Today’s Cybersecurity Dilemma: Analyzing over 100,000 security incidents daily from more than 150 distinct threat actors
The Challenges:
- Security teams struggle to keep up with threats
- Uncertainty about relevant and significant threats
- Blind spots from ineffective, scattered cybersecurity tools

The Solution: Defend Against the Threats That Matter Most
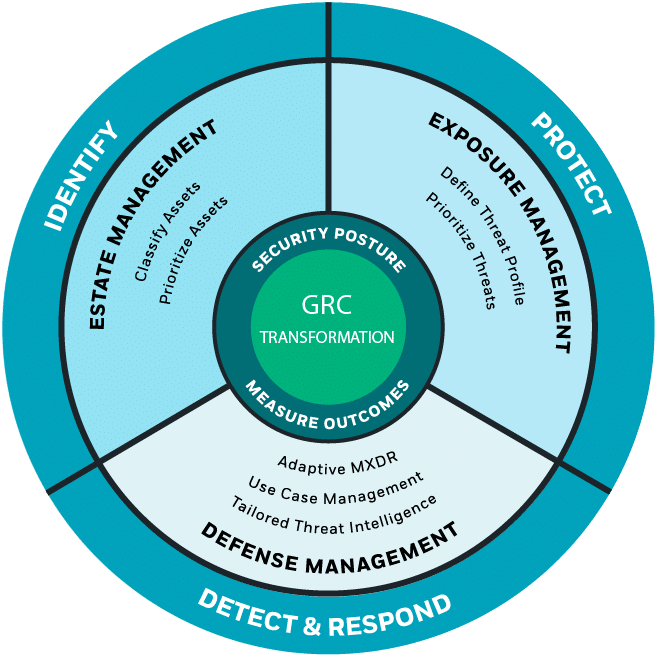
CyberProof provides an integrated threat-led platform that combines:
- Estate (Asset) Management: Tag, classify, and prioritize known and unknown assets to understand your exposure – continuously
- Exposure Management: Focus on relevant threats using CTEM and ASCA frameworks – continuously
- Defense Management: Optimize detection and response playbooks – continuously
- Resulting in GRC Transformation: Mitigate Global Risk, Define Business Outcomes & ROI, Mature Security Posture
SecOps & Risk Mitigation
CyberProof uses OSINT and threat intelligence feeds for visibility into threats.
CyberProof’s adaptable playbooks address continuously evolving threats with updated strategies.
Professionals manage sophisticated networks, leveraging experience to counter advanced threats.
Professionals manage sophisticated networks, leveraging experience to counter advanced threats.
24/7 global SOC support ensures incident response with guaranteed SLA.
24/7 global SOC support ensures incident response with guaranteed SLA.
CyberProof develops recovery plans, restoring capabilities after a cyber incident.
Classify and manage enterprise assets, understanding risks and data sensitivity.
Non-destructive tests uncover potential exploits in assets and applications.
Mitigate security issues early with CyberProof’s training and awareness programs.
Rigorous security assessment for on-premise and cloud applications to ensure protection.
IAM manages user access, monitors for anomalies, ensuring security.
Cloud First approach ensures compliance and security within cloud environments.
Managed service for SIEM, EDR, MXDR, and threat intelligence solutions.
Identify, assess, and mitigate security vulnerabilities through regular scanning.
Partners
See all partners“Today I have complete visibility into the entire environment, in real time”
Jamil Farshchi | Equifax CISO
CyberProof CTEM
CyberProof’s CTEM platform, powered by Interpres, is able to continuously identify, assess, and prioritize risk, while enhancing defense services like MDR, Vulnerability Management and Use Case Management to address evolving threats. Take proactive steps to fortify your security today!
Threat Alerts
UNC6040 Vishing Campaign Targeting Cloud Data
Researchers are tracking UNC6040, a financially motivated threat group using voice phishing to target Salesforce instances for data theft and extortion. By posing as IT support, attackers trick employees into authorizing a malicious Data Loader app, exfiltrating sensitive data via modified versions, sometimes named “My Ticket Portal,” and using VPN IPs and phishing panels for credential harvesting and lateral movement across platforms like Okta and Microsoft 365, with links to “The Com” collective.
Extortion may follow months after breaches, with attackers claiming ties to ShinyHunters. Recommendation includes enforcing least privilege, restricting app access, IP-based controls, enhanced monitoring, and universal MFA to counter these social engineering tactics.
Spike in Deepfake Activity Drives Increase in BEC and Social Engineering
A sharp rise in deepfake-driven fraud has been observed in early 2025, with documented financial losses exceeding $200 million across sectors. These incidents increasingly involve advanced real-time voice and video impersonation techniques during virtual meetings, authentication steps, and onboarding workflows. In nearly half of all known cases, attackers leveraged manipulated video—either pre-recorded or generated live—to deceive victims, often bypassing identity verification systems.
This escalation continues a broader trend identified over the past three years, with deepfake incidents growing by over 2100% since 2022. Threat actors are incorporating deepfake content into social engineering campaigns, business email compromise (BEC), and impersonation-based access attempts, reflecting the growing use of synthetic media in coordinated intrusion activity.