Executive Summary
A new security vulnerability, publicly identified as CVE-2025-56383, has emerged concerning the popular text editor Notepad++. Initially reported as a “DLL hijacking” issue, our lab analysis confirms that the issue is, more precisely, a severe case of plugin replacement and abuse that leads to arbitrary code execution within the notepad++.exe process. While not a classic Windows DLL search-order hijack, the operational impact is just as serious, allowing an attacker with local write access to the plugin directory to silently run malicious code.
This blog post breaks down the technical details of the vulnerability—which we successfully reproduced against Notepad++ v8.8.5 by replacing a legitimate plugin DLL—and, more importantly, provides immediate, actionable defensive strategies. For defenders, simply patching the application isn’t enough; the core defense must focus on removing the write opportunity to the plugin folders and implementing high-fidelity detection that correlates file tampering with subsequent DLL loading.
Read on to understand the nuance of this exploit, why it matters for your environment, and how to use the provided security queries and recommendations to lock down your systems and detect this threat before it can be exploited for persistence or lateral movement.
Background
After CVE-2025-56383 was been reported as a “Notepad++ DLL hijacking” issue, CyberProof researchers reproduced the public PoC against Notepad++ v8.8.5: replacing a plugin DLL (for example NppExport.dll) in the Notepad++ plugin folder caused notepad++.exe to execute code when the plugin loaded (the PoC used a benign message box). Researchers onbserved that the behavior is real, but it is more accurately described as plugin replacement / plugin abuse (a plugin file was intentionally loaded by the application), not necessarily a canonical Windows DLL search-order hijack. The defensive response should focus on removing the write opportunity and on high-fidelity detection of DLL tampering + load.
DLL hijacking (or binary planting) is a long-standing Windows weakness where applications load DLLs by filename from unsafe or attacker-controlled locations. In this PoC, a plugin DLL (e.g., NppExport.dll) was replaced with a proxy DLL that forwards legitimate exports while executing attacker code at load time. Because the proxy preserves expected functionality, the application appears normal while running attacker code inside notepad++.exe.
It is important to clarify:
- Plugin replacement/abuse – Notepad++ is designed to load DLLs from its plugins folder, so any DLL dropped there runs.
- Not a classic search-order hijack – there’s no unsafe fallback resolution like LoadLibrary(“foo.dll”) hitting %PATH% or the current working directory.
- Requires local write access – exploitation is only possible if plugin folders are writable (via local compromise, misconfigured ACLs, or elevated privilege
Technical Details
Test setup (defender-safe): air-gapped Windows VMs with snapshots; no network connectivity to production; benign DLL stub used to demonstrate load (a harmless UI message box). No exploit or payload code was run on production systems.
Observed behavior:
- The original plugin DLL was preserved/renamed (e.g., old.dll) and a new DLL placed at the plugin filename.
- On Notepad++ start, the new DLL executed and displayed the benign proof-of-execution dialog while the app continued to function.
- Telemetry captured the chain: file create/modify/rename to notepad++.exe image load to DLL execution.
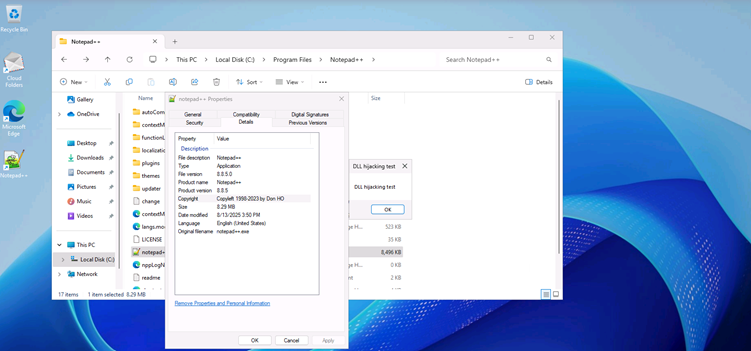
Fig. 1: Benign message box shown by the replacement NppExport.dll when loaded by Notepad++ v8.8.5
Why this matters:
- Attacker requirement: local write access to Notepad++ plugin folders (could be low-privilege account, malicious MSI, or other local compromise).
- Impact: arbitrary code runs in notepad++.exe context — usable for persistence, credential theft, lateral movement, or escalation when combined with other flaws.
- Stealth: because the proxy DLL forwards legitimate exports, user-visible app behavior remains normal and casual detection is unlikely.
Detection
KQL:
Notepad++ loading a DLL from the NppExport plugin folder when launched at a non-elevated integrity level
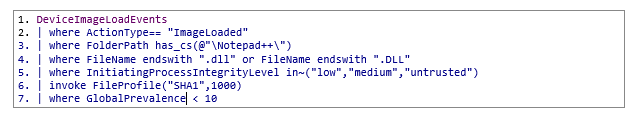
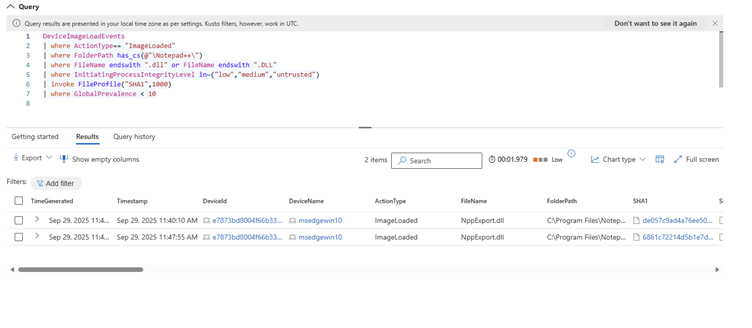
Fig. 2: Hits for Notepad++ loading a DLL from the NppExport plugin folder when launched at a non-elevated integrity level
CrowdStrike:
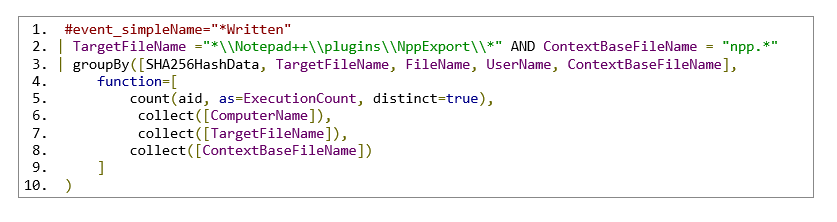
S1:
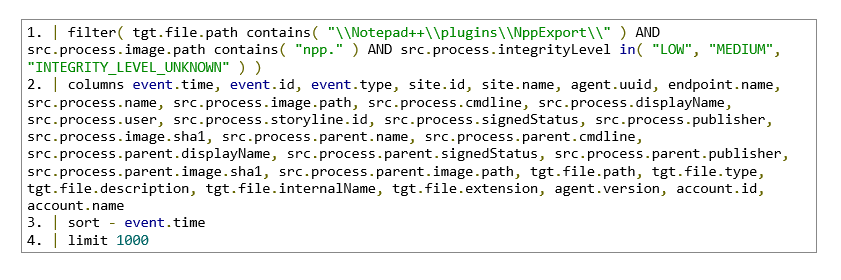
Please note these queries give can give false positives, so please check the reputation NppExport.dll hashes. You can reduce FPs by:
- Correlating with file writes (require a DeviceFileEvents record within 2–5 minutes before load).
- Baseline plugin DLL hashes/sizes; escalate only when unknown or significantly different.
- Exclude trusted installer/updater processes (msiexec, Intune, SCCM, TrustedInstaller).
- Prioritize cases where the writer was non-elevated / low-integrity.
Defensive Recommendations
To effectively mitigate this risk, defenders must focus on removing the opportunity by hardening the environment with stringent ACLs, robust File Integrity Monitoring (FIM), application control measures, and centralized software installation policies. Furthermore, deploying high-fidelity detection is essential. You must correlate file write events to subsequent DLL loads and flag hash anomalies to catch stealthy proxy DLLs that preserve application functionality.
Start your defense immediately by:
- Removing the opportunity across the environment (ACLs, FIM, app control, centralized installs)
- Deploy high-fidelity detections that correlate writes to loads and check hash prevalence
- Running the provided MDE query to surface any rare or unauthorized plugin DLL loads
Detailed recommended actions include:
- Restrict plugin folder writes: Set NTFS ACLs on C:\Program Files\Notepad++\plugins\ so only Administrators and SYSTEM (and your management service account) have write permissions. Use deployment tooling (SCCM/Intune) to perform updates as SYSTEM.
- File integrity monitoring (FIM): Add plugin folders to FIM and alert on new/modified/renamed DLLs. Maintain a small allowlist of known plugin hashes.
- Correlated detection: Deploy the named EDR rules and only escalate when write to load correlation and hash anomalies are present.
- App control: Where feasible, use AppLocker/WDAC to restrict which DLLs notepad++.exe can load (e.g., only vendor-signed DLLs).
- Centralize installs: Disallow local installs; deploy Notepad++ centrally via SCCM/Intune and block local installers.
- User/ops process: Provide an internal process for plugin requests so users don’t install unsigned plugins ad-hoc. Educate staff about the risk of running untrusted installers.
Conclusion
The vulnerability identified as CVE-2025-56383 confirms a critical security pattern: plugin replacement/abuse in Notepad++ that leads directly to code execution. This threat is operationally viable wherever plugin directories are writable, making it a serious concern for enterprise security. Crucially, the correct defensive response extends far beyond simply patching a single application.
CyberProof Threat Hunters use advanced analytics and deep security intelligence to actively search for the subtle indicators of compromise that static detections miss. CyberProof can help organizations like yours to:
- Validate and tune the high-fidelity detection rules needed to catch complex attacks like CVE-2025-56383.
- Proactively hunt for anomalous DLL loads, file modifications, and suspicious process behavior across your entire environment.
- Establish baselines for legitimate plugin hashes to dramatically reduce false positives and accelerate your incident response.
Learn more about how CyberProof can strengthen your security posture and transform your threat detection capabilities.










