Contributors: Karthik Joseph, Niranjan Jayanand
Executive Summary
CyberProof MDR analysts alerted Threat Hunters on an incident originating from an infected USB device that could lead to a backdoor infection and cyptomining through a multi-stage attack leveraging DLL search order hijacking and PowerShell to bypass security. Upon further investigation, we were able to confirm the malware involved, was linked to an earlier reported cryptominer (XMRig or Zephyr) attack kill chain. While investing we also were able to confirm that the malware was blocked by the organizations EDR during the final stages of the miner attack.
Back in October 2024, Azerbaijan’s CERT also reported about uncovering and disclosing information about a large-scale international cryptocurrency mining scheme, which they named “Universal Mining.” Our blog will cover some of the TTPs observed and we share hunting queries for the TTPs observed during our investigation that still holds true for some variants reported from as far back to at least October 2024.
Technical Details
We tracked a list of known IOC clusters to understand the global prevalence of this campaign, first leveraging different intel sources and telemetry. Below is a map of the top countries hit by the worm attempting to deliver the cryptominer.
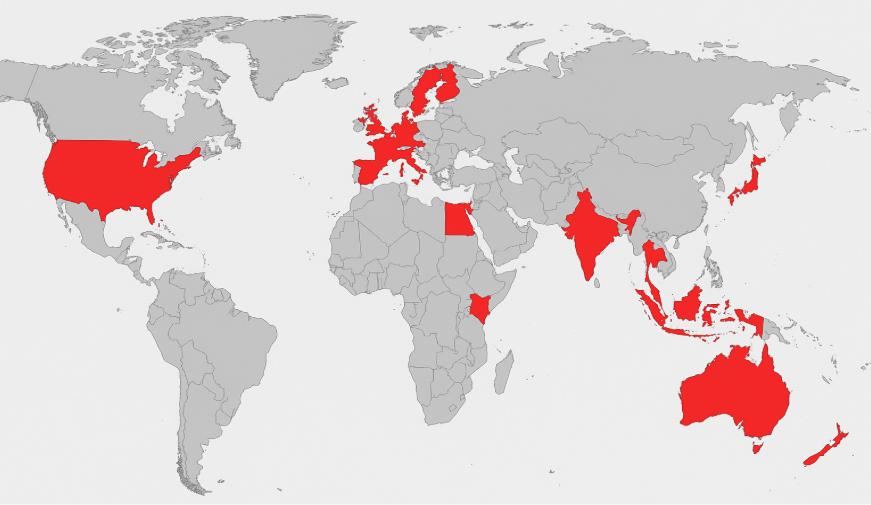
Fig. 1: Geographical distribution of infected USBs leading to Zephyr infection in last 12 months.
We have been able to identify that the following have been some of the top industry sectors affected by this cryptomining attack:
- Financial Institutions
- Educational Institutes
- Healthcare
- Manufacturing
- Telecom
- Oil & Gas
We have determined that the infection starts with execution of a VB script file from a USB drive (using file name that starts with x and random 6 digits) from a folder name “rootdir” as shown below.
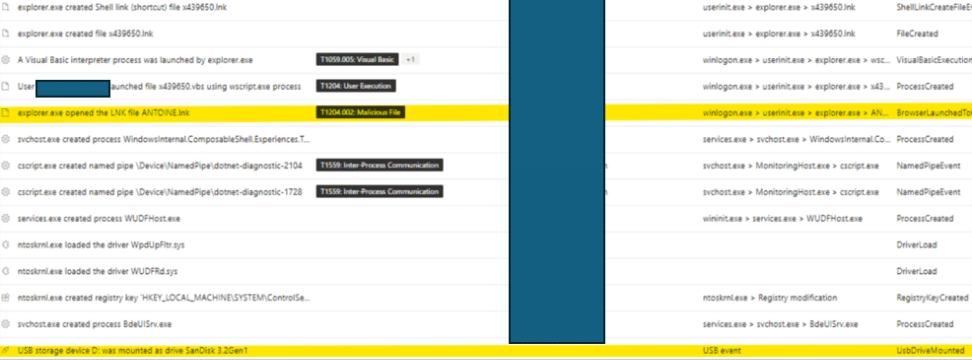
Fig. 2: Infection spreading from USB drive
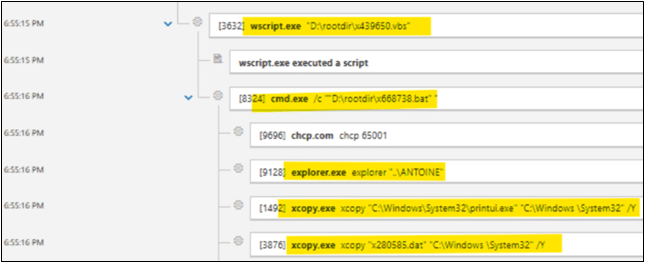
Fig. 3: Xcopy used for file moving and file naming pattern of VBS & BATCH file seen
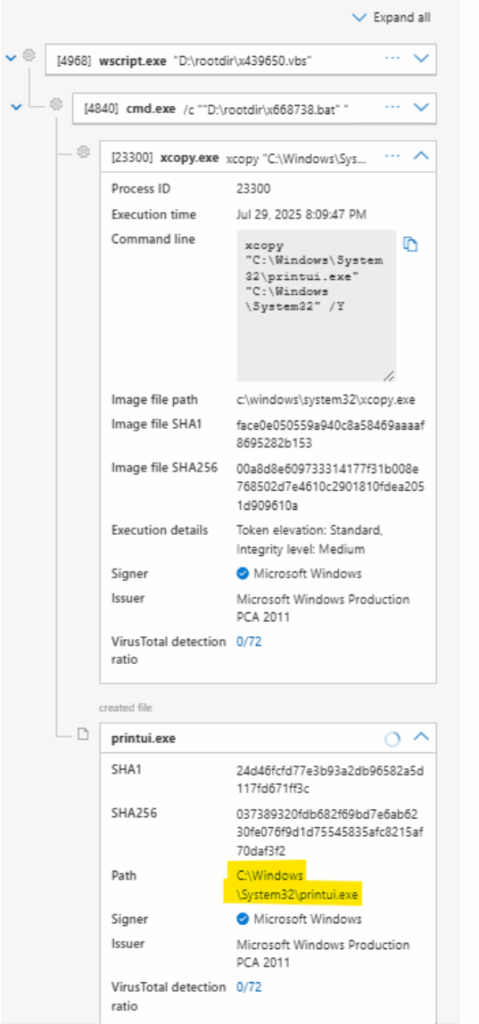
Fig. 4: Another view from Microsoft Defender EDR showing similar behavior
This is followed by execution of a batch file via Command Prompt, as a child process of wscript (whose name is similar to the VBScript file). Note the launch of xcopy.exe to copy printui.exe from %system32% folder to newly created folder under the path – C:\Windows \System32 (note the extra space here (C:\Windows \). Then again xcopy.exe is used to copy a random file named .dat file into this newly created folder path which is later used for DLL side loading of malicious printui.dll as shown below.
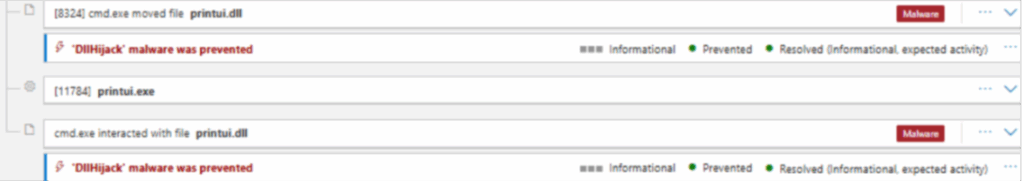
Fig. 5: Folders used for malicious code
Below we can see blocking of printuil.dll that has the code to download cryptominer.
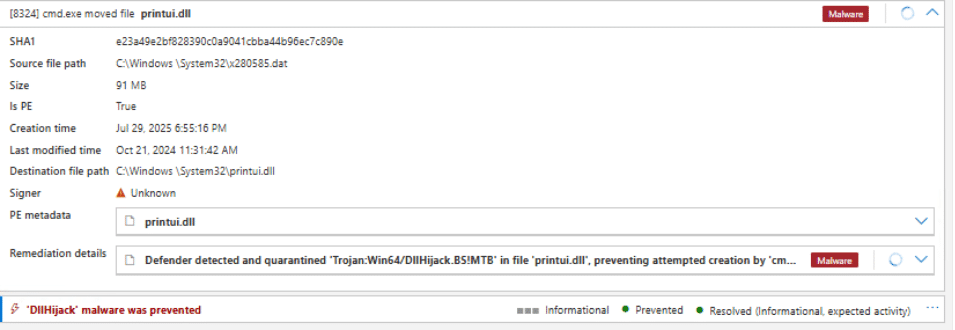
Fig. 6: EDR blocking a key component in the cryptominer’s download chain
Threat Hunting Query
The below threat hunting queries can be used to spot USB spreading and early TTPs related to Zephyr Crypto campaigns:

Upon testing the queries we were able to detect related TTPs as shown below:
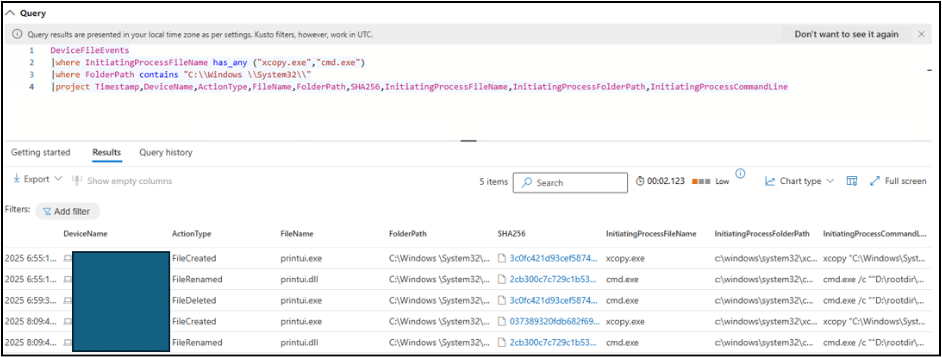
Fig. 7: Threat hunting query detecting anomalies in the infected environment
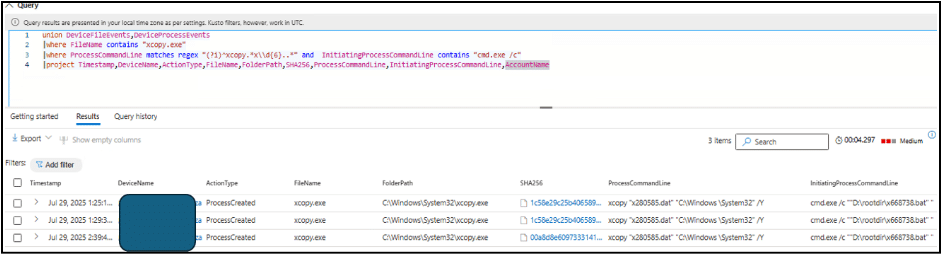
Fig. 8: Threat hunting query detecting anomalies in the infected environment
Conclusion
The continued prevalence of cryptomining attacks originating from infected USB drives, even in mid-2025, serves as a powerful reminder of a fundamental security challenge. Organizations that don’t regularly review and enforce their USB usage policies remain vulnerable not only to malware, but also to insider threats.
To effectively mitigate these risks, a multi-layered approach to security is essential. For years CISA has recommended enforcing a policy on limited USB device usage, especially in environments handling sensitive data or critical infrastructure. This starts with foundational security practices and extends to more advanced protections.
Key Recommendations to Protect Your Network
- Disable Autorun and Autoplay: The most critical first step is to prevent drives from automatically running executable code when they are connected. You can enforce this across your network using Group Policy or by adjusting registry settings.
- Implement Device Control: Go beyond disabling autorun. Block the use of untrusted or unsigned processes that attempt to run from USB devices. This can prevent malicious scripts and executables from ever launching.
- Harden Endpoint Security: Implement robust endpoint detection and response (EDR) solutions that can block potentially obfuscated scripts and monitor for anomalous behavior. Configure your security policies to block executable files from running unless they meet specific criteria, such as being on a trusted list.
- Protect Critical System Processes: Use security controls to block malicious attempts to steal credentials from the Windows Local Security Authority Subsystem (lsass.exe), a common target for attackers looking to escalate privileges.
- Enforce Physical Security: Don’t forget about the physical world. Use physical security measures to prevent unauthorized USB devices from being connected to critical systems. For example, using write-protected USB drives and locking ports can be highly effective.
Learn more about how CyberProof Advanced Threat Hunting capabilities can help your organization identify undetected threats inside your network.













