
Case Study – Energy
Threat-led security transformation improves resilience for a multinational energy company
DOWNLOAD THE PDFAbout the client
The client is a multinational energy company engaged in producing natural gas liquids and petrochemicals. The company has operations in multiple locations around the world.
The client’s challenge
In recent years, energy companies have become a top target for state-sponsored groups and ransomware operators. Incidents such as the Colonial Pipeline attack have underscored the critical vulnerabilities in energy infrastructure and the potential for widespread disruption. The client wanted to ensure that they had the necessary safeguards in place to protect their organization.
The client recognized that their reliance on legacy on-premises systems created blind spots across both IT and OT environments. Combined with rising attrition of skilled staff, this increased the risk of undetected exposure to ransomware, supply chain compromise, and operational disruption. The Russian-Ukrainian conflict heightened concerns around state-sponsored attacks targeting energy infrastructure, while ransomware groups continued to exploit misconfigured systems and unmonitored endpoints.
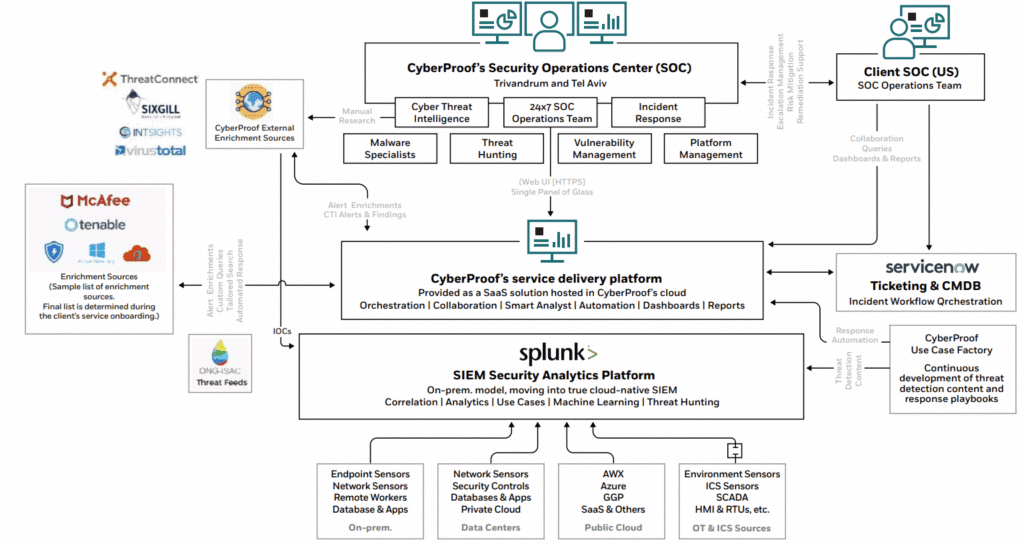
As a result, the business was looking for a managed cybersecurity partner to help them make the shift to a cloud-native security stack using Microsoft Sentinel and Defender and provide support with advanced Managed Extended Detection & Response (MXDR) cybersecurity services, as well as with threat intelligence and threat hunting services.
Benefits
- 24/7 security monitoring and proactive threat intelligence .
- Reduced ransomware exposure through continuous threat hunting and credential monitoring.
- Improved resilience of critical OT operations by aligning monitoring with adversary behaviors targeting the energy sector.
- Faster containment of incidents, reducing mean time to respond (MTTR) and limiting business disruption.
- Operational cost savings by consolidating legacy tools under a single Managed XDR service.

Our solution
CyberProof delivered a threat-led transformation, migrating the client to Microsoft Sentinel and Defender to replace legacy systems and provide continuous visibility across IT and OT.
Threat intelligence-driven monitoring was aligned to the client’s attack surface, correlating adversary behaviors against real exposures. Asset-based visibility highlighted risks across critical OT, cloud, and third-party connections, enabling remediation before attackers could exploit them.
By mapping defenses to MITRE ATT&CK techniques used by energy-focused threat groups, CyberProof ensured detections were relevant, proactive, and continuously improved.
Results
By shifting from a technology-first to a threat-led security model, the client gained visibility into its most critical exposures, and aligned defenses with the adversaries most likely to target the energy sector. This approach not only improved incident response times but also strengthened resilience against both state-sponsored and criminal cyber threats.
Speak with an expert
Explore how CyberProof can help you anticipate, prevent, and mitigate ever-evolving cyberattacks in hybrid and cloud-native environments.






