enrich our knowledge base on threat groups and TTPs to develop detection logics to stay ahead of targeted attacks by cyber criminals.
At CyberProof, our strong cross team collaboration between SOC, MEDR, UCM, Automation, Engineering and R&D has successfully mitigated multiple intrusions in first quarter of 2025. We will continue to focus on high impactful threat groups in coming months and shall report if we find any interesting stories. Please review MITRE attack navigator for RansomHub to learn more about the group’s TTPs.
Indictors of Compromise
- IOCs reference #1 – RansomHub: Attackers Leverage New Custom Backdoor | Symantec Enterprise Blogs
- IOCs reference #2 #StopRansomware: RansomHub Ransomware | CISA
Recommendation
- Ensure implementing Multi-Factor Authentication (MFA) for all accounts and applications (ie VPNs, etc)
- Regular audits of inventory and logs.
- Implement regularly scheduled backups and recovery processes.
- Review and ensure regular patch management.
- Leverage cyber threat intelligence to stay ahead of threat actors targeting your organizations directly or through indirect business partners (mergers and acquisitions).
- Ensure regular scans using updated EDR solutions.
- Limit exposure of services by disabling unused ports.
- Segment networks to restrict lateral movement from initial infected devices and other devices in the same organization.
How CyberProof Can Help
CyberProof Advanced Threat Hunters are skilled to hunt across different security platforms building new hypothetical queries to stay ahead of threat landscape. We learn through telemetry around the clock to identify how attackers modify their TTPs challenging our researchers. We heavily continue to focus on malicious loaders like SocGholish, IDAT loader (HijackLoader) and RATs etc to alert and block early stage attacks.










